My personal information
[devvn_ihotspot id="3178"]
| Element | Available Values | Explanation | User benefits | Administrator benefit |
|---|---|---|---|---|
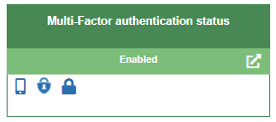 | A. Disabled [Red] B. Enabled [Orange] C. Enabled [Yellow] D. Enabled [Green] | A. Disabled - Red: The user has not registered any MFA authentication methods B. Enabled - Orange: The user has only configured one (1) MFA authentication method C. Enabled - Yellow: The user has registered two (2) or more MFA authentication methods D. Enabled - Green: The user has registered three (3) or more MFA authentication methods Note: Available authentication methods may include Microsoft Authenticator, Voice Call, and Text Message. | You can quickly verify the status of the MFA feature for your account and compare that status to Microsoft best practices. You can use the click-through links to register for MFA or change the authentication methods currently configured for your use. MFA provides an extra layer of security for the user account when logging into Office 365 and cloud applications. E-Visor for Teams helps centralize and display your current MFA configuration. | E-Visor for Teams provides end users with the ability to quickly see whether they have registered for MFA, what authentication methods they have configured, and how that configuration compares to Microsoft best practices, using a color-coded display. If users need to make a change to their MFA configuration, they can register for MFA or modify their authentication methods with the link provided. |
 | A. Disabled [Red] B. Enabled but not registered [Orange] C. Registered [Green] | A. Disabled: Self-service password reset has been disabled by the administrator for the user. B. Enabled but not registered: Self-service password reset is enabled for the user by the administrator; however, the user has not configured an authentication method. C. Registered: The user has registered the authentication methods required for self-service password reset. NOTE: Available methods could be: Mobile App Code, Mobile Phone, Mail | You can quickly verify the status of the SSPR feature for your account and, if configured, view which authentication method you have configured. You can use the click-through links to register for SSPR or change the authentication methods currently configured for your use. SSPR enables a user to change their password, even if the user cannot input the current password, provided the user passes a secondary authentication control. | E-Visor for Teams provides end users with the ability to quickly see whether their account is enabled for SSPT, if they have registered for SSPR, and what authentication methods they have configured, using a color-coded display. If users need to make a change to their SSPR configuration, they can configure SSPR or modify their authentication methods with the link provided. |
| - | - | You can easily link directly to the portal to change your password in response to expiry or potential security concerns. E-Visor for Teams directly links you to the correct portal, without the need to generate a ticket to the help desk. | By consolidating links to manage user passwords, this functionality saves users time through the centralization of important portals that they may not use with enough regularity to remember. Surfacing these links in a highly visibile location encourgages the usage of the change password functiaonlity, leading to more frequent use of the tool, fewer support tickets, and more empowered end users. |
|
| - | - | This option automatically and immediately logs your user account out of all devices and cloud applications. You may want to log out of all locations and apps if you notice a succesful sign-in event for a sign-in you know you did not initiate, such as a from a stale device or unusual location. | Users can proactively respond to anomalous sign-in usage, usage from stale devices, or other security issues they may notice from their identity or device data. Your users have additional context to their activities that, in some cases, enable them to spot unusual activitiy. This option also provides a quick response to a potential security incident that they can initiate while waiting on a more permanent solution from your support team. | |
| - | - | This button enables you to view personal information, sourced from your user account, and validate if it is correct. Your organization may allow you to edit the values of some or all of these parameters | This link provides your users visibility into their personal information, as sourced from Active Directory. They can report a change or, if configured, make a change to their information directly in the portal. |
My sign-ins
[devvn_ihotspot id="4065"]
[devvn_ihotspot id="4088"]
| Element | Available Values | Explanation | User benefits | Administrator benefit |
|---|---|---|---|---|
 | 1 | Total login attempts over the last 7 days. | This box shows your total login attempts to cloud applications or managed devices over the last 7 days. | Presenting users with an easy way to review and filter where, when, and how their identities are used empowers those users to see if their account is at risk. The context a user can add to the usage of his or her own account increases the probability that a malcious attack attempt is discovered and increases the speed at which the attack is discovered, thus potentially reducing the surface area of the attack. If an end user notices anamolous login attempts, the user can take immediate and proactive action to log out of all applications and devices and change the password, straight from the E-Visor for Teams app. Then the user can reach out to support to provide further remediation. |
 | 1 | successful logins over the last 7 days. | This button filters your login attempts to only show successful logins over the last 7 days. | |
 | 1 | Failed logins over the last 7 days. | This button filters your login attempts to only show failed logins over the last 7 days. | |
 | 1 | Logins on a Windows device over the last 7 days. | This button filters your login attempts to show only logins on a Windows device over the last 7 days. | |
 | 1 | Logins on an Android device over the last 7 days. | This button filters your login attempts to show only logins on an Android device over the last 7 days. | |
 | 1 | Logins on a MacOS device over the last 7 days. | This button filters your login attempts to show only logins on a MacOS device over the last 7 days. | |
 | 1 | Logins on an iOS device over the last 7 days. | This button filters your login attempts to show only logins on an iOS device over the last 7 days. | |
 | 1 | Logins on a Linux device over the last 7 days. | This button filters your login attempts to show only logins on a Linux device over the last 7 days. | |
 | 1 | Another operating system over Login over the last 7 days. | This button filters your login attempts to show only logins on a from a device with another operating system over the last 7 days. | |
 | 1 | Logins that prompted an MFA authentication over the last 7 days. | This button filters your login attempts to show only logins that prompted an MFA authentication over the last 7 days. | |
 | 1 | Logins where a conditional access policy was applied over the last 7 days. | This button filters your login attempts to show only logins where a conditional access policy was applied over the last 7 days. | |
 | 1 | Risky logins over the last 7 days. | This button filters your login attempts to show only risky logins over the last 7 days. | |
 | Device Logo | N/A | This column graphically shows you the operating system of the device on which the sign-in attempt occurred. | |
 | Date | N/A | This column shows you the date on which the sign-in attempt occurred. Optionally, you can sort the sign-in data by date. | |
 | Time | N/A | This column shows you the time at which the sign-in attempt occurred. Optionally, you can sort the sign-in data by time. | |
 | A. Failure B. Success | A. Failure: The login attempt failed; the user was unable to access the application or resource B. Success: The login attempt was succesful; the user was able to access the application or resource | This column shows you whether the sign-in attempt was successful and the user could access the location, application or resource, or if the sign-in attempt was unsuccesful and the user could not access the location, application, or resource. Optionally, you can filter the table information by successful or failed attampts. | |
 | N/A | Risk state represents the probability that a login is compromised. For example, logins from an unknown or uncompliant device are identified as riskier than logins from a known and compliant device | This column displays how risky the device is on which the login attempted occurred. Optionally, you can filter the table information by risk state | |
 | A. None B. Low C. Medium D. High | The login conditions are analyzed taking into account factors such as Device, Location, Recent User Activity, OS, among others, and a score is generated that determines the level of risk that might exist. This risk assessment makes decisions for that login such as Allow, Allow with Restrictions, or Deny Access. | The end user can identify the level of login risk they had in each of their logins, being able to infer and review when there was a risky login and when not. | |
 | A. None B. low C. Medium D. high | The risk of login, represents the possibility that this login may be at risk of being compromised. Factors such as Device, Location, Recent User Activity, OS, IP, Network, among us with artificial intelligence are analized to locate that login in any of the categories according to the results obtained A. None: No risks associated with the logins of the user. B. Low: Indicates that the risk associated with the logon is Low. C. Medium: Indicates that the risk associated with the sign is Medium. The logins of a Medium risk to the resources of the Organization may be locked or in default thereof, to apply for a two-Factor authentication [MFA] prior to allow access. D. High: Indicates that the risk associated with the logon is High. The logins of High risk to the resources of the Organization may be blocked by the security of such assets. | The end user can identify what level of login risk they have in real time at the time of generating the login, being able to infer and review when there was a risky login and when not. | |
 | A. unfamiliarFeatures B. anonymousipRiskEvent C. malwareRiskEvent D. impossibleTravelRiskEvent E. leakedCredentialsRiskEvent F. unfamiliarLocationRiskEvent | A. unfamiliarFeatures: Registers a login from a location that is unfamiliar, based on your previous activity. For example, this could include a login from a different country other than your residence. B. anonymousipRiskEvent: Registers a login from an IP address that is classified as Anonymous. Typically anonymous IPs are used to hide the traffic source and are therefore classified as risky. C. malwareRiskEvent: Registers a login from a device infected with malware or viruses. D. impossibleTravelRiskEvent: Registers a login from a location too far away from the previous login location to travel to in the amount of time between those login attempts. E. leakedCredentialsRiskEvent: Registers a login with the leaked credentials of the user. This usually occurs because the user has a password that is compromised or easily stolen by malicious spammers. F. unfamiliarLocationRiskEvent: Registers a login from a location previously not used by the user. For example: this could inlcude a login from a different country other than your residence. | The possibility of having in seconds, the ability to visualize what type of risks I am subjected to, if I am on a device with malware, if the location is not reliable, if a login was generated in a location far from the usual one, all this allows giving context to the end user and indicate what type of risks it has in order to take action | The possibility of having in seconds, the ability to visualize what type of risks I am subjected to, if I am on a device with malware, if the location is not reliable, if a login was generated in a location far from the usual one, all this allows giving context to the administrator, so that no action is taken on it, it can generate conditional access rules for those users, request MFA, generate a white list of IPs that we consider safe, and gradually mitigate these types of risky events |
 | Operating system name | This column indicates the operating system of the device on which the sign-in attempt occurred. | Operating system details provides necessary context as you evaluate a specific sign-in event. You can also easily surface malicious sign-in attempts from device types that you do not use. | Sign-in details provide your users with the necessary context to evaluate their sign-in attempts. This information helps users discover specific sign-ins that they want to investigate further or easily surface malicious sign-in attempts. |
 | N/A | This column indicates the application to which the sign-in attempt occurred. | Application name provides necessary context as you evaluate a specific sign-in event. You can also easily surface malicious sign-in attempts to applications that you do not use. | |
 | N/A | To generate a login each user has two ways, mobile applications - desktop clients or access them through a browser, this column tells us if the login was from a mobile app, desktop client or from a browser . | Application type provides necessary context as you evaluate a specific sign-in event. You can also easily surface malicious sign-in attempts from applications or application versions that you do not use. | |
 | N/A | Device name identifies a particular physical hardware device. The name may be assigned by the device owner or by the operating system. | Device name provides necessary context as you evaluate a specific sign-in event. You can also easily surface malicious sign-in attempts from devices that you do not recognize. | |
 | N/A | This table displays the devices that were enrolled as corporate through Intune, applying the conditional access policies to apply MFA. | The user can know if their device is being managed by their organization and can identify that they are securely accessing those allowed by their organization. | The administrator can visually validate that the enrolled devices are in compliance with the policies set in Intune. |
 | N/A | IP address indicates the location from which the sign-in attempt occurred. | IP address provides necessary context as you evaluate a specific sign-in event. You can also easily surface malicious sign-in attempts from IP addresses that you do not use. | Sign-in location details help users discover specific sign-in events. They also enable users to easily surface potential malicious login attempts from unfamiliar locations. |
 | N/A | These columns indicate the physical location from which the sign-in attempt occurred. | Location details provides necessary context as you evaluate a specific sign-in event. You can also easily surface malicious sign-in attempts from locations that you have not recently logged in from. | |
 | N/A | |||
 | N/A | |||
 | A. Single factor authentication B. Multi factor authentication | This column tells us when the user should have used one or more authentication methods according to the policies and conditional access rules that have been associated with the user. | The end user will be able to identify on which applications and devices MFA is requested and in which they can use a single authentication to understand the behavior of their different logins. | The administrator will be able to understand when the MFA applies to users and when it does not. Even when an MFA has been given to the user, you will be able to see what type of MFA was used, if it was through the authenticator app, sms, mobile call or others. |
 | A. Not applied B. Success | This option tells us when the login was granted after the user was analyzed by the Conditional Access of Azure Active directory or when it does not apply. | The user can be sure that his login is being validated and protected, since he is going through the conditional access rules of AAD, in addition to that he can identify when they apply and when they do not. | The administrator can be sure that his users are logging in under the control of conditional access, that if for some reason he violates any condition, the authentication will not be given, which allows giving peace of mind in each of the user logins |
 | Rule of conditional Access, which at that time will apply to the user at the time of access to the resource | Conditional access applied indicates the conditional access policy that was used to evaluate the sign-in attempt and whether the sign-in attempt passed the conditional access requirements. You can click through to understand the name, controls, and conditions from the conditional access policy. | Conditiaonl access applied information provides the specific conditional access rules that were applied to a sign-on event. If you are trying, for example, to troubleshoot a failed sign-in activity, you can click through the details to see the specific rules and conditions that caused the sign-in failure. |
©2020 Synergy Advisors LLC. ALL RIGHTS RESERVED.
Contact Us at (+1) 425-689-3310 or through our Support Page