
- multifactor authentication
- May 26
- Comments (0)
Improve cybersecurity: An increasingly pressing need
The basis for United States Executive Order 14028 and the actions of other governments
The world is experiencing more and more cyber-attacks at all levels; from individuals to companies to entire nations, attacks are increasing in number and sophistication, putting information, operations, and businesses at serious risk. Remote work and the arrival of 5G have played an important role in increasing risks and attacks by not having adequate or sufficient controls to mitigate security risks. This has led to the continuation of the trend of Ransomware and phishing attacks and staying at least one step ahead of cybercriminals is critical to protecting your sensitive assets.
At the end of 2021, BeyondTrust presented the 5 cybersecurity predictions that companies and nations would face during 2022:
- Increase in phishing attacks through e-mail, social media and fake websites
- Shortage of cybersecurity talent, leading to salary increases
- 5G as an opportunity to provide and access services outside Wi-Fi and local area networks
- New models of extortion through custom Ransomware and with the use of IoT devices
- Increase in supply chain attacks, leading governments to turn to legislation to deal with these threats and protect networks, as well as collaborate with private sectors and other governments to identify cyber threats
These predictions are coming true!
Given this complex situation where we see an increase in sophisticated and persistent cyberattacks on governments, private sector companies, and individuals, governments such as the United States are taking action. The White House released Executive Order 14028 in May 2021, covering many key areas that need to be addressed to protect critical digital infrastructure. This is one of the most detailed U.S. executive orders on cybersecurity released by the White House, and affects many organizations, both in the public and private sector, that work with the government.
Most notably the executive order contains a number of specific mandates related to assessments, reports, and the deployment of specific security tools, such as multi-factor authentication (MFA), encryption, and zero trust architecture (ZTA).
How does Synergy Advisors support organizations in this scenario?
Synergy Advisors develops technologies and solutions that enable organizations to establish effective security and productivity strategies. Speaking specifically to the scenario mentioned in this article, Synergy Advisors’ team of experts has developed a set of offerings, based on cutting-edge methodologies, functionalities, and solutions that enable organizations in the United States to comply with EO 14028, as well as organizations from other regions and countries to secure their technological environments in authentication, encryption, information governance, alerting, and analytics.
Synergy Advisors’ Multi-Factor Authentication
E-Visor is an analytics tool developed by Synergy Advisors that provides reports and analytics to enable organizations to achieve compliance and governance policies and take control of how their data is managed. In the Microsoft Teams app version, it collects data across different Microsoft portals to present it back to end users in a single location, where they can monitor their identity and device activity. To secure access to organizational resources, applications, and services, the experts at Synergy Advisors have developed a multi-factor authentication (MFA) module available to be configured and used by end users through E -Visor Teams App. This helps optimize processes and reduce time, costs, and security risks, providing an intuitive end user experience, quickly and efficiently, without requiring intervention from the organization’s service desk.
In a few steps, the user can:
- Access the application
- Configure a second authentication factor
- Change, remove and add the verification method
- Update information
Next Generation Cybersecurity with E-Visor Teams App
E-Visor Teams App provides strong capabilities to secure sensitive information and resources, supported by advanced Microsoft solutions. From the security tab in the application, users can easily see, and take action on, the security of their identities, devices, and cloud apps.
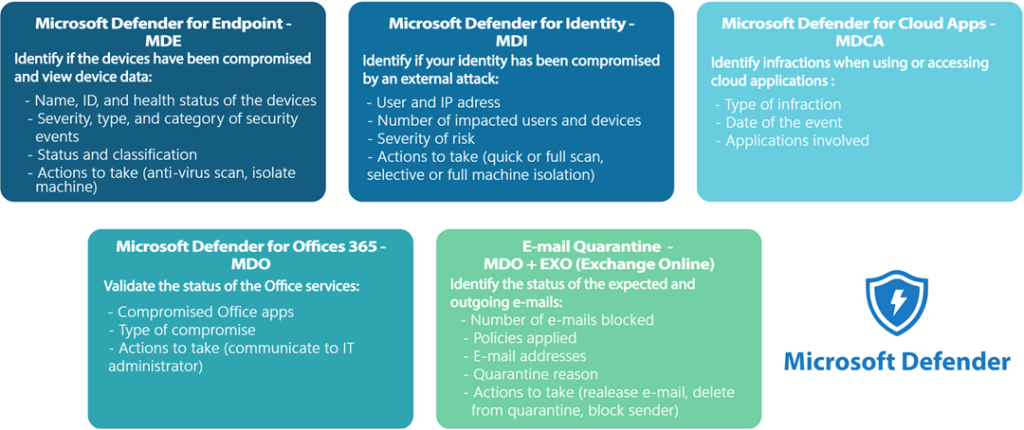
Encryption, data control, and information governance
advanced and exception encryption workflow
Synergy Advisors’ E-Suite solutions provide end-to-end protection under the multiple information protection scenarios. E-Cryptor enables organizations to properly manage information and provides a strong layer of protection, while optimizing time and reducing costs. E-Cryptor helps organizations solve advanced and exception encryption workflows, removing the need to send these requests to the IT department. Instead, your users can personally manage access to their documents and files, even when access is restricted, optimizing wait times for access to a document and enabling secure collaboration inside and outside the organization.
This solution facilitates the document lifecycle management and governance process while improving data control, through advanced functionalities for diverse scenarios:
- Secure Collaboration: E-Cryptor can help provide limited and time-bound secure access to files that your users need to share on an exception basis.
- Application Integration: E-Cryptor can help automate the encryption and decryption of files as they leave or enter a service application, to ensure that the application or service can act on the encrypted file, for example, to perform search, indexing, rendering in the UI, analysis, and more. E-Cryptor can also automatically encrypt a file on download, securing the file as it leaves the protection of the service or application.
E-Cryptor main features and benefits
- Eliminate bottlenecks: Easily access to encrypted documents
- Security: Maintain security while simplifying the process of consuming data
- Self-Service: Document access request
- Data governance: Who, when and how confidential files have been accessed
- Flexible Policies: Secured and user-focused
- Simplified Data Access: Manage documents permissions in a fast and usable way
- Comprehensive Business Insights: Detailed activity logs
Synergy Advisors provides the necessary tools to comply with Executive Order 14028 of the United States government, providing comprehensive protection through disruptive cybersecurity strategies and technologies.
While the order focuses on the U.S. government, the cybersecurity challenges are global. This is where the continental and intercontinental coverage offered by Synergy Advisors plays an important role in supporting organizations of all sizes and industries in securing information, protecting supply chains, securing identities and access for remote work, discovering and protecting sensitive data, and generating effective data governance strategies.
Contact us to help you face your security challenges.



