
- passwordless
- Jul 7
- Comments (0)
Our Password Independence Day is Here!
For years we have been forced to “remember” passwords to access the different sites, services and applications that we use, both personally and in our work. Especially with more organizations adopting full or hybrid remote work environments, the way we manage, secure, and protect access and identities has become one of the most common, and at the same time most difficult, challenges to overcome. In many cases, the only protection tool to secure access to systems and applications is the user’s password.
Today, more than ever, it is crucial to remember why passwords are not a secure method, especially if we consider that we, as users, are the ones who promote their misuse, generating security gaps with common errors such as the following:
- Use the same password for different services
- Set weak and easy-to-crack passwords
- Use personal information to create passwords
- Store passwords in physical or unencrypted digital files
These bad practices can trigger cyber-attacks that expose the sensitive information of organizations; Let’s look at some of them:
- BRUTE FORCE ATTACK: The attacker attempts to access a system repeatedly, using different combinations of characters, until one of them matches and gains access.
- PASSWORD SPRAYING: The cybercriminal acquires a list of accounts and tries to access them using a set of widely used passwords, until one matches.
- SOCIAL ENGINEERING: Tricking the user into delivering their access credentials through techniques such as phishing (via e-mail), smishing (via SMS), vishing (via a call), warshipping (an infected technological gift), or shoulder surfing (spying on the password while the user is unaware).
- KEYLOGGER ATTACK: The attacker infects keyboards by installing software that tracks and records what is typed, thus stealing passwords.
- MAN-IN-THE-MIDDLE: The cybercriminal intercepts the communication between 2 or more interlocutors and impersonates the identity of one (or more!) of the parties, to see the information and modify it at will.
As we can see, passwords are no longer the most secure and effective method to protect access to our systems. Generating a strong password or following best practice recommendations, such as using different characters, lengths, symbols, and using different passwords for each site, are no longer a guarantee that our identities will not be compromised.
We are in the month of independence; it’s time to free ourselves from passwords!
Passwordless, the liberator!
Important organizations in the technology industry are looking towards new horizons to keep identities and access secure while providing a layer of protection to the systems, services, and applications that we use in both the personal and corporate spheres. It is estimated that a medium-sized company loses an average of US$155,000 in economic and reputational value for each password attack received (Kaspersky).
Given this scenario, expert companies such as Microsoft, and Gartner have recommended the use of Passwordless methodologies to mitigate security breaches caused by using passwords, which are vulnerable to increasingly advanced and sophisticated attack techniques.
“During the past year, we have seen a small increase in client inquiries specifically citing ‘passwordless’ and an increase in inquiries about other passwordless approaches,” says Ant Allan, Vice President Analyst, Gartner. “By 2022, Gartner predicts that 60% of large and global enterprises, and 90% of midsize enterprises, will implement passwordless methods in more than 50% of use cases.”
The Passwordless concept is born from the Zero Trust model (never trust, always verify), which assumes that there can be attackers both inside our network and outside it, and not to trust any user or device by default. For users, Passwordless eliminates the need to remember or type passwords, leading to a better user/customer experience. For organizations, the need to store passwords is eliminated, leading to improved security, reduced breaches, and lower IT support costs.
Passwordless proposes the elimination of static passwords to strengthen user authentication through methods that work from 3 fundamental aspects that, used correctly, enable the mitigation of gaps related to static passwords:
- Something that you know, for example, a code, or a pin
- Something you have, such as an access key, or a token
- Something that you are, related to biometric authentication such as facial recognition, or fingerprint use
Microsoft presents the following diagram that clearly shows the position that organizations would obtain by implementing Passwordless:
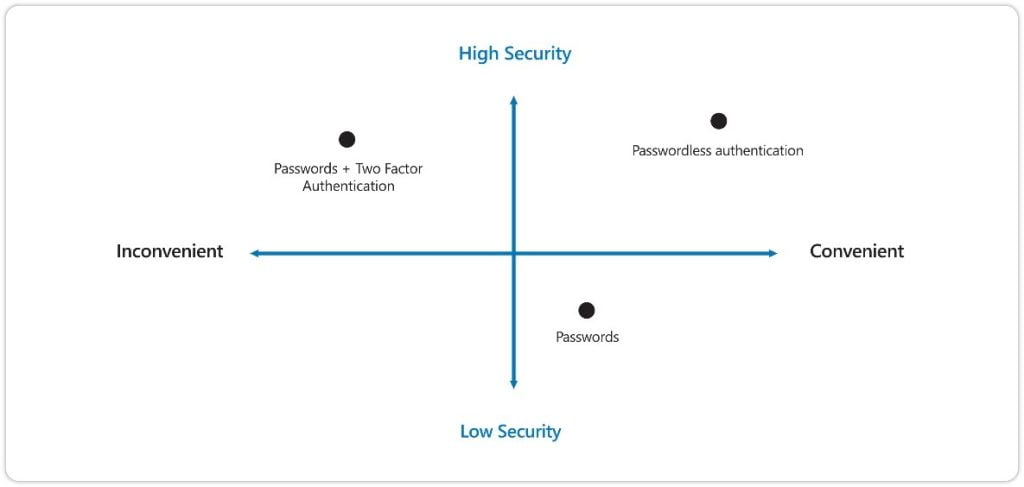
Passwordless authentication methods are more convenient and provide a better user experience because there are no passwords to remember and they are supported by almost all devices and systems. Additionally, they are virtually impervious to phishing.
Passwordless benefits
- Faster authentication to apps and services: End users no longer need to create, manage, or remember passwords. In contrast, they can log in quickly with a look or a touch, using biometrics.
- Higher levels of security: Through recognized security standards, there is a wide range of devices and services that help strengthen your security posture.
- Reduced IT costs: Technical support incidents for password resets represent a high cost and generate productivity losses.
Some secure authentication methods that strengthen your security posture include the following:
- MULTI-FACTOR AUTHENTICATION – MFA: When accessing accounts or apps, users must provide additional identity verification, such as scanning a fingerprint, or entering a code received by phone.
[You may be interested: Multi-Factor Authentication use case]
- AUTHENTICATOR APPS: This authentication method provides a high level of security and removes the need for the user to provide a password at sign-in.
- BIOMETRIC AUTHENTICATION: Users can log in with a look or a touch, with no need for a password. Biometric authentication uses fingerprint or facial recognition and is more secure, more personal, and more convenient.
- SECURITY KEYS: With a simple touch, a multi-protocol security key protects access to computers, networks, and online services.
How to establish passwordless in your organization?
The step towards this methodology suggests an evolutionary and progressive process that ends in the total elimination of passwords in your organization, reaching an optimal level of security:
- IDENTIFICATION: Categorizing users by their level of privileges, as well as determining the appropriate authentication methods for your organization. This should be a personalized process for each organization to meet its specific needs.
- PLANNING: Determine the plan for using the new authentication methods, while progressively reducing the use of passwords in services, applications, and workflows.
- TRANSITION TO THE PASSWORDLESS SCENARIO: As new authentication methods are implemented, perform awareness and education campaigns for users. Likewise, validation is important to ensure that no user needs passwords and password authentication can be disabled.
- ELIMINATION OF PASSWORDS FROM THE IDENTITY DIRECTORY: Make sure that in the identity directories no longer persist any form of the password. This stage marks the achievement of the long-term security goal of a truly password-less environment.
If your company uses Exchange Online, you should read this
Effective October 1, 2022, Microsoft will begin to permanently disable Basic Authentication for Exchange Online in all Microsoft 365 tenants regardless of usage, except for SMTP Authentication.
Microsoft is removing the ability to use Basic authentication in Exchange Online for Exchange ActiveSync (EAS), POP, IMAP, Remote PowerShell, Exchange Web Services (EWS), Offline Address Book (OAB), Outlook for Windows, and Mac. They are also disabling SMTP AUTH in all tenants in which it’s not being used.
This decision requires customers to move from apps that use basic authentication to apps that use Modern authentication. Modern authentication (OAuth 2.0 token-based authorization) has many benefits and improvements that help mitigate the issues in basic authentication. For example, OAuth access tokens have a limited usable lifetime, and are specific to the applications and resources for which they are issued, so they cannot be reused. Enabling and enforcing multi-factor authentication (MFA) is also simple with Modern authentication.
In September 2021, Microsoft announced that effective October 1, 2022, they will begin disabling Basic authentication for Outlook, EWS, RPS, POP, IMAP, and EAS protocols in Exchange Online. SMTP Auth will also be disabled if it is not being used. See full announcement here: Basic Authentication and Exchange Online – September 2021 Update.
The best way to overcome this change is to implement a comprehensive passwordless strategy, which will not only support your organization in facing this change, but also enable it to strengthen its security posture and be at the forefront of the best practices in the market.
Synergy Advisors’ team of experts has developed a package of fully customizable passwordless solutions according to your specific needs. Fill the form below or e-mail us at [email protected] to get a free demo and consulting session where we can show you the best way to start your password elimination strategy.
Password Independence Day is here!
Synergy Advisors is ready to support your organization in this transformation. Contact us below.



