SENSITIVE INFORMATION:
HOW TO TURN A COSTLY CHALLENGE INTO EFFECTIVE MANAGEMENT?

Today, more than ever, organizations face challenges to discover and protect sensitive information. The pandemic forced many organizations to accelerate their digital transformation, including actions such as migrating processes and applications to the cloud, implementing technologies as a service (IaaS, PaaS, SaaS, DaaS), and adopting a hybrid work model.
We are now faced with a scenario in which employees have access to various communication channels, unprotected devices, and sensitive information, without the security controls that enable them to correctly manage those files, with no good practices in the protection of information, and without at least basic analytics that support the information security departments in decision-making. This is how the employee becomes the weakest shackle in the security chain. Organizations have suffered so many attacks to their information and many have begun to shift the focus of their security strategies from the external factor to the internal user.
But this does not exempt external factors from being a threat to information; it is critical to establish and execute tactics that address and monitor everything that happens with sensitive information, inside and outside the perimeter.
What types of data are sensitive?
While each organization will define sensitive information differently, there are some commonalities that we can identify. Sensitive information constitutes all data that may belong to employees, business partners, suppliers, customers, and users that is confidential or could mean harm if it were disclosed. Some examples of common sensitive data types include the following:
- Credit card numbers
- Social security numbers
- Personal information such as address and date of birth
- Intellectual property
- Confidential medical information
- Patents
- Business plans
- Customer information
- Financial data
This type of data can come from all levels within the organization and from partners in the value or supply chain, which is why controlling what, who, how, when, and where people can access information becomes a manual, laborious, and excessively expensive task. Yes, it seems like a difficult task, but then, what is the best posture? Do we ignore it or do we have to take control of the situation?
The price of staying in the comfort zone
At the beginning of March 2022, Microsoft published an article about the most common challenges that organizations face when protecting sensitive information. These can include security breaches that generate high costs, negative impacts on the price of the actions and fines imposed for violations of regulations such as GDPR and CCPA, as well as loss of reputation by customers who are victims of identity theft, credit card fraud, and other malicious activities resulting from such breaches (Microsoft shares 4 challenges of protecting sensitive data and how to overcome them – Microsoft Security Blog). In 2021, the number of data breaches increased by 68% (the highest in 17 years) at an average cost of $4.24 million each (Cost of a Data Breach Report 2021, Ponemon Institute, IBM. 2021). Likewise, the article indicates that around 45 million people were affected by medical data breaches, triple the number affected just three years earlier (Cyberattacks Against Health Plans, Business Associates Increase, Jill McKeon, HealthITSecurity xtelligent Healthcare Media. January 31, 2022).
A journey to effective protection
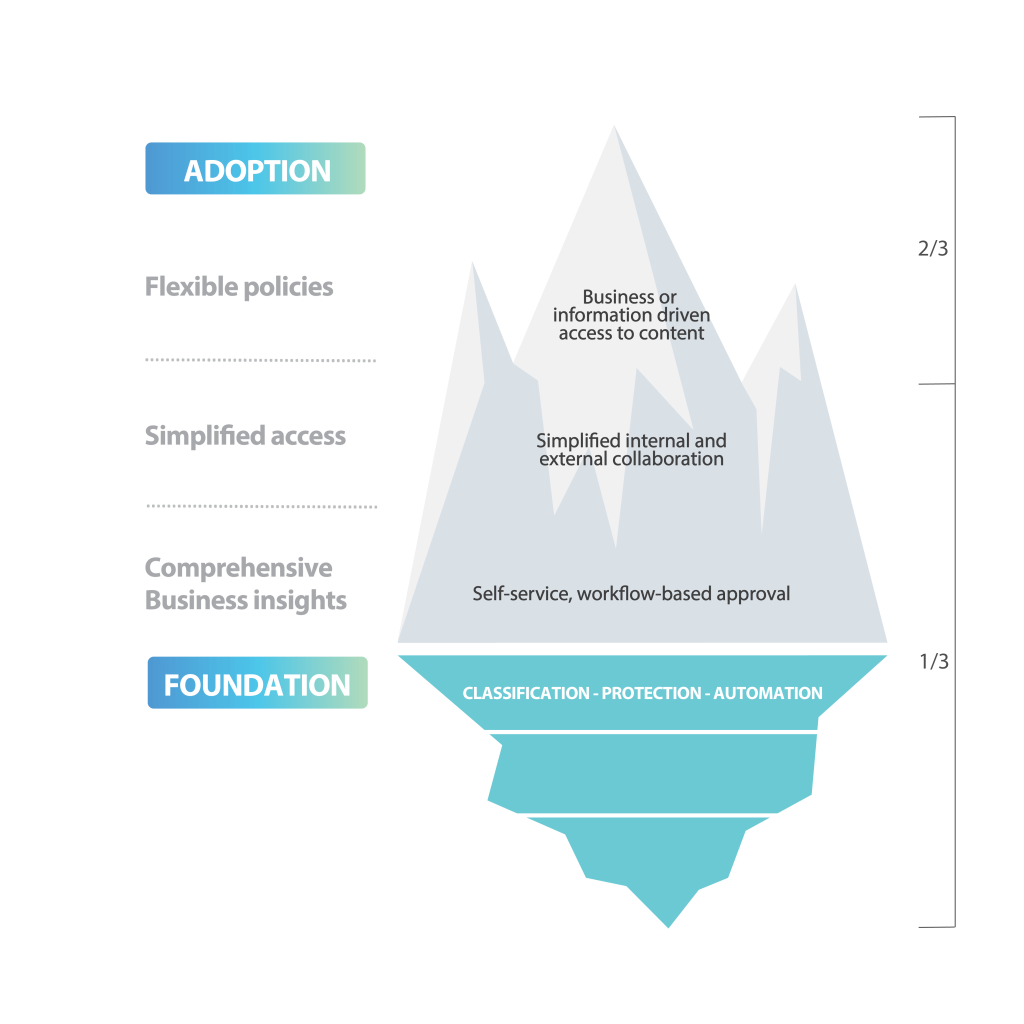
Given this scenario, the right choice is to build a security strategy that, in addition to helping protect the company’s sensitive information, establishes and strengthens the governance of identities and data to help Chief Information Security Officers build and maintain control over the actions that are executed regarding sensitive information, with personalized policies, automated processes, and rich data to support decision making.
To achieve this, we must undertake a journey that includes a detailed stop at each station along the way. However, it is not enough to want to make the trip; it is vital to select a conveyance (the solution) that accomplishes the expectations of the traveler (the organization) and that has the technical and technological capabilities required to overcome the obstacles along the way, and arrive at the destination where a welcome cocktail awaits (the effective and proactive protection of sensitive data).
Introducing E-Inspector: the next generation jet
E-Inspector is a solution developed by Synergy Advisors with advanced capabilities to facilitate the automated discovery, audit, and protection of sensitive data, stored in the cloud or on-premises. E-Inspector is the next generation jet that constitutes the appropriate conveyance for the secure journey to the protection of sensitive data.
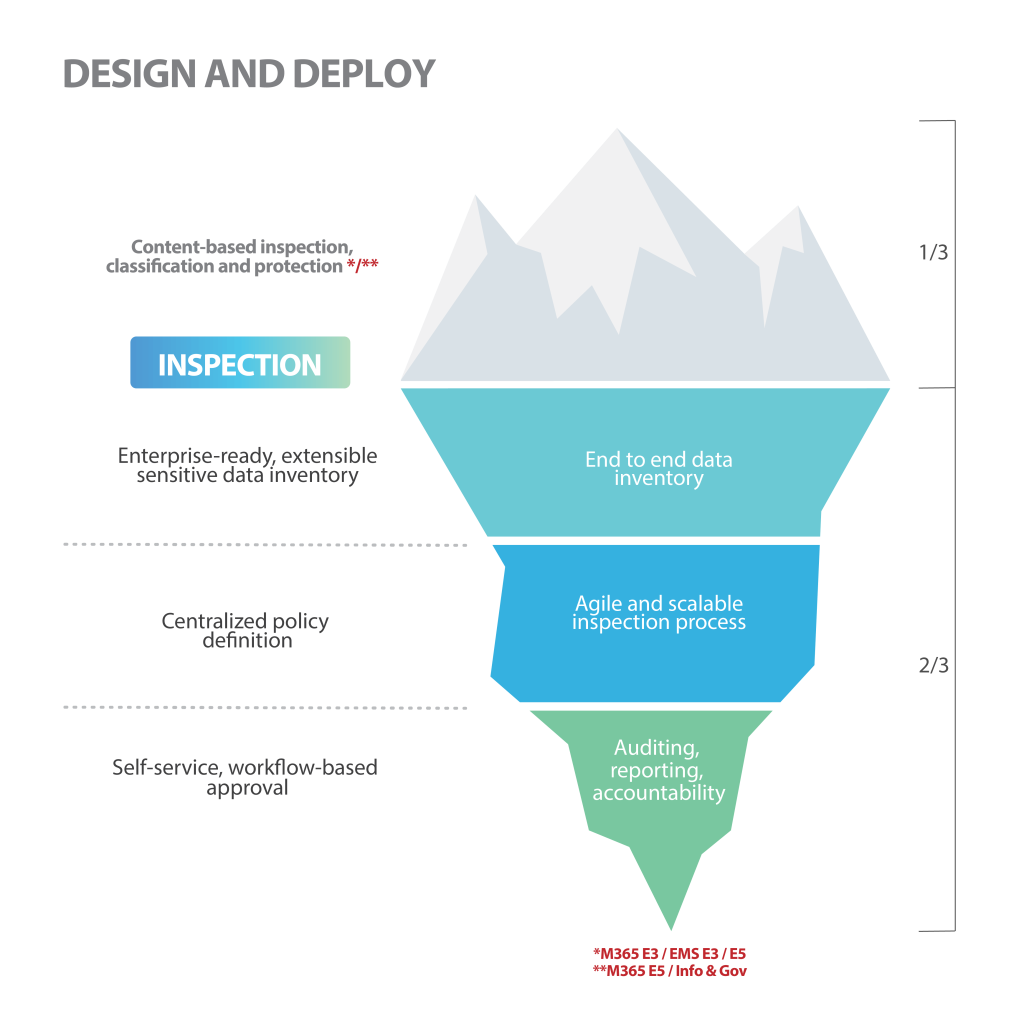
This solution has protection capabilities based on MIP (Microsoft Information Protection) technologies that enable you to take control of the data no matter where it is, and guide the protection strategy through 3 stations that make up a secure journey:
- Discovery: E-Inspector identifies where your sensitive files are located and provides data about the number, type of files, and their attributes (owner, time, last modification, etc.).
- Assessment and audit: Classifies data and metadata and inspects content for sensitive information.
- Protection and response: Automatically applies the required encryption according to the content of the document. This automates and streamlines the entire process, and builds a detailed inventory of the repository, including which files were encrypted. Likewise, it enables changes to be made to the analyzed files in terms of protection, classification, and content protection policies and direct actions on the files such as copying, moving, deleting, and changing owners without removing the encryption of the files.
Through the execution of the previous 3 phases, E-Inspector comprehensively optimizes and automates the management of sensitive information, including an information governance component that acts on identities and data and enables the definition of centralized policies to support inspection capabilities in the cloud and on-premises, while offering data-rich inventory, workflow-based actions that go beyond content protection, and a reporting and analytics layer delivered through Power BI.
How to start the journey to proactive protection
Even at rest, data is dynamic with multiple servers and locations, multiple access vectors and actors, multiple copies of the data, and multiple administrators. Maintaining control is complex, so discovering what kind of data, where it is located, and who is accessing it is the most effective first step in developing a protection and mitigation strategy for organizations of all sizes and industries. Synergy Advisors brings its EDOs (E-Suite Discovery Offerings), an E-Inspector offer that enables inventory and analysis of data at rest to establish a risk protection and mitigation plan.
The E-Inspector EDO is executed with the following process:
- Review and installation: An expert analyzes the organization’s policies and infrastructure before installing the E-Inspector and E-Visor technologies.
- Scan data at rest: E-Inspector, in conjunction with MIP, analyzes 1 data at rest repository. Results and analysis are presented through comprehensive E-Visor reports.
- Findings and action plan: Joint review with the company of the analyzed results, with a prescriptive action plan in 2 efficient 1-hour meetings, offering the company a high return on investment at a low cost.
Important note: The E-Inspector solution runs in the organization’s Azure tenant, so the analyzed files and the data collected is always under the control of your organization.
The prerequisites to access the offer are minimal, since premium subscriptions are not required and the work can be performed with the free version of Microsoft Azure (Azure Pass) and existing MIP licenses, even a trial version. In this way, the offer enables access to the following options:
- Option 1:
– Space: Up to 1 TB of data
– Total time: 1 week
– Time required from the client: 6 to 10 hours in 3 meetings
- Option 2:
– Space: Up to 5 TB of data
– Total time: 2 weeks
– Time required from the client: 10 to 12 hours in 4 meetings
Offer deliverables:
- Action plan: co-creation of 1 plan for your specific scenarios, analysis of potential impact, and mitigation steps.
- Files inventory: complete file inventory and data metrics through the E-Visor platform.
Download below:
The journey to implementing an effective sensitive data protection strategy is not easy, but Synergy Advisors is here to help organizations in this process.
Are you ready to effectively protect your organization’s sensitive data?