MitM Phishing Toolkits Present New Threats
Multi-factor authentication can be intercepted by almost 1200 man-in-the-middle phishing toolkits

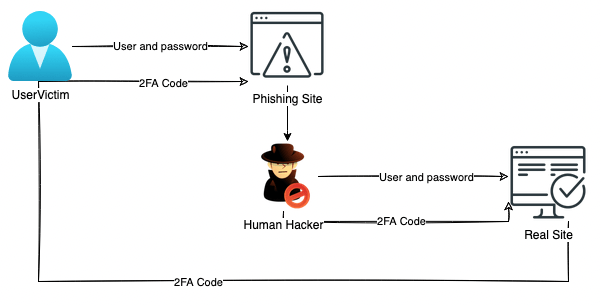
We are seeing a rise in cyber criminals threats through the insertion of reverse proxies with man-in-the-middle attacks to steal authentication cookies from login services. This technique enables attackers to bypass modern authentication, such as two-factor authentication (2FA) or multi-factor authentication (MFA).
This attack is different from real-time phishing scams in which attackers steal credentials and the second factor (as opposed to authentication cookies) in real-time and requires human intervention to be inserted into the real site. In some cases, real-time attacks can be prevented with MFA.
Typically, 2FA man-in-the-middle attacks using phishing toolkits are targeted at services like social media, email, movies, gaming, and others accounts that have comparatively relaxed rules for the expiration time of session cookies, which can sometimes be valid for years.
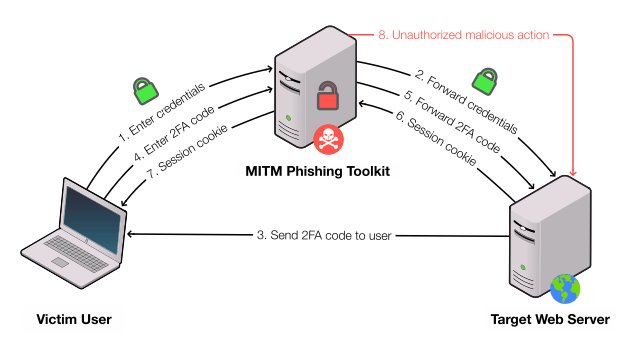
MITM Phishing Toolkit
According to a recent report entitled “Catching Transparent Phish: Analyzing and Detecting MITM Phishing Toolkits” from Academics of Stony Brook University and Palo Alto Networks, an alarming aspect facilitating the rise of these man-in-the-middle attacks is easy access to phishing toolkits through easily-accessible repositories like Evilginx, Muraena, and Modlishka.
How can the E-Visor Teams App help?
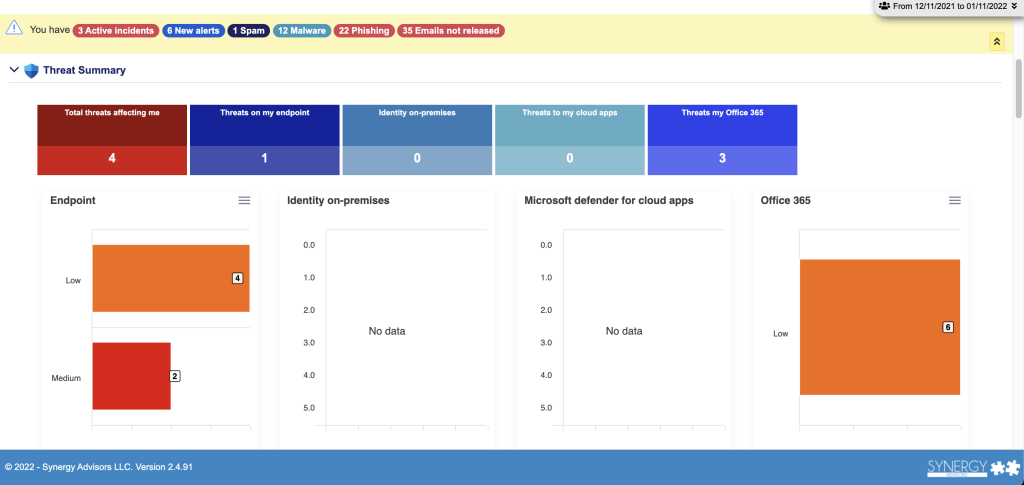
E-Visor Teams App can show end users and support teams suspicious activity from user accounts and even proactively alert them to specific issues. E-Visor Teams App provides a complete and dynamic log of user account activity, all directly inside Microsoft Teams, empowering end users, who have the context necessary to identify anomalous usage.
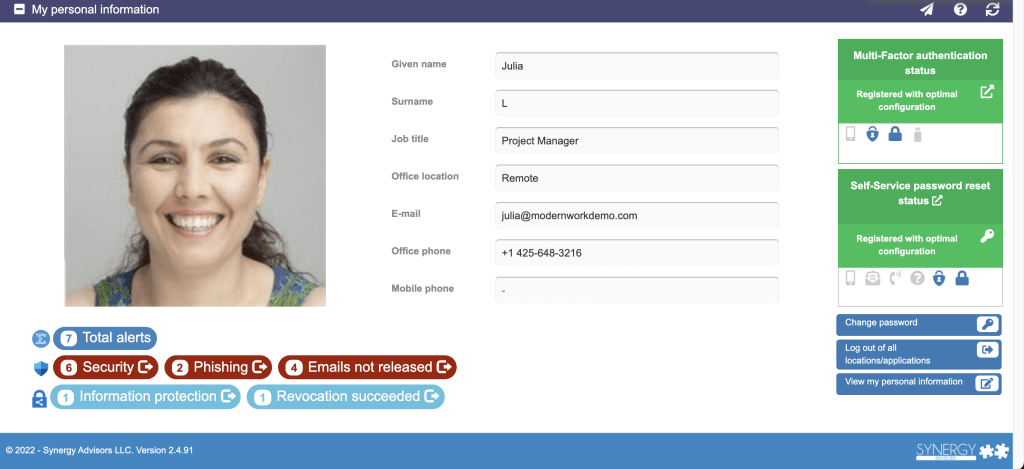
MFA is a critical component to protect users from real-time attacks. E-Visor Teams App quickly and easily shows users whether they have enrolled in MFA and configured the service according to best practices, ensuring compliance with your organization’s policies in the most user-friendly manner possible. Green is good, red is bad.
Additional information
The authors of the study have developed a tool they’ve called PHOCA that can help detect if a phishing site was using a reverse proxy—a clear sign that the attacker was trying to bypass 2FA and collect authentication cookies, rather than credentials.
Contact us
If you are interested in more information about how to protect your organization from man-in-the-middle attacks, including a live demo or Pilot of the E-Visor Teams App, contact us at [email protected].