| E-Suite M365 Enterprise |
E-Suite IP |
E-Visor Enterprise |
|
|---|---|---|---|
 |
|||
| Analytics Services Collects, parses, and correlates M365 logs over 160+ data points |
✔ | ✔ [Partial: MIP/DLP reports] |
✔ |
| SIEM export Send data to specific security logs technology SIEM |
✔ | ✖ | ✔ |
 |
|||
| Secure collaboration and access to sensitive files Optimized process based on workflows |
✔ | ✔ | ✖ |
| App integration Unstructured data encryption and decryption via API |
✔ | ✔ | ✖ |
 |
|||
| Inventory Extend Microsoft Azure Information Protection (MIP), providing content inventory across both Cloud and On-Premises |
✔ | ✔ [Partial: NFS, OD4B, SP, SPO] |
✖ |
| Data-at-rest protection Scanning and encryption capabilities to analyze and protect sensitive data |
✔ | ✔ [Partial: NFS, OD4B, SP, SPO] |
✖ |
| Alerts & Notifications Security alerts workflow for optimized approvals and actions |
✔ | ✔ [Partial: MIP/DLP notifications only] |
✔ [Partial: Email notifications only] |

New policies to arm your organization with the tools it needs to achieve your security goals.
Analytics
Tested in real scenarios
- Track user activity
- Audit admin actions
- Cyber security
Data Governance
Integrated information collaboration lifecycle
- Support user lifecycle
- Secure external collaboration
- Application integration
Optimized Operations
Intelligent alerting and notification services
- Cyber Security
- Compliance
- Productivity
Give your organization the power to discover, govern, protect, and report on your most sensitive information across Microsoft 365 services. E-Suite is a collection of four services, E-Visor, E-Cryptor, E-Inspector and E-Vigilant designed to help you discover, audit, and govern your most sensitive information and resources:
Investigate Users & Resources
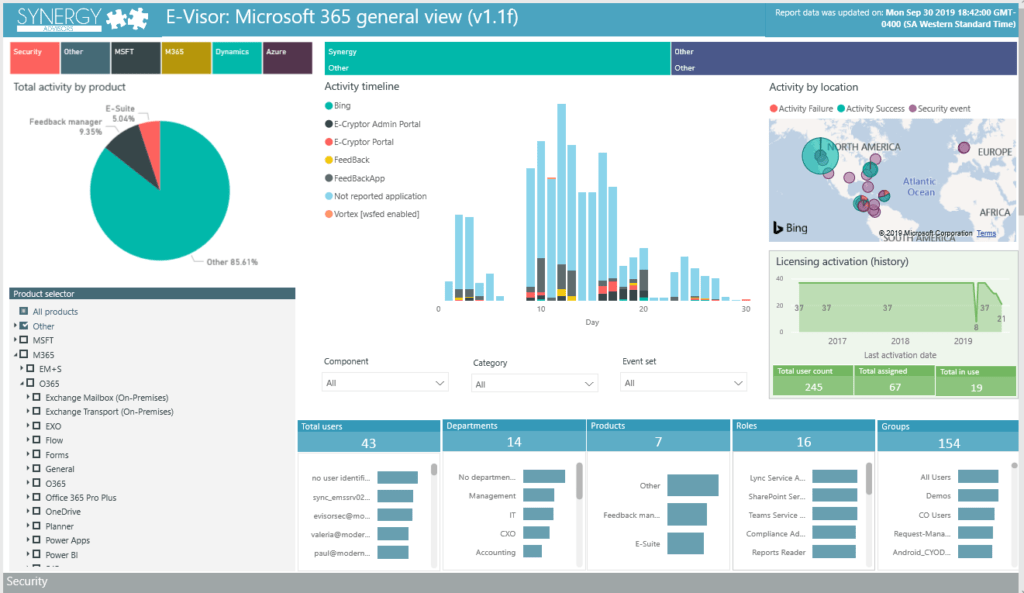
Collects, parses, and correlates logs across Microsoft 365 to give you:
- A full view of your cloud identities, devices, apps, and files
- Log automatization across multiple sources, correlated with Active Directory, geolocation, and other sources
- Proactive response to security threats
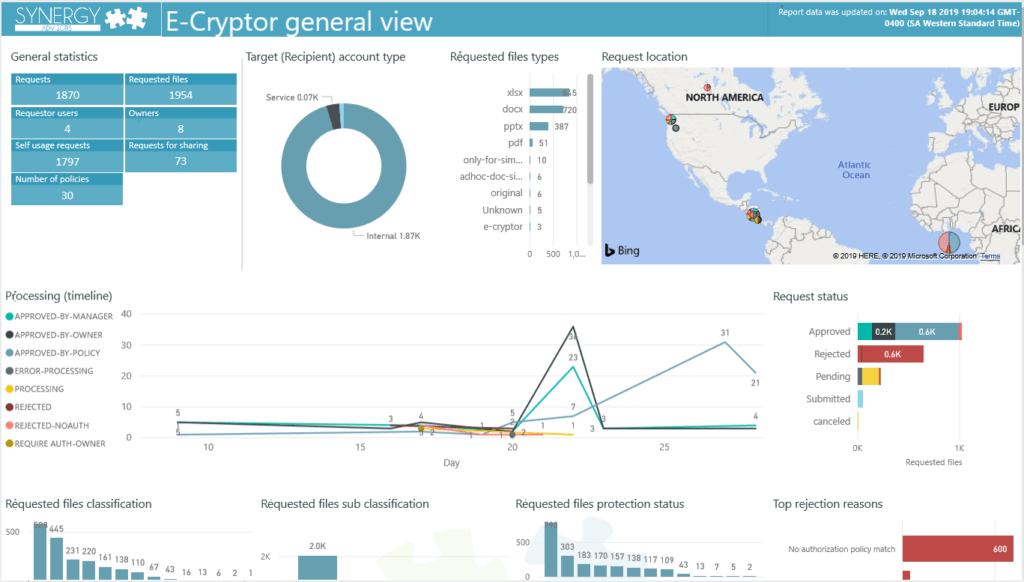
Improve Data Governance
Augment your Microsoft Information Protection (MIP) encryption policies to enable advanced scenarios:
- Transfer the ownership files
- Securely share encrypted files with internal and external audiences
- Automatically encrypt and decrypt files as they enter and leave server and service applications
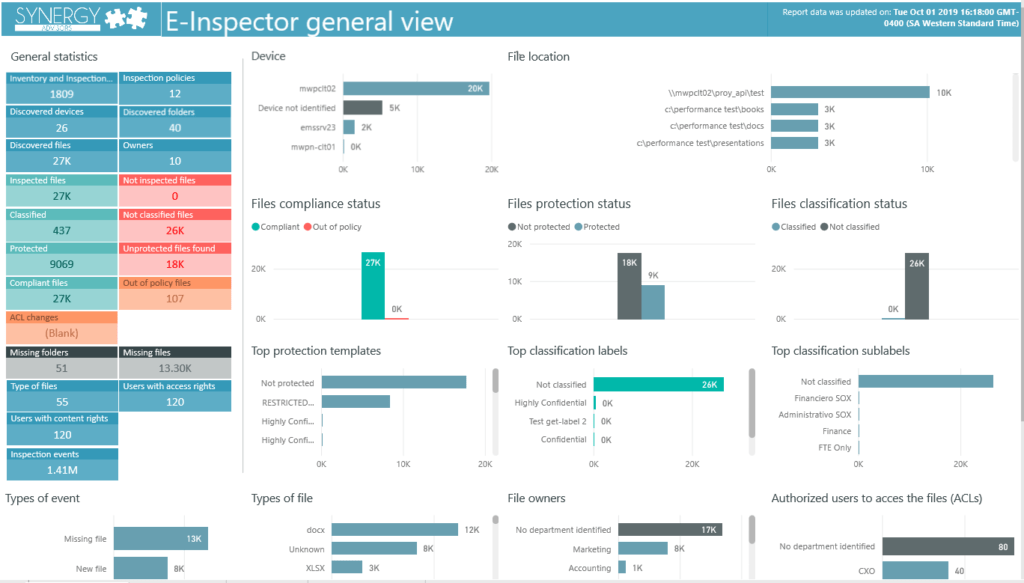
Inspect and Protect Information
Scans data at rest to audit, discover, and secure sensitive information at rest:
- Scan sensitive information on files stored in NAS providers and SaaS applications
- Discover and act on files based on metadata attributes
- Alerting, notifications, and workflows in near real-time
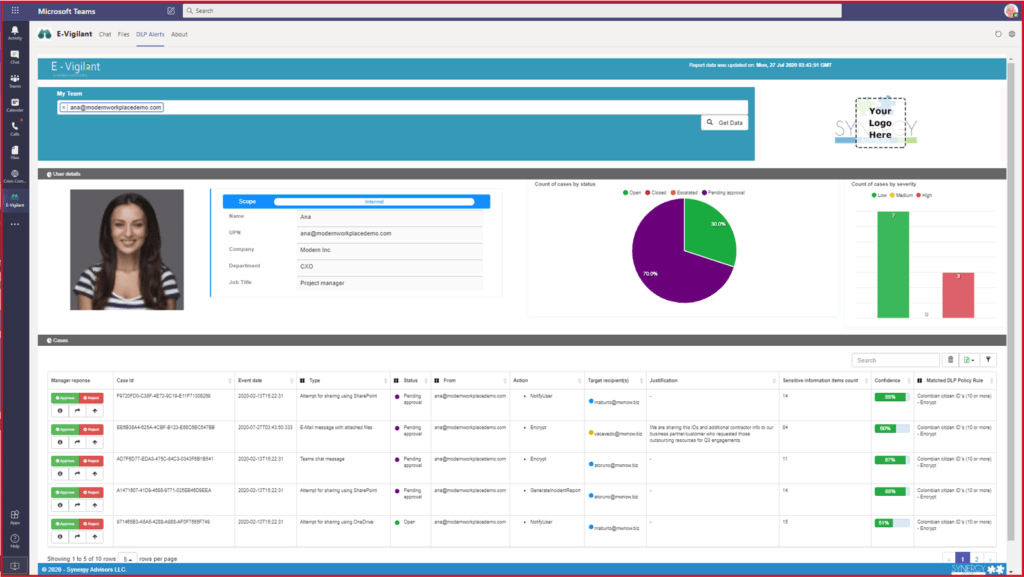
Alerts, Notifications, and Responses
Intelligent alerts and notifications for Cyber Security, Compliance and Productivity
- Route DLP policy violation to the actors with the requisite context, reducing false positives and surfacing high-impact cases
- Alert end users to viruses and malware found and recommend or automate next steps
- Alerting, notifications, and workflows in near real-time
Highlight by interest area:
Analytics
Data Governance
Optimized Operations
Request more information
Or you may reach us at (+1) 425-689-3310
©2020 Synergy Advisors LLC. ALL RIGHTS RESERVED.