
Information Governance for the Enterprise
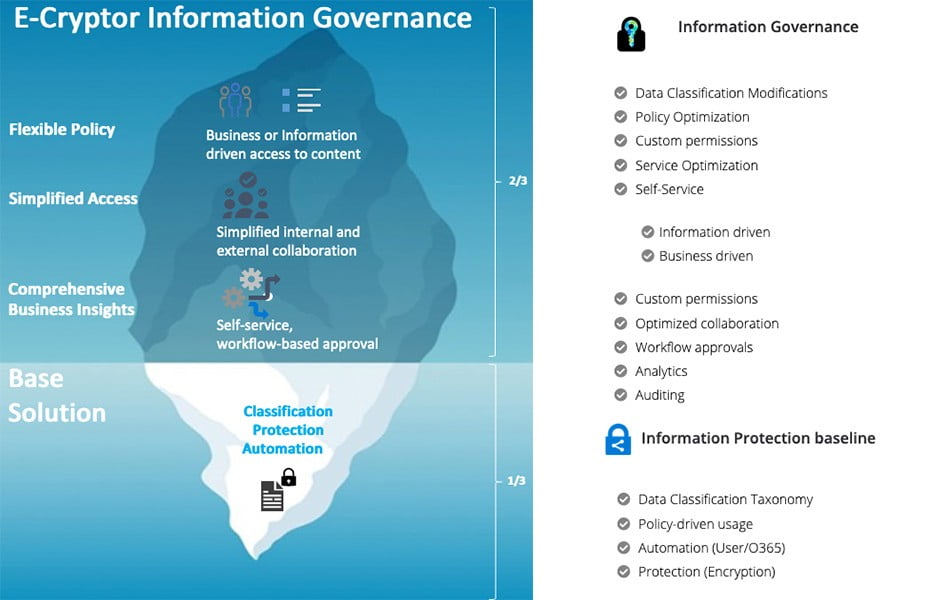
Flexible Policies
Secured and user-focused
- Business and information driven rich policies
- Extend beyond a whitelist access approach
- Scalable for the enterprise
- Based on day-to-day conditions to access and share content
- Tested in multiple real scenarios
Simplified Data Access
Manage documents permissions in a fast and usable way
- Self-service actions available for a user to get or provide access to content
- File access notification and sharing via multiple channels for user convenience
- Extensible to secure external collaboration
- Extensible to business applications
Comprehensive Business Insights
Detailed activity log
- End-to-end user and administrator logging and analytics
- Sensitive information usage based on defined, policy-driven conditions
E-Cryptor – Lifecycle
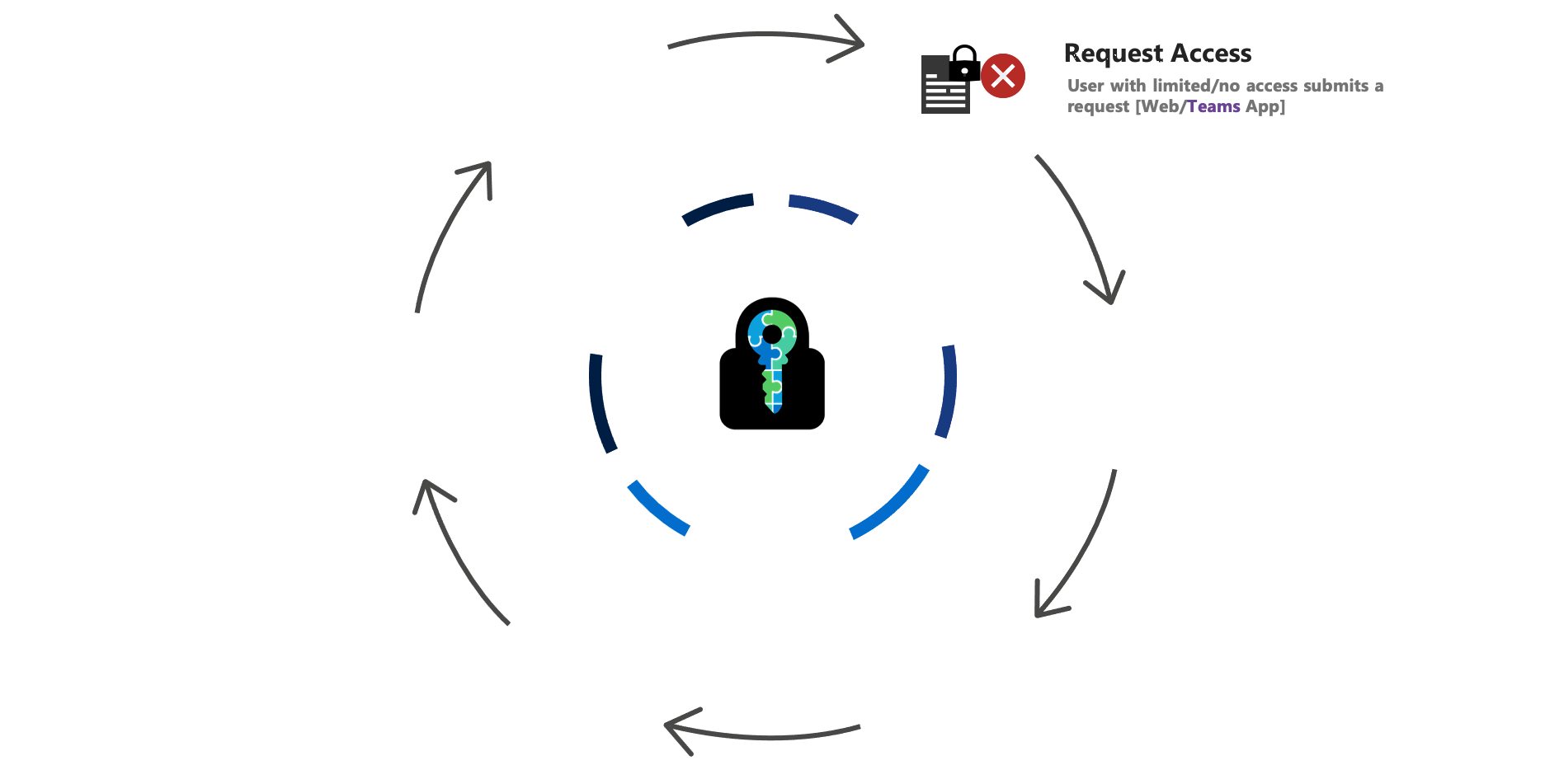
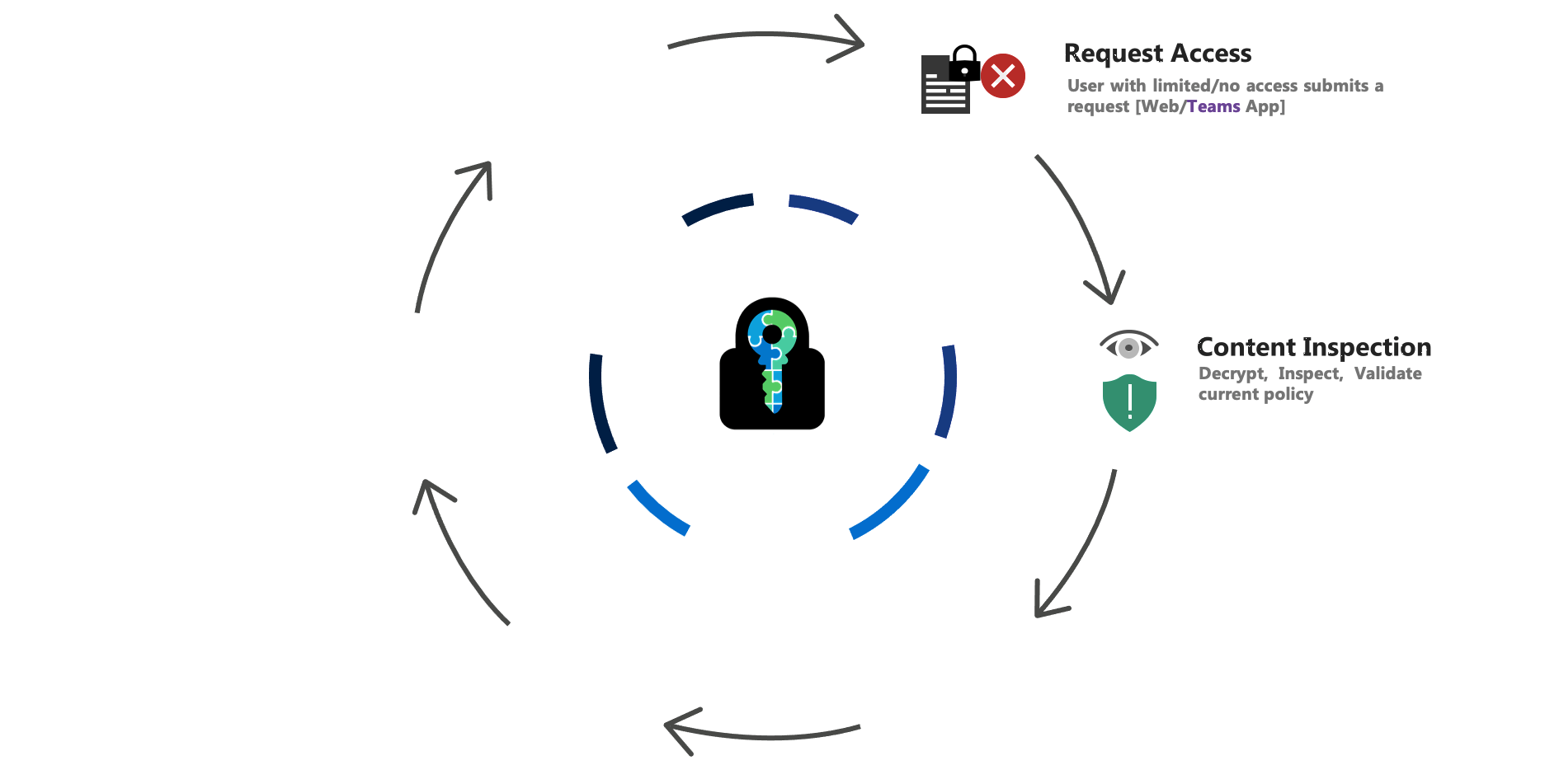
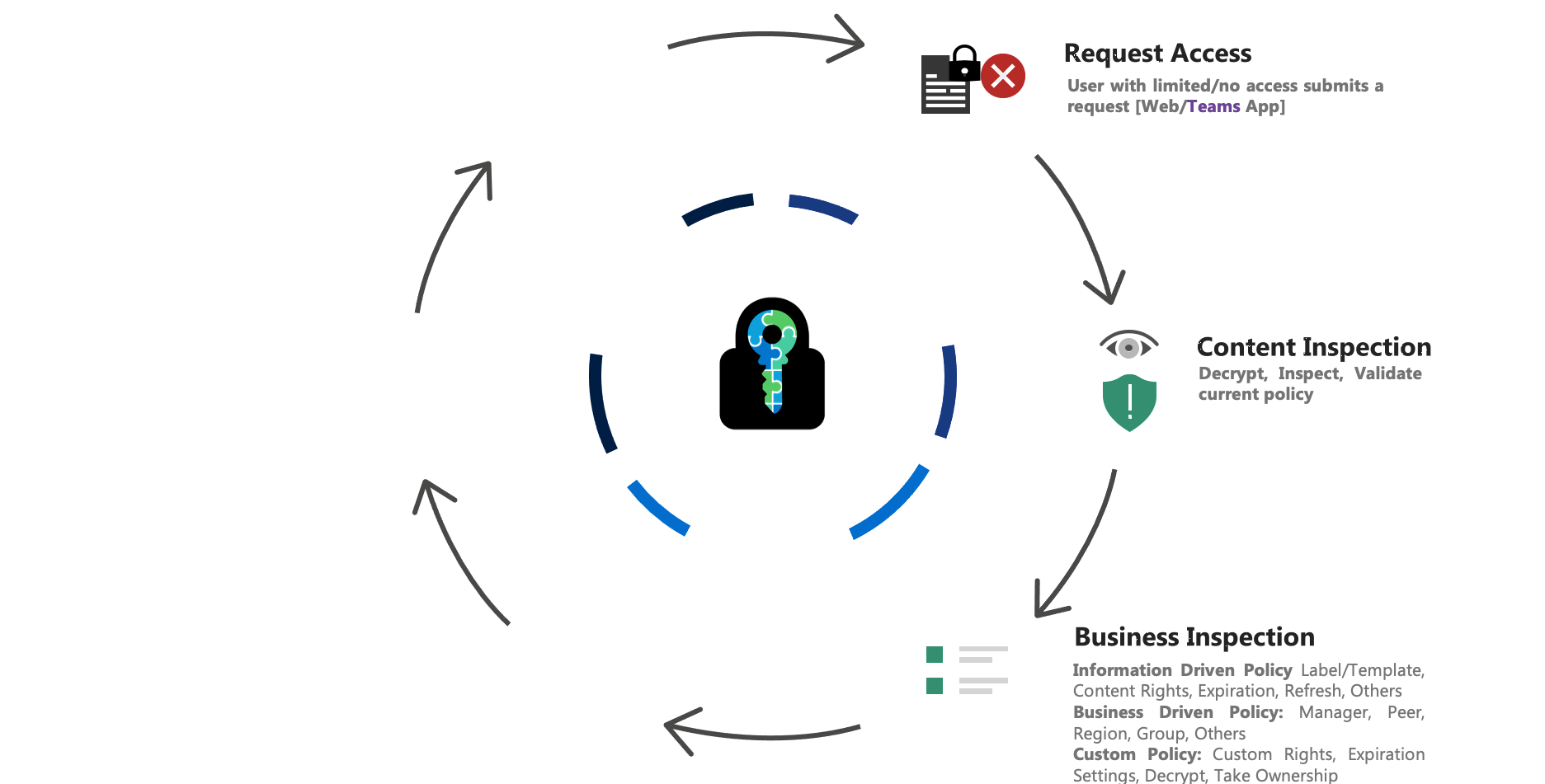
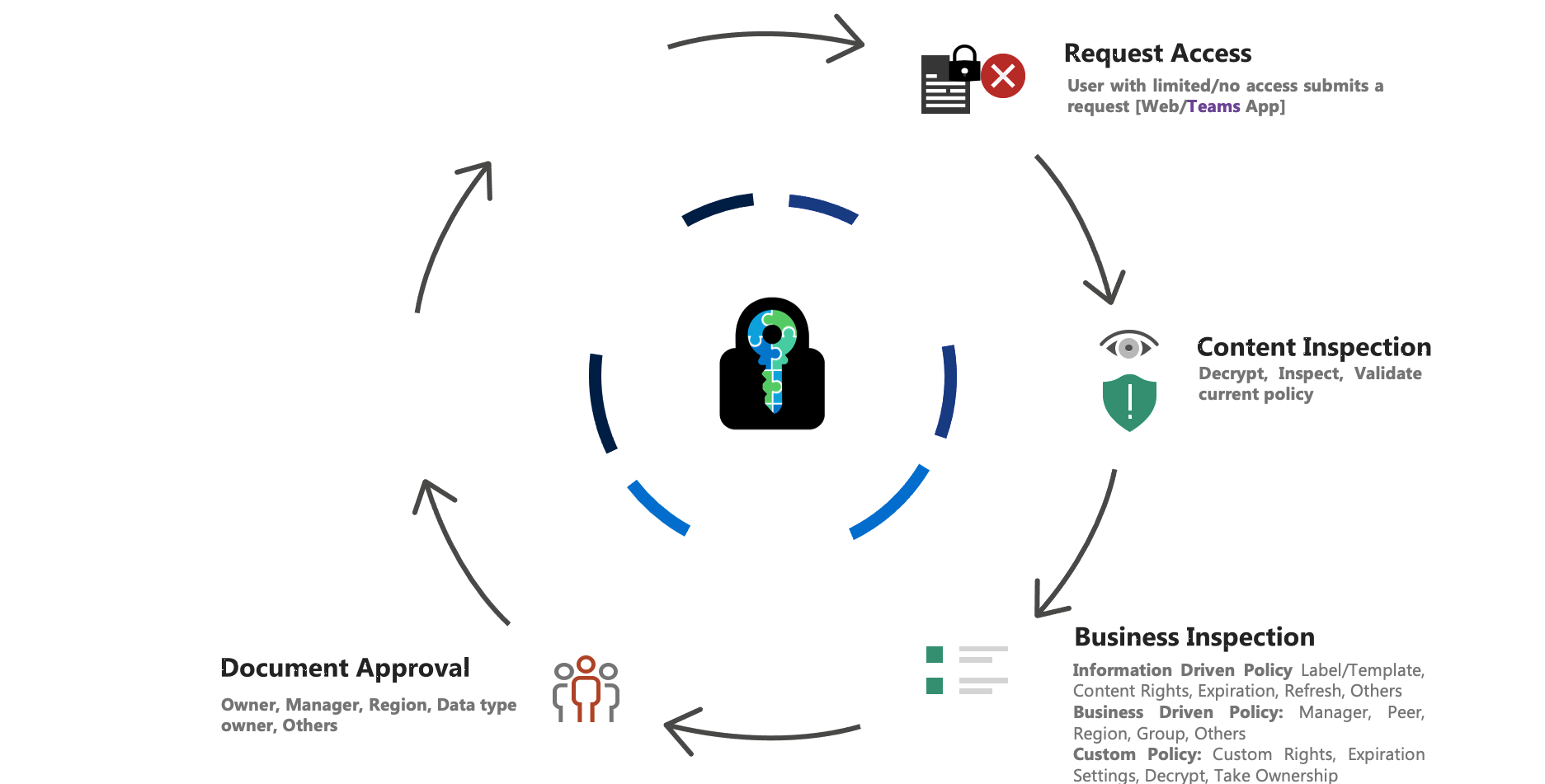
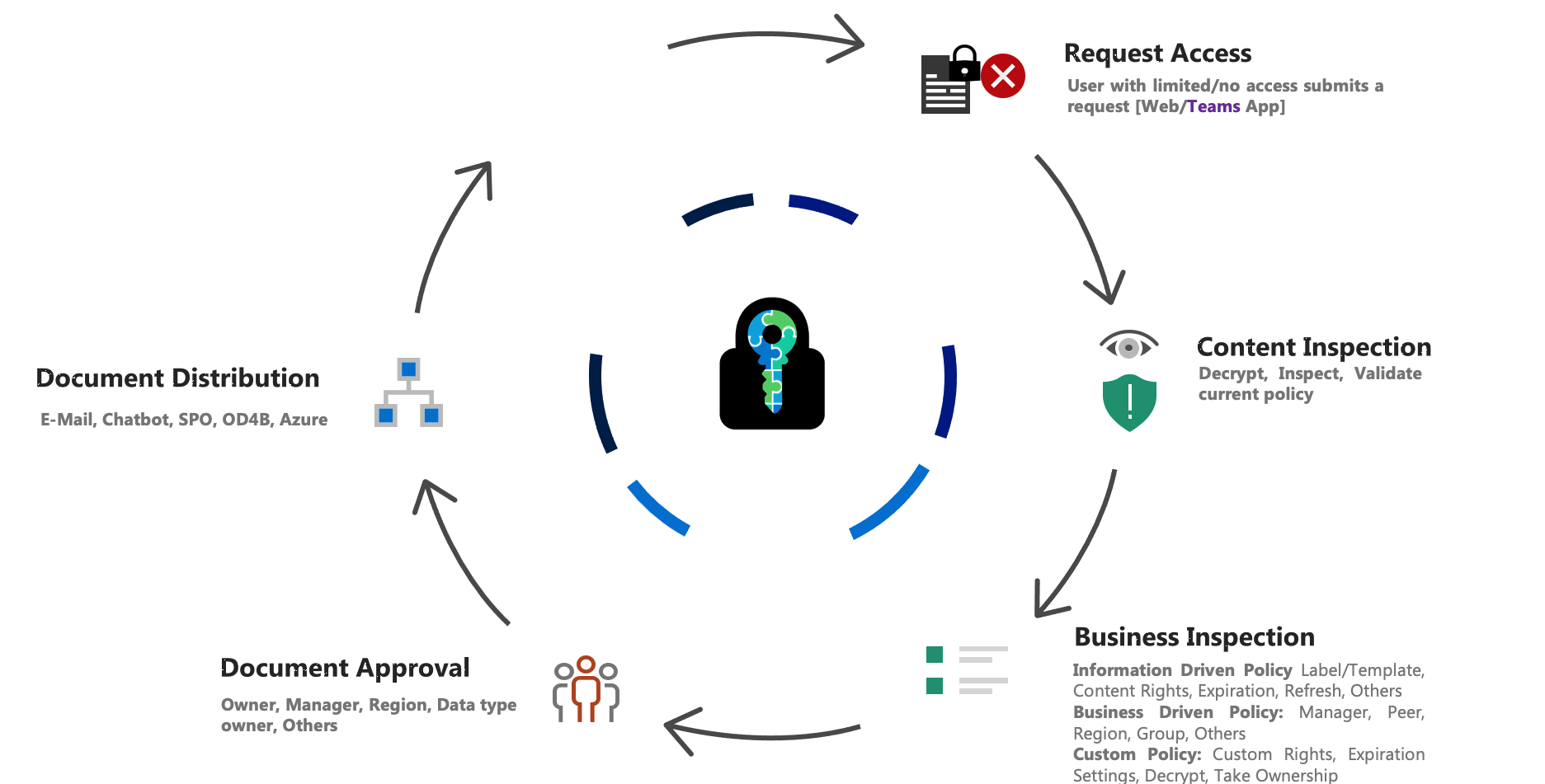
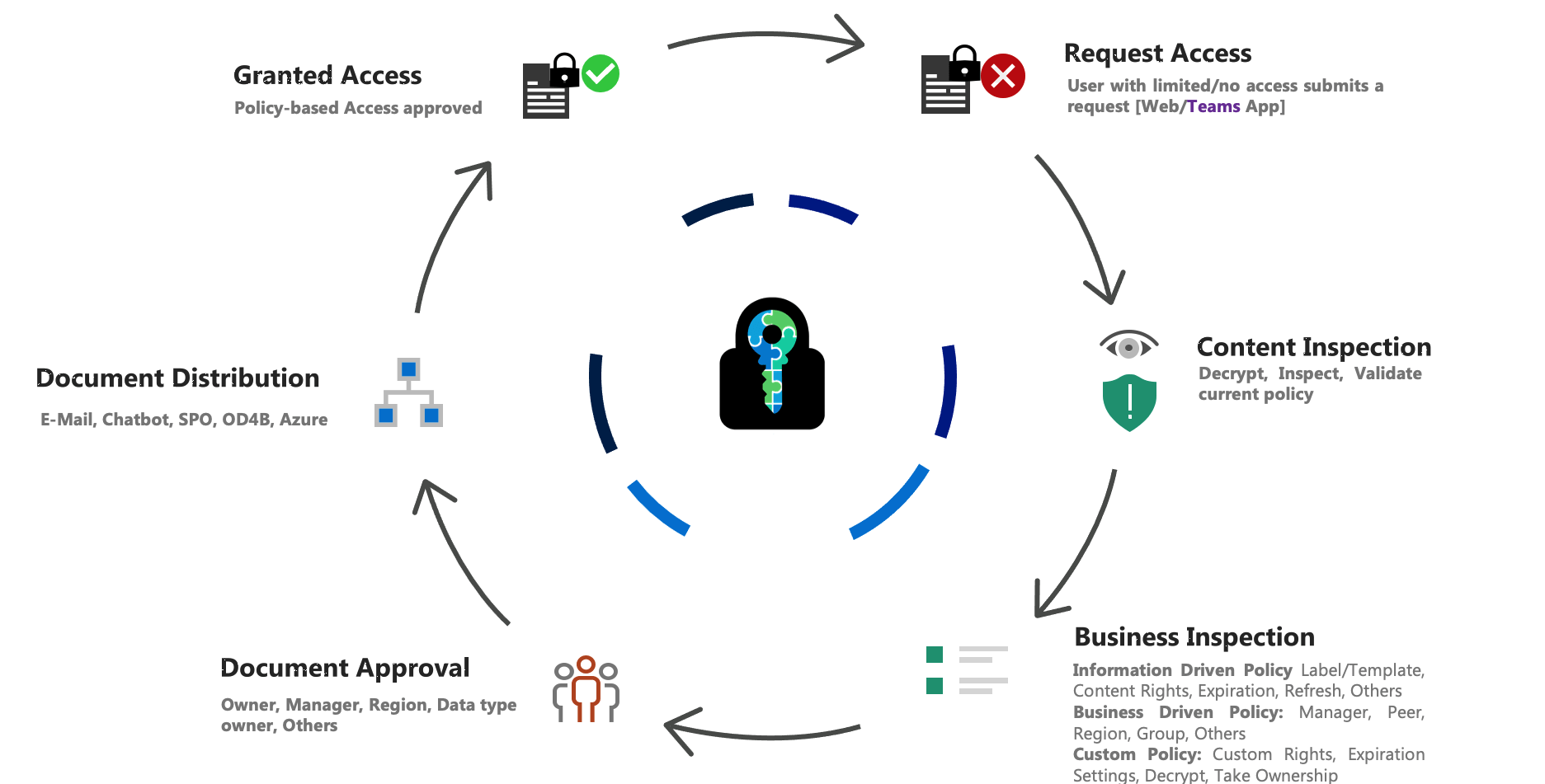
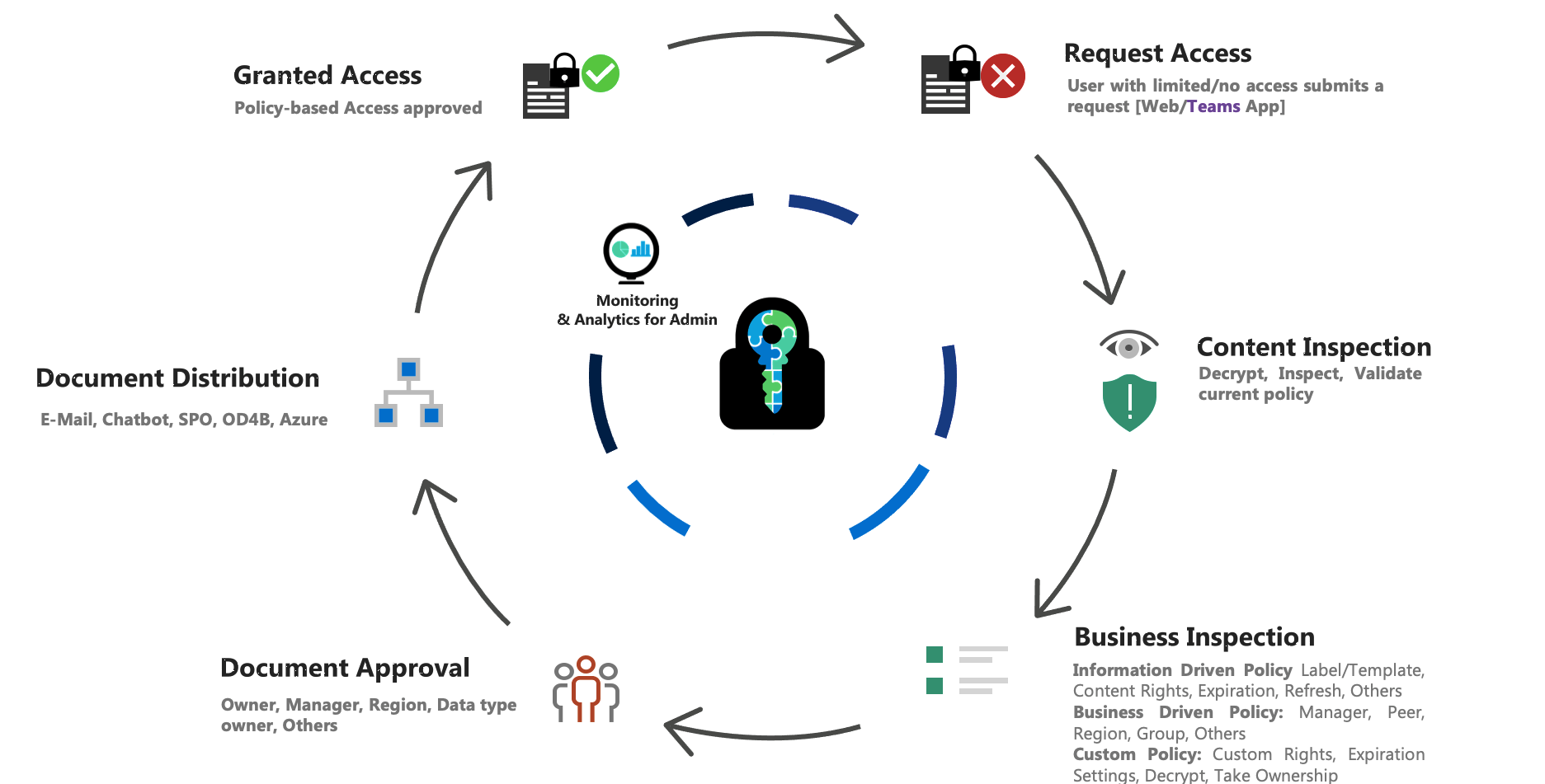
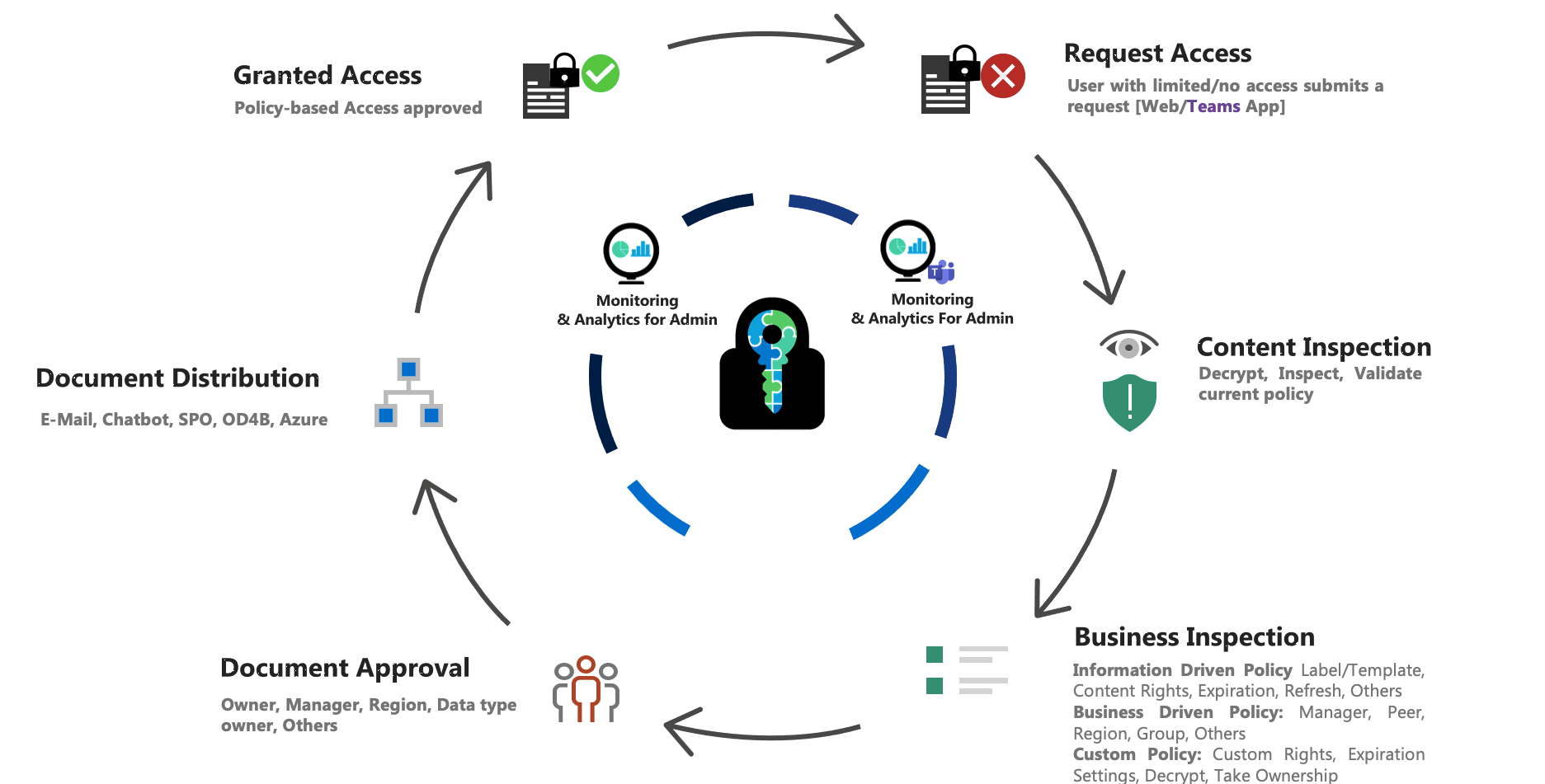
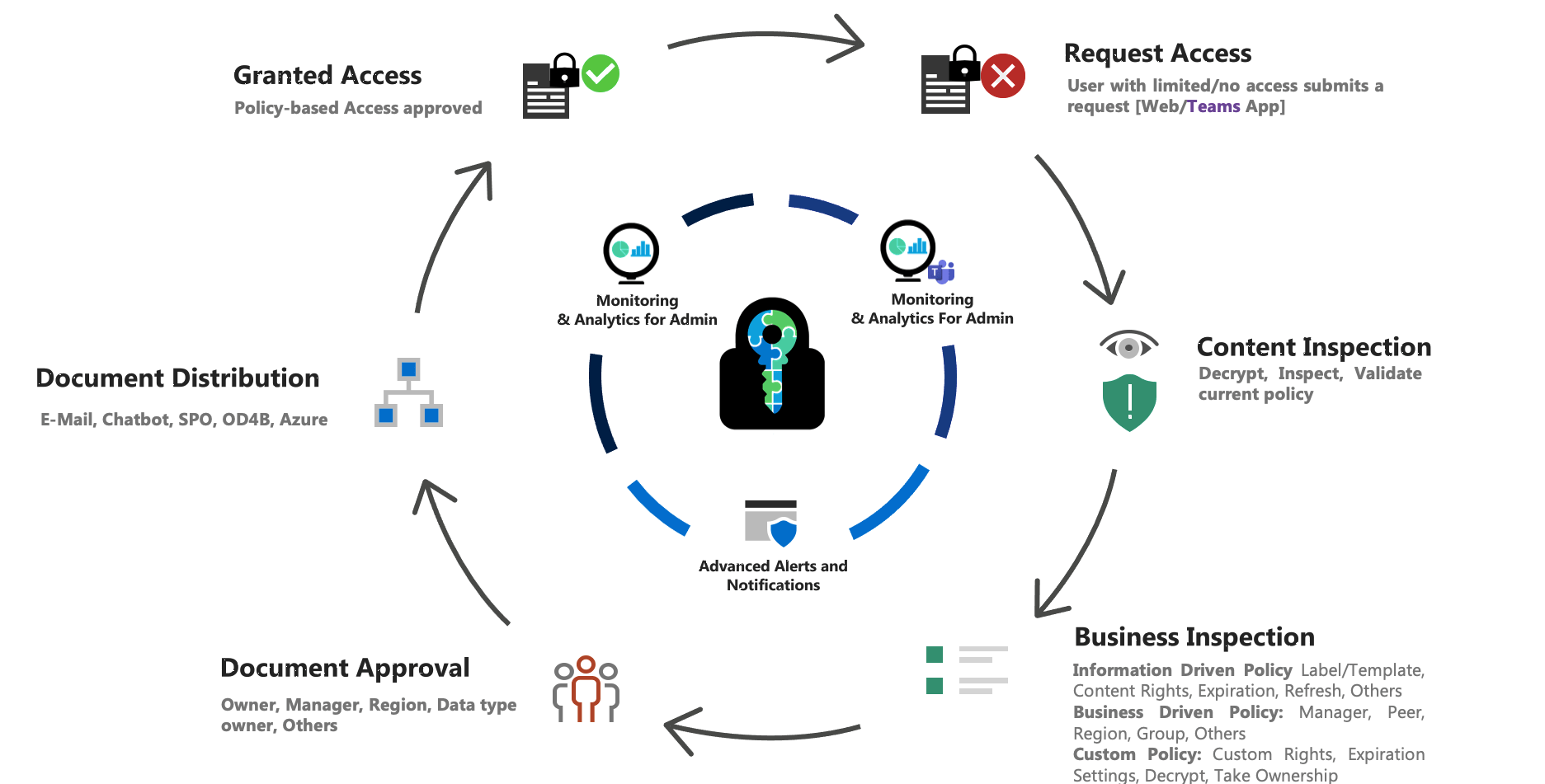
Some of the Collaboration Challenges solved by E-Cryptor
- Owner file unknow
- Need to edit the document and don't have permissions
- Peer is on vacation, and needs to access one of his files
- Share documents with an external user assigning only the necessary permissions
- Manager needs to have access to all the documents of one of his employees
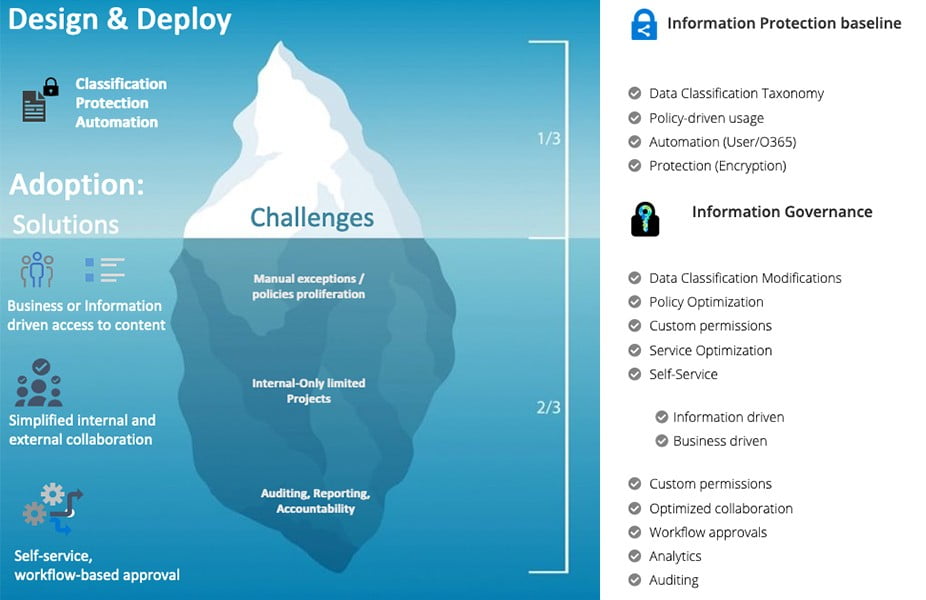
What more E-Cryptor helps you Solve
- Document lifecycle management and governance while improving data controls
- Clear bottleneck for access to encrypted documents; keep the security while simplifying the process
- Governance to data owners, showing who, when, and how their sensitive files have been accessed
Please install and activate TablePress plugin to work this widget.
Request more information
Or you may reach us at (+1) 425-689-3310
[contact-form-7 id="1687"]
©2020 Synergy Advisors LLC. ALL RIGHTS RESERVED.
Contact Us at (+1) 425-689-3310 or through our Support Page