Optimizing Enterprise Security with the New Copilot for Security Monitoring Dashboard
Ushering in a New Era of Security Monitoring
In today’s rapidly evolving threat landscape, optimizing security resources is essential—not only to reinforce security but also to avoid unnecessary costs. Microsoft’s new Copilot for Security monitoring dashboard delivers advanced visibility into Security Compute Units (SCUs) usage. This powerful tool enables security teams to make real-time, data-driven decisions that optimize their investment while strengthening their security posture.
What are Security Compute Units?
Security Compute Units (SCUs) are a measure of computational resources used when engaging with Copilot for Security. Each time a request is processed, such as when a user initiates a prompt or a security analysis, SCUs are consumed based on the complexity and type of interaction.
SCUs serve to quantify and monitor resource usage, helping organizations control costs and allocate resources efficiently. By understanding SCU consumption patterns, security teams can optimize their use of Copilot for Security, ensuring that critical security functions are supported while avoiding overconsumption.
Advanced Visibility for Optimal Security Management
The new monitoring dashboard offers a detailed view of Copilot for Security usage across the organization. This includes a comprehensive perspective on SCU consumption, enabling security teams to identify peak usage patterns, analyze user activity, and make strategic adjustments that enhance both efficiency and effectiveness.
Key features of the dashboard:
- Real-Time Monitoring: View Copilot for Security usage across your organization. From hourly to daily consumption, the dashboard identifies peak usage times, enabling proactive SCU allocation planning.
- Detailed Usage Analysis: Examine specific usage patterns, including which plug-ins are used, who uses them, and how they are deployed. This level of detail helps you tailor your Copilot configuration, ensuring that resources are allocated where they’re most impactful.
- Eliminate Inefficiencies: Detect and address inefficiencies in your security operations. Learn how to optimize prompts and adjust configurations to reduce SCU consumption without compromising response effectiveness.
Resource Control: Optimize SCUs by setting access limits and dynamically adjusting resource allocation during peak and low usage periods. This ensures precise resource management and improved cost planning.
SCUs serve to quantify and monitor resource usage, helping organizations control costs and allocate resources efficiently. By understanding SCU consumption patterns, security teams can optimize their use of Copilot for Security, ensuring that critical security functions are supported while avoiding overconsumption.
Microsoft’s new usage dashboard helps organizations track SCU usage in real-time, offering a detailed breakdown of where SCUs are spent, who is utilizing them, and how resources can be better managed to meet security needs without excessive spending.
Strategic Use of Monitoring Insights
Let’s say your organization uses predefined “promptbooks” to address common incidents. With the monitoring dashboard, you can detect SCU consumption peaks at specific times, adjusting to prevent overuse while maintaining effective incident response.
This type of optimization enables organizations to adapt their security strategy flexibly and precisely.
You can access the Copilot for Security usage dashboard here: https://securitycopilot.microsoft.com/usage-monitoring, where you will see something like the screenshot below.
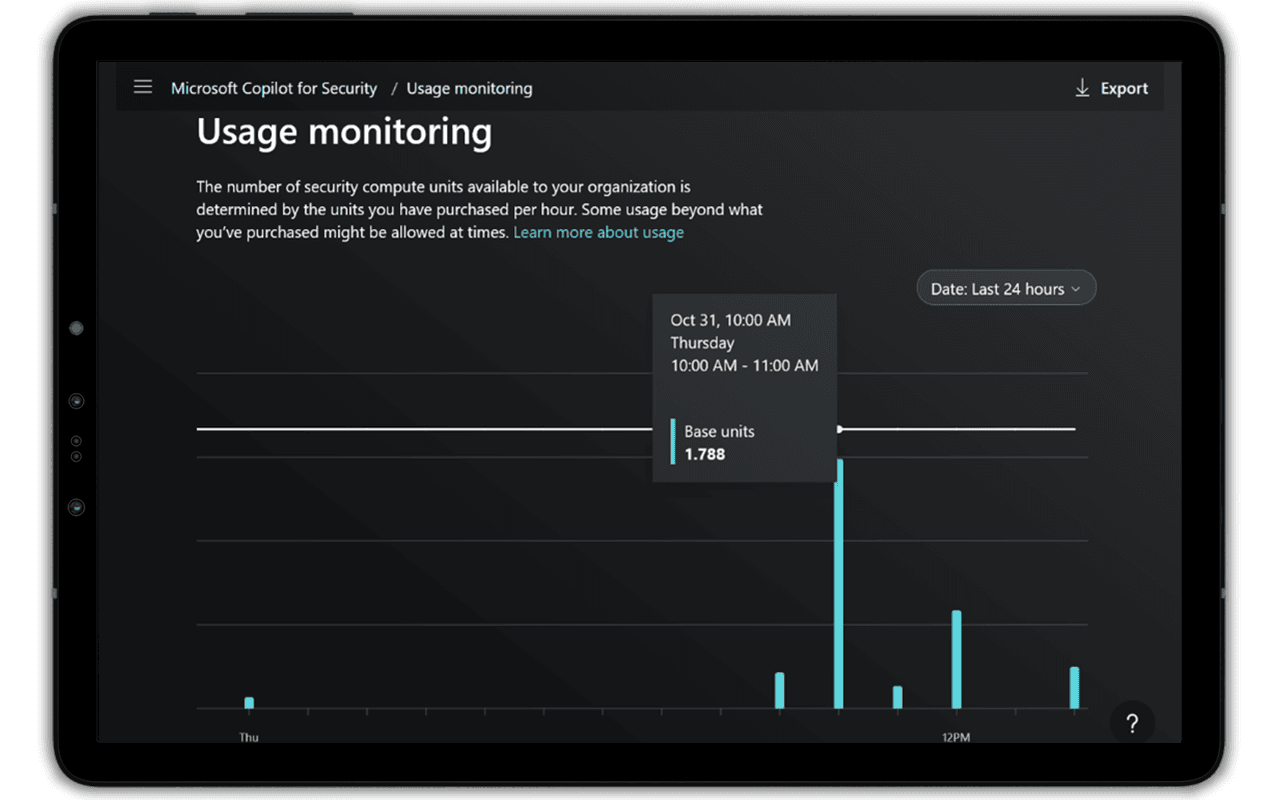
From here, we can see a histogram showing the amount of Security Compute Units (SCUs) that were consumed each hour for the last day. We can observe usage spikes to help us understand peak SCU consumption times and plan our SCU allocation.
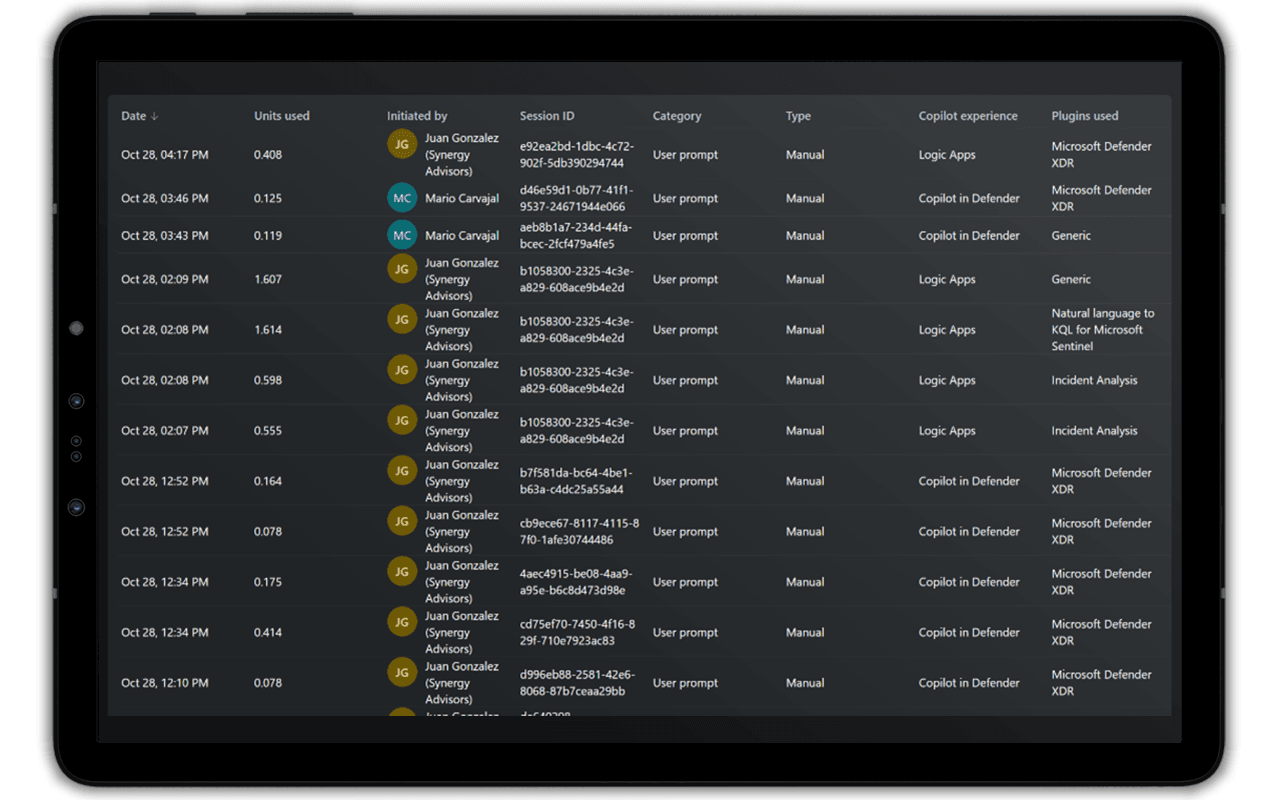
But what if we need to know which user consumed the SCUs? Or what plug-ins were invoked during the prompt execution? Or even how the prompt was invoked?
With the new usage dashboard, you can drill down on usage patterns and understand exactly how Copilot for Security is used. We can now see additional details, such as the exact number of SCUs used in a session, who initiated the interaction, the Copilot experience from which the prompt or interaction was initiated (standalone or embedded experience), which plug-ins were used during the interaction, the usage type, and the category:
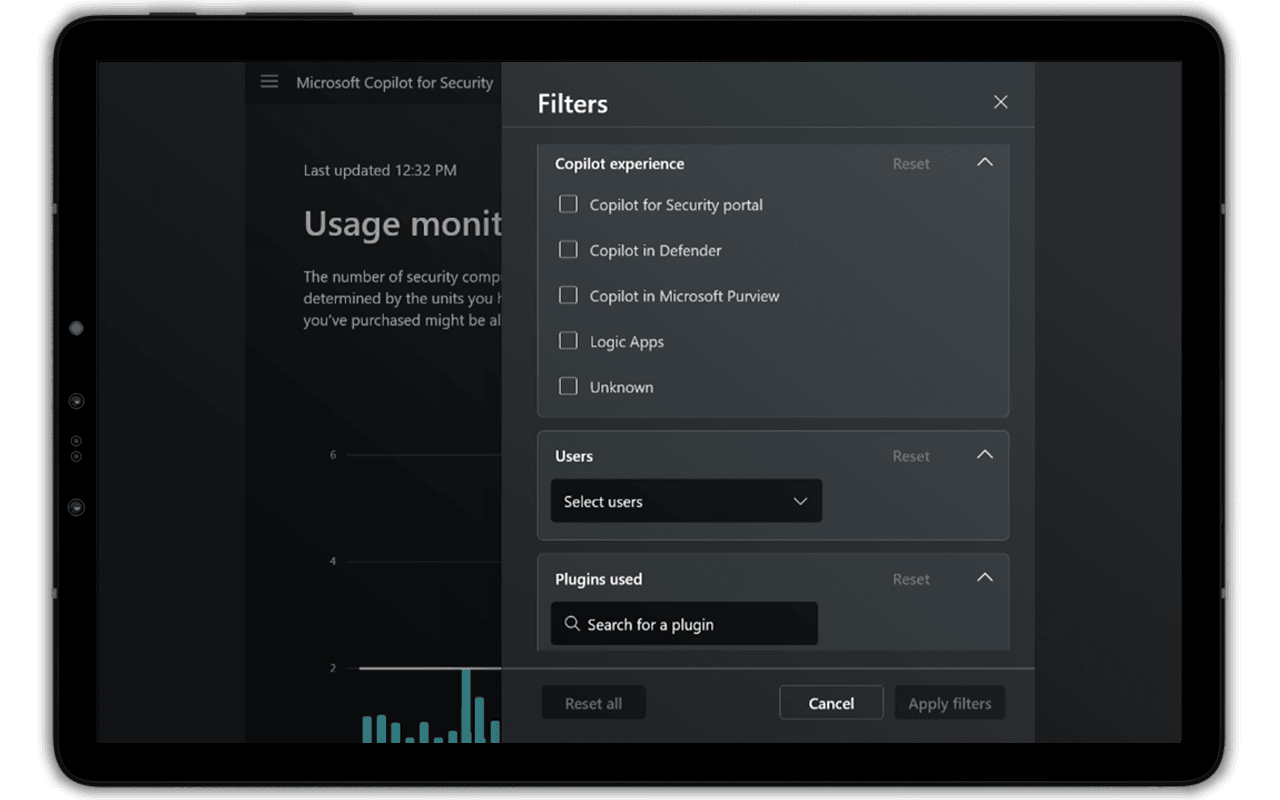
But let’s say we want to understand usage patterns for a specific user, a specific plug-in, or Copilot experience. With the new dashboard, you can filter the usage logs by users, plug-ins used, experience, type, and category:
By using this new dashboard, organizations can make informed decisions to enhance their security operations, eliminate waste, and maximize their investment in Copilot for Security.
Optimizing your security resources will be a pivotal step in adopting Copilot for Security to really take advantage of its benefits while minimizing waste and overconsumption of critical security compute units. With the new usage and monitoring dashboard for Copilot for Security, organizations should start leveraging these insights today to achieve a more efficient and cost-effective adoption of Copilot for Security.
Smart Adoption of Copilot for Security
The introduction of Copilot for Security’s new monitoring dashboard paves the way for a more efficient and cost-effective approach to managing security resources. With Synergy Advisors as your partner, your organization can not only leverage this technology but also maximize its value through an optimized security strategy aligned with your business goals.
How Synergy Advisors Helps You Maximize the Value of Copilot for Security
Optimal Copilot for Security adoption requires planning, continuous monitoring, and strategic integration. Synergy Advisors offers a suite of services designed to help organizations implement and maximize the value of this tool, ensuring an efficient ROI and a strengthened security posture:
Interactive sessions where security teams explore and directly experience Copilot’s capabilities in a controlled environment, gaining practical familiarity with the technology. Read more
Collaborative workshops where we work together to design a Copilot for Security implementation tailored to your organization’s unique needs and structure. Read more
Pilot implementations showcase how Copilot for Security integrates into your existing systems, allowing you to assess its value and effectiveness before a full rollout. Read more
A controlled rollout of Copilot for Security, where we guide your team through the initial adoption and SCU optimization, configuring settings to achieve the best possible outcomes. Read more
For organizations seeking an advanced adoption approach, Pilot Plus includes extended support and detailed monitoring, maximizing your investment in Copilot for Security with strategic management and tailored recommendations. Read more
With these services, Synergy Advisors positions itself as a strategic partner in a Copilot for Security adoption that strengthens your organization’s security while optimizing resource use.
Ready to maximize your investment in Copilot for Security?
Contact us today to learn how Synergy Advisors can help elevate your security strategy to the next level.



