Accelerate Information Protection awareness and effectiveness in your organization using E-Visor Teams App – Information Protection Essentials

Hello from sunny Seattle! (…finally)
Today’s blog post is all about information protection! It’s certainly a topic that is near and dear to me and to Synergy Advisors, as I have enjoyed most of my 20+ year career working with top 100 companies around the world on this critical subject. We are SO HAPPY to announce the release of our new E-Visor Teams App for Information Protection! Our main objective with this tool is to #DemocratizeData through answering these basic, but fundamental, questions:
- What kind of data do I manage, create, and use?
- From where is my data being accessed?
- Can I recognize who is trying to use my data?
With our app, answers to the above questions are detailed and quickly available to a Key Actor: The end-user!
Information workers, first line workers, anyone who creates documents can be instrumental in identifying potential misuse of data.
Yes, the users who create, copy, share, and edit the information itself can significantly augment your information protection if you provide visibility to the use of business data, but HOW can you provide this to your users? Easily and directly in Microsoft Teams, where they already invest a good amount of time! We have evolved our “Enterprise Information Protection” analytics to go beyond an organization-wide view for administrators to every single persona who should know the details behind the use of information they create, classify, and share.
A LITTLE BIT OF BACKGROUND INFO:
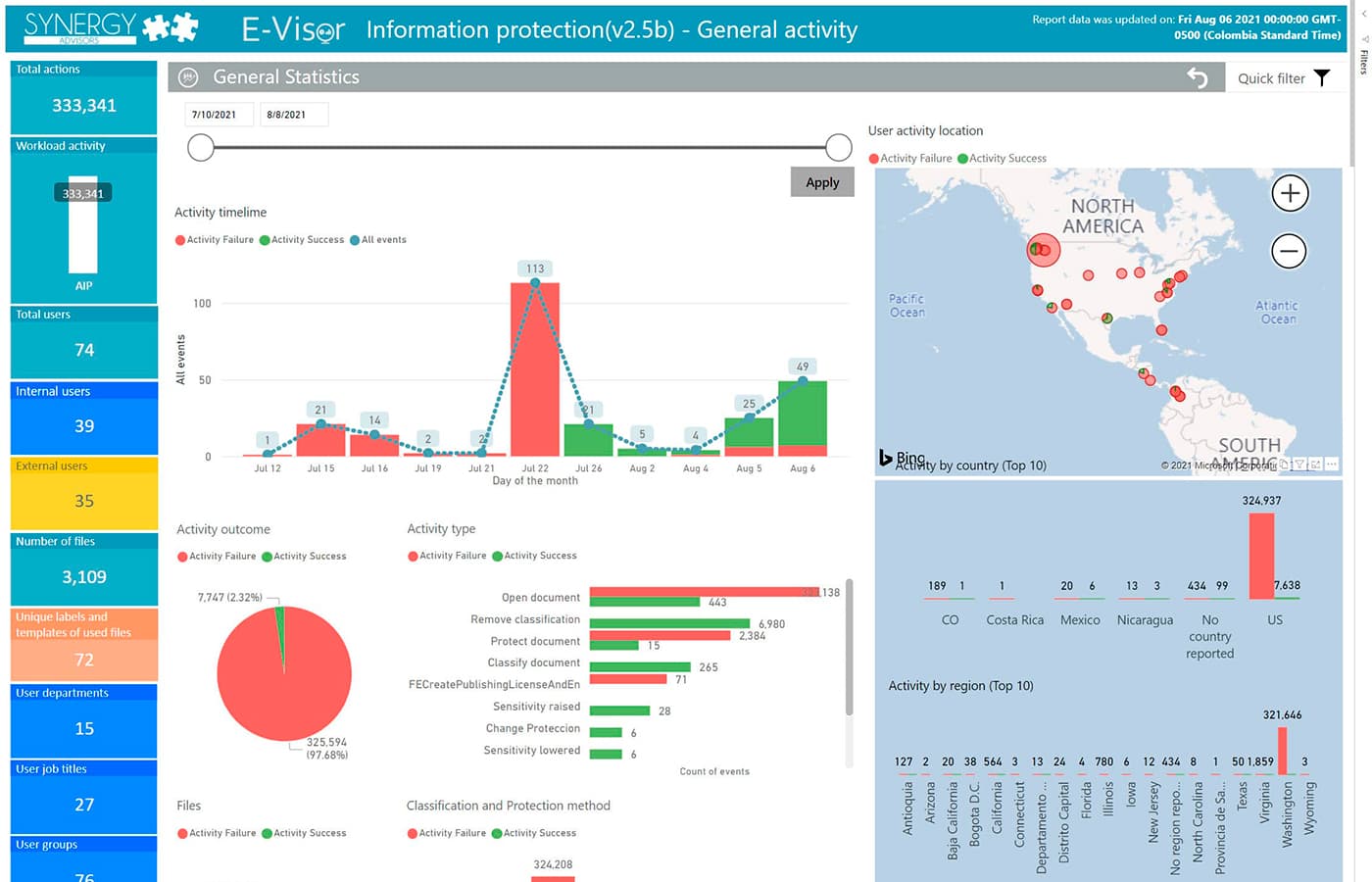
Before digging into this new end user app, let’s look at what we have developed in terms of information protection analytics:
We started building reporting and analytics solutions nearly 6 years ago with Azure RMS, Azure IP, and now MIP to show details about what, who, when, and where (geo-location and device) users have been using or tried to access your data and we correlate this information with your organization’s Azure Active Directory (AAD). This goes beyond just reporting or logging to provide an extremely powerful analytics tool that offers great insight to information usage, which you can filter by role, data type, department, location and more. Previously, that information was available to Security, Compliance and SecOps. It has been such an amazing experience, but now, you will see how to raise your #InfoProtection to the next level and your users and organization will be very pleased through the insights you can provide. Check it out!

Introducing E-Visor Teams App – Information Protection
Let’s look at how you can easily empower your employees to see end-to-end data insights and raise the flag if they see something fishy might be going on:

Activity Notifications
Challenge
As the organization may not have a dedicated team looking for suspicious and anomalous activity along data in use, at rest and in motion, how can you keep up?
How many log entries, potential false positives, policy and alerts configuration, and triggers can match the effectiveness the context an author can provide? Authors can see who is accessing their content and they know who should and who should not see this data. This is not an easy task for IT, Cyber, or SecOps who, with all respect, may not understand all collaboration vehicles and data exchange across your organization. Here, the end user is coming to relieve that heavy burden to different areas along the organization.
Feature Objective
Answer the most common questions asked by users about who is using their data, how, and from where
Feature Scope
Provide a summary that can easily tell you what is worth reviewing:
- Files activity
- Opened and created
- Access attempts
- Successful and unsuccessful

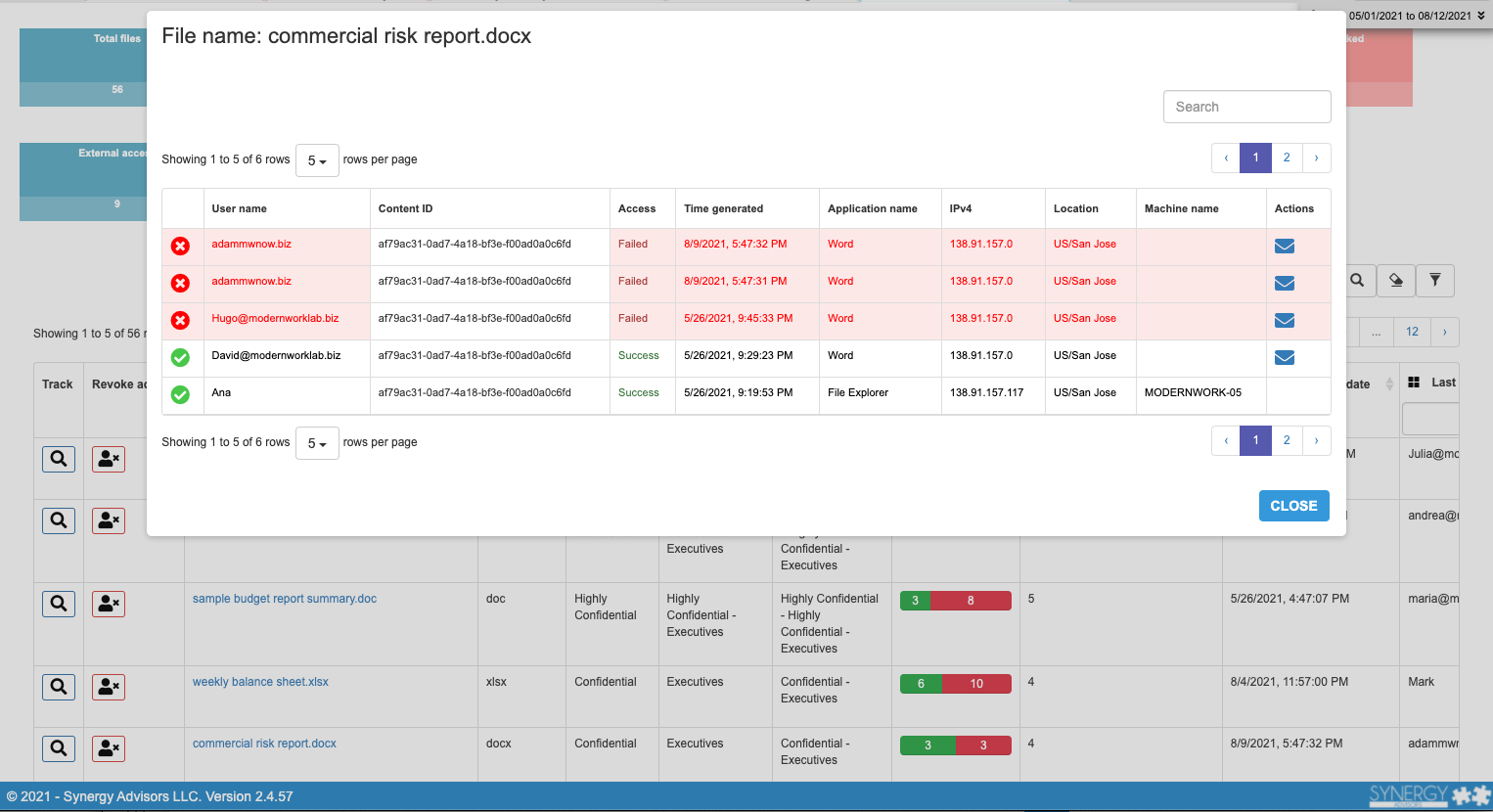
Details: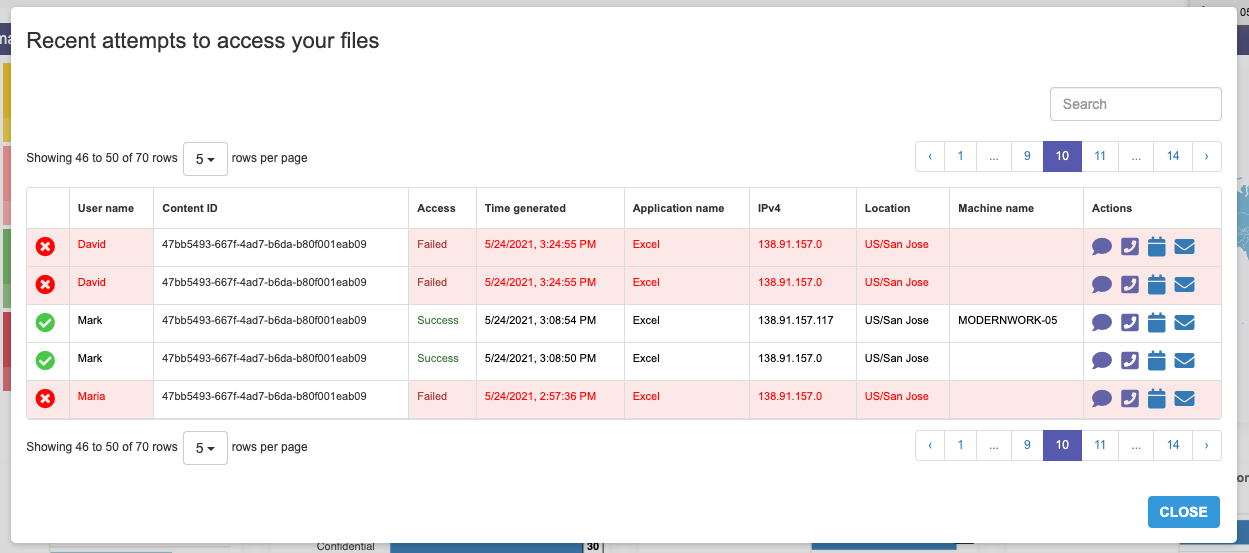
Effectively call end user attention via the yellow ribbon, which presents an activity summary. From there, users can drill into specific actions and cases to learn more about file usage in near real-time.

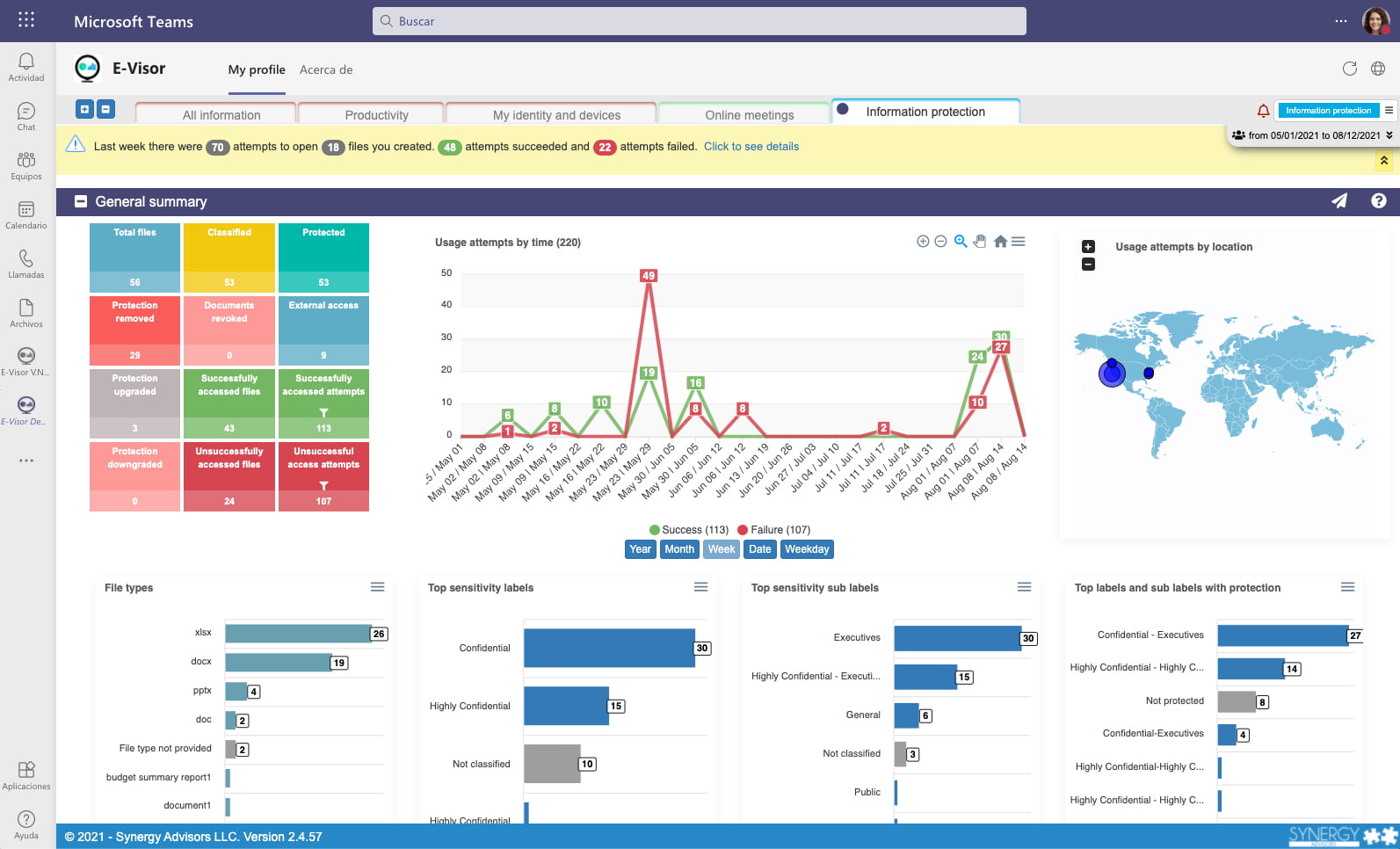
General Summary
Challenge
While simplicity is critical, multiple questions arise about where data is going. Unlike access to a system, which can be controlled by a yes/no parameter, there are multiple considerations, formats, copies of the file, repositories, and other attributes to consider for data. For this, we use an analytics approach to respond to multiple questions, without overwhelming the user with the information we provide.
Feature Objective
Answer the most common questions from users about their data, as data comes and goes.
Feature Scope
Provide insight to easily identify use and potential risks that the business data user is responsible for:
- Totals
- Counters can provide a quick summary about how much activity the user has
- When
- Details on when the access occurs in the timeline perspective
- From where
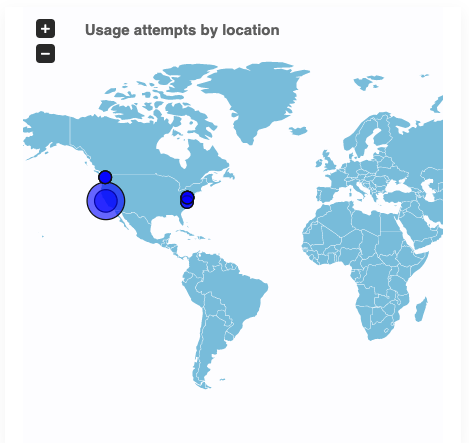
- Geo-location details about when data was accessed
- Also, the number of access attempts to files is represented in the intensity/size of the icons in the map
- Multiple file details
- What kind of file formats
- What kind of labels and sub-labels (content classification) have been used and how encryption has been used to protect data.
- Activity
- Key feature:
- We do not want to just report about usage from users within your organization; we want to tell you from what business unit, departments, and more.
- As mentioned, we provide, beyond logging, AAD correlation that benefits users while exploring who is using their information
NOTE: This kind of tracking capability of file usage is only available to MIP protected documents (encrypted), as they have a unique internal identifier that makes it possible to track, even if the user renames the file.
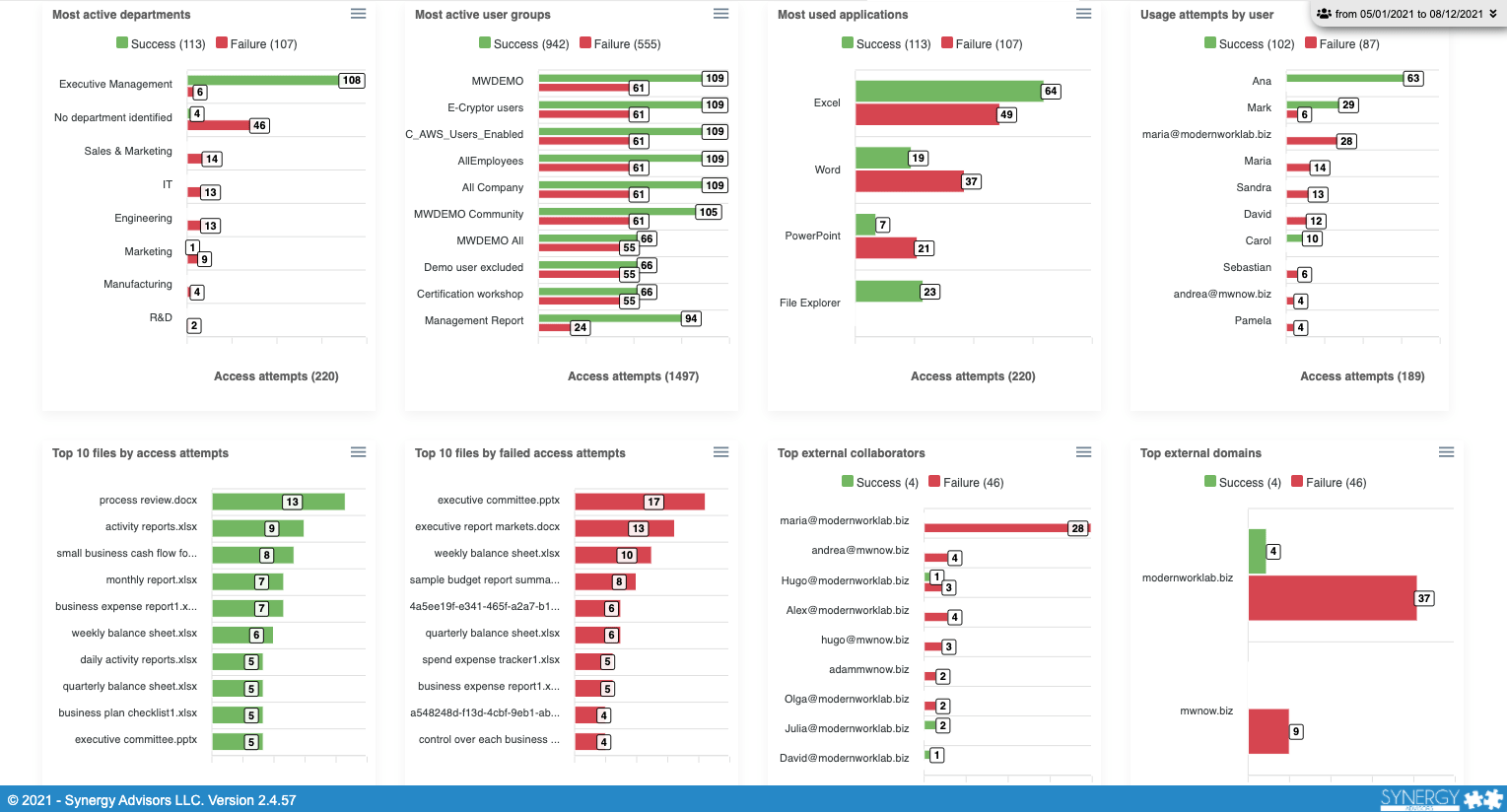
- Additional insights
- Top file access and unsuccessful access
- Top external collaborators
- Top external domains
- Key feature:

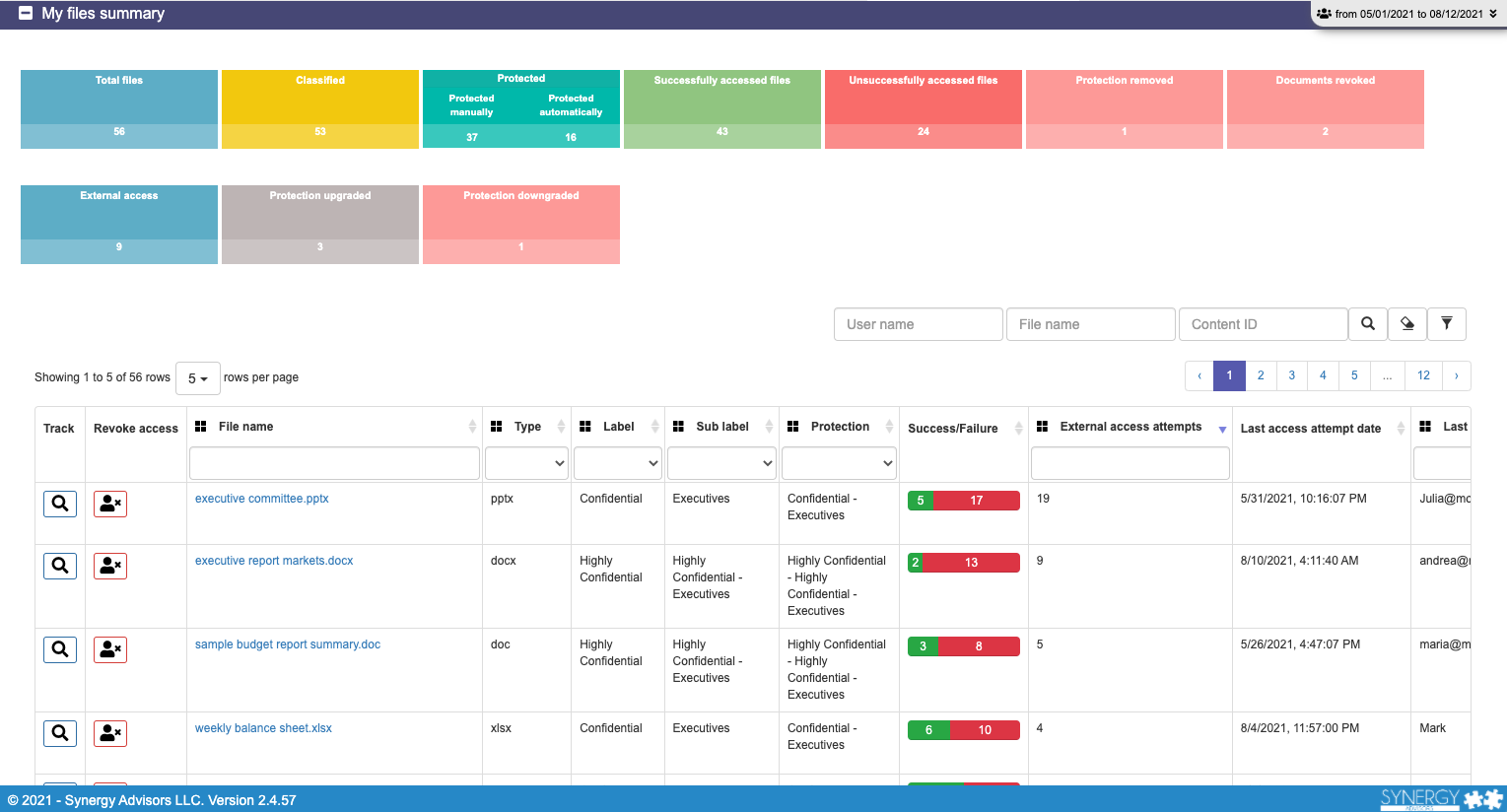
My Files Summary
Challenge
Alright, you captured my attention via the alerts and notifications, or perhaps I am sharing very sensitive information and I want to know the activity around the data I have created and shared.
Feature Objective
Provide per file activity details
Feature Scope
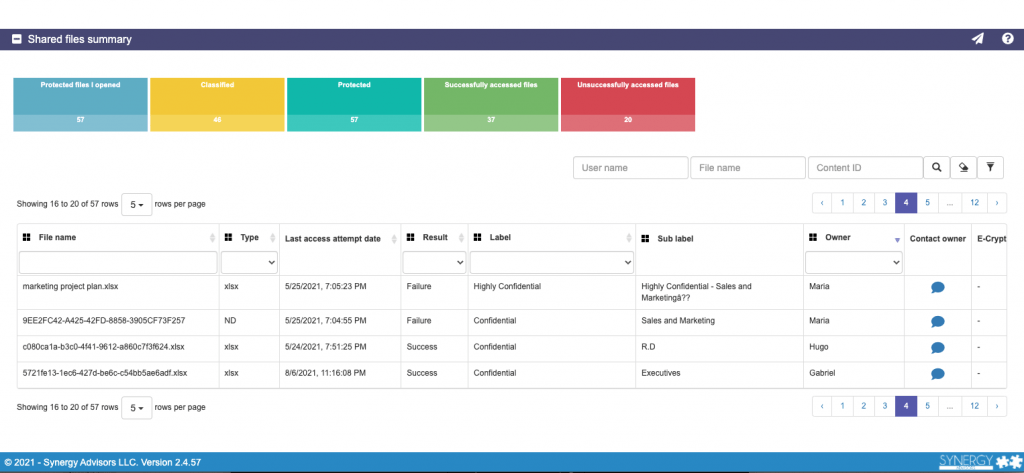
In this section of the application, we provide specifics for each for the files a user has protected with MIP
- Details
– File label and classification details
– Protection status (encryption)
NOTE:- End-to-end tracking, even beyond your network, is available for files that users have applied an MIP policy to that includes the protection feature. This will validate the first time each user tries to open a document, and can be configured to log each subsequent attempt as well.
- Classified-only documents cannot be tracked, as the MIP agent may not be installed on the device used to open the file
- Usage
Here, the user can see who, and from where, tried to access the application, with a confirmation if the data was successfully accessed or not, of course - BONUS
Key Feature: Filtering
This might sound obvious, but you can filter data for the current activity using the checkboxes on top of this section or, eventually, from the table. You can combine multiple parameters to, for example, show only Highly Confidential documents activity, or files accessed by X individuals, or even just when external users tried to access a file.
Key Feature: Revocation
As analytics are clear enough to surface suspicious activity, we empower users not only to contact the people who accessed/tried to access content via Microsoft Teams (internal employees) or e-mail (externals) but also, for immediate action, users can revoke access to the file, which will cancel access to the document, even to users who were originally granted permissions. How nice to be able to “in case of emergency break glass” for accidents in which a user sends sensitive documents to the wrong person or if data access activity seems suspicious
Note that this requires E-Visor Teams App for Information Protection Standard

Shared Files Summary
Challenge
In addition to being able to see what kind of documents you use from others, at some point in time, a user may try to access files to which they may not have permissions or not enough permissions to perform an action. In these situations, what can we do?
Feature Objective
Provide user options to collaborate via Teams and e-mail with the document owner, who can change the permissions policy.
Feature Scope
In this section of the application, we provide specifics for each for the files a user has tried to access and whether they have been classified/protected with MIP.
- Details File label and classification details
In case you need to call IT for help, this can dramatically accelerate identifying why you cannot perform a specific action. - Owner This is the person who applied the label to the file and can make changes to the file’s permissions.
For ease of use, we provide Teams actions so you can contact that person and resolve the access needs you have.
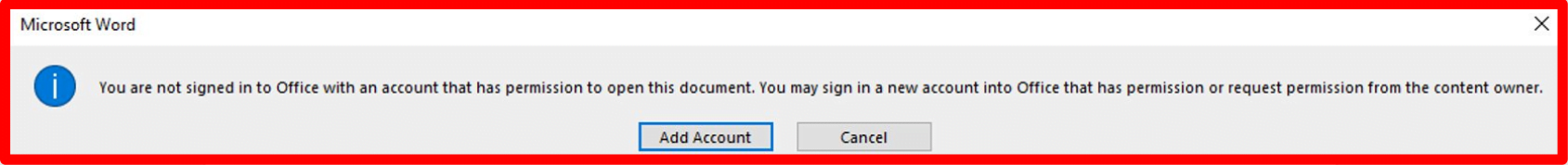
This might sound easy to do for a small company with very few documents, but what if I told you that sometimes MIP does not reveal who the owner of the file is? How do you know who can help you access a document without being forced to contact IT? Don’t worry, we’ve got you covered
BONUS
In case you want to go beyond knocking doors to start requesting access to a file, or sharing a file with another person, we can help you with these scenarios (and more!) via our E-Cryptor app/portal
Follow this link to learn more

General/Miscellaneous Considerations
Lastly, I do not want to miss other relevant app details for your consideration:
Range Filtering
First, people would like to focus on what they are seeing
No problem! We provide a range so users can specify and set a timeframe of data they would like to focus on and all reports will automatically be adjusted accordingly
Geo Location
Just like how our E-Visor for Information Protection (Power BI) provides great insight based on where the data has been used, we provide this capability to the end user. It’s such a quick way to identify potential data risk/exposure due to infrequent or rare locations accessing or trying to access your data
Privacy
Of course, this is your data and your insights; all of this runs in YOUR Azure subscription and your end-user Teams application. There is no data (other than subscription/licensing activation) sent to Synergy Advisors.
Microsoft Information Protection Licensing
These reports are for customers with EM+S, M365 E3, M365 Information Protection and Governance, and M365 E5 (see also Azure requirements)
Azure Consumption
As stated previously, we help you install our solution (both the end-user app from the Teams Marketplace and the backend components in your Azure Tenant) along with all corresponding pieces (database and others)
For ease of use, we can provide you with a sizing tool so you can quantify the potential ACR needed to run the app. Note this will also depend on the number of users, documents, and e-mails in the organization
We are so excited to see organizations like never before embracing MIP; let us help you get the most out of it!
Interested in a live demo or discovery execution? Contact us at [email protected]