
Driving compliance success while maximizing M365 Copilot – Part I
In this blog post series, we introduce how Synergy Advisors solutions and experts can help your organization quickly get ready to deploy Microsoft 365 Copilot in your organization while strengthening your data compliance and protection! We will show you how to prepare your on-premises and other cloud data repositories for the potential data governance challenges that unstructured data can bring.
AI is everywhere! This is true today, not sometime in the future. A year ago, we heard this was coming… and now it is a reality. Above and beyond the “trending” aspect, we need to recognize that users see so many benefits from solutions like Microsoft 365 Copilot and those benefits enable the organization to get the most out of their investments in AI:
Optimized collaboration
- Easy data search across all collaboration repositories
- Meeting summaries
- E-mail and document crafting and summarization
While many of these amazing capabilities can provide tremendous benefits to the business, many organizations may have to prepare their environment to get themselves ready to get the most out of Copilot without taking the risk of data exfiltration.
RISK
AI can do things at the speed no human can do; however, organizations must do their due diligence before they can simultaneously meet both the CIO and CISO objectives. The collaborative and efficiency benefits provided by Copilot are game changers. At the same time, they cannot come at the cost of oversharing of your sensitive information, potentially across the entire organization and beyond!
Let’s look at the following scenarios:
A person asks Copilot about “business re-orgs/upcoming strategic plans/firing situation” and, if proper controls are not in place, the requestor might be able to see a confirmation of upcoming personnel decisions with specific details, including names, performance reviews, and more.
A person asks Copilot about “compensation details” and, just like the example above, if proper controls are not in place, requestors can see as many details as they ask for in the prompt, including salaries, bonuses, financial numbers, and names.
– N – Serve yourself, yes you got it! Through any “creative” prompt to Copilot, a requestor can surface sensitive and confidential information that should not be shared with that person
But what are the current security controls that could mitigate these scenarios and prevent leaked and oversharing of sensitive information?
Existing Mitigation Strategies:
People will not see information in Copilot’s answer from content stored in repositories that the user does not have permission to access
Questions:
- Has the organization implemented user access governance?
- Has the group management and, more importantly, group nesting implementation been reviewed, tested, and documented so you can identify potential changes?
- Do you grant anonymous or “anyone” (all tenant) access or B2B access to data at rest?
People will not see information in Copilot’s answer from content where the user does not have encryption permissions to the file (typically encrypted with Purview IP)
Questions:
- Does the organization have granular labels implemented across M365?
- Is all data labeled AND encrypted?
- Adding visual markings through headers and footers is not enough
- Even if a document is encrypted, Copilot may still use those files on behalf of the user
- Is the user allowed to export data from those documents? If so, Copilot can return those results
- Is the group management and, more importantly, group nesting reviewed, tested, and documented so you can identify potential changes and risk within your data classification and the people allowed to access certain data labels?
- Is all data labeled AND encrypted?
- As of this writing, you cannot set exceptions for paths to be “scanned” by Copilot; we hope Microsoft provides this capability in the future.
Bottom line, we are in looking at a critical trade off between business, technology, and compliance.
Copilot can clearly do what is “fair” and right:
People with “explicitly” defined access can receive responses to the queries listed above…. But this makes a HUGE assumption of your environment. What is sensitive data to your organization, who should be able to see it, and is that configured correctly across your Microsoft 365 platform? Can any organization really assume that their environment is perfect and every file (while in use, in motion and at rest) has authors, contributors, and administrators who have set the right access and content permissions? And yes this applies across M365 and to wherever you keep unstructured documents and other files…

Well now what can you do? Read the rest of this blog and the following series for the strategy that Synergy Advisors, an information protection and governance consulting company with more than 20 years of experience in the market working with top 100 accounts across multiple countries and segments, can recommend to QUICKLY assess and remediate your environment in preparation for Microsoft Copilot.
Strategy overview
The proposed strategy listed below is covered by the following three stages where you can:
Understand your status, do NOT assume all is good; revalidate and test your current situation
- For this, we introduced an assessment tool that accelerates the identification of sensitive information and its location and who has access to it
Once identified, improve your data protection platform by applying the corresponding mitigations such as stronger ACLs, content labeling, and encryption
- You can prioritize, for example per content/business unit, so that you can speed up the co-pilot roll out this way!!!
- Luckily, we have a solution that can be used to improve, identify, remediate, move, protect, and archive data according to your needs, leveraging Synergy Advisors solutions to achieve this goal faster than manual analysis and based on business rules
- For this, see the 2nd post [Coming soon].
You may ask yourself then, if these two activities should be executed regularly or ideally in near real time, well yes, we will cover how to identify every new, used, or edited file and to re-evaluate the conditions and validate if they may be exposing data.
- For this, see the 3rd post [Coming soon].
Step I - Assess and Discover Activities [Introducing the Copilot Data Governance Assessment]
In the Copilot Data Governance Assessment [CDGA], our initial step is to validate where your data is and who has access to it. This may sound pretty broad, but the outcome and review tool provides an assertive way to show your business and technical decision makers where you stand protecting your data at rest from a data compliance and access lens.
Objective
Here is where “get to know your data” means you REALLY will get all the details and then be able to weigh the situation
What?
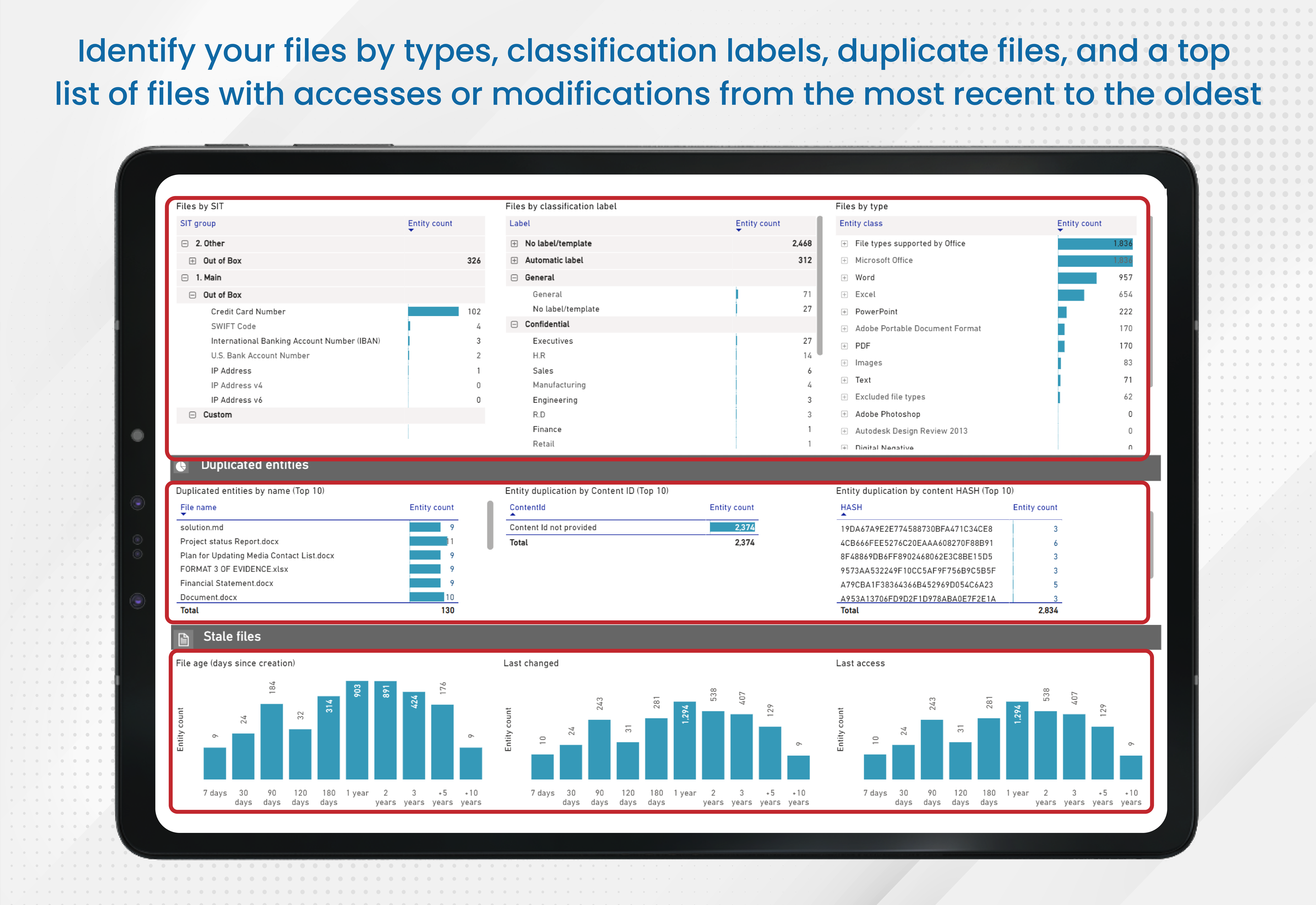
The kind of content (beyond file extensions) people use; you may be surprised by what you find
Where?
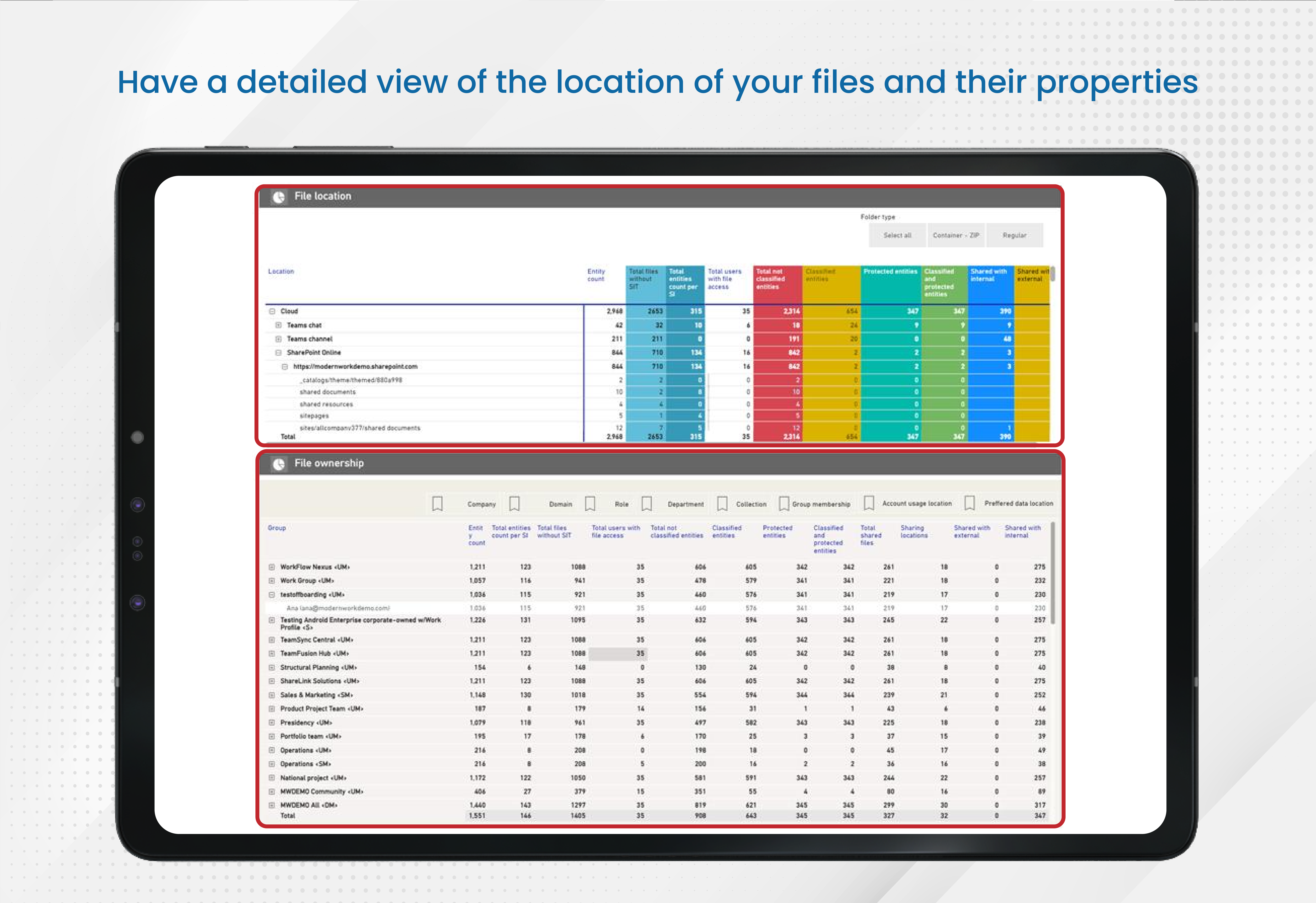
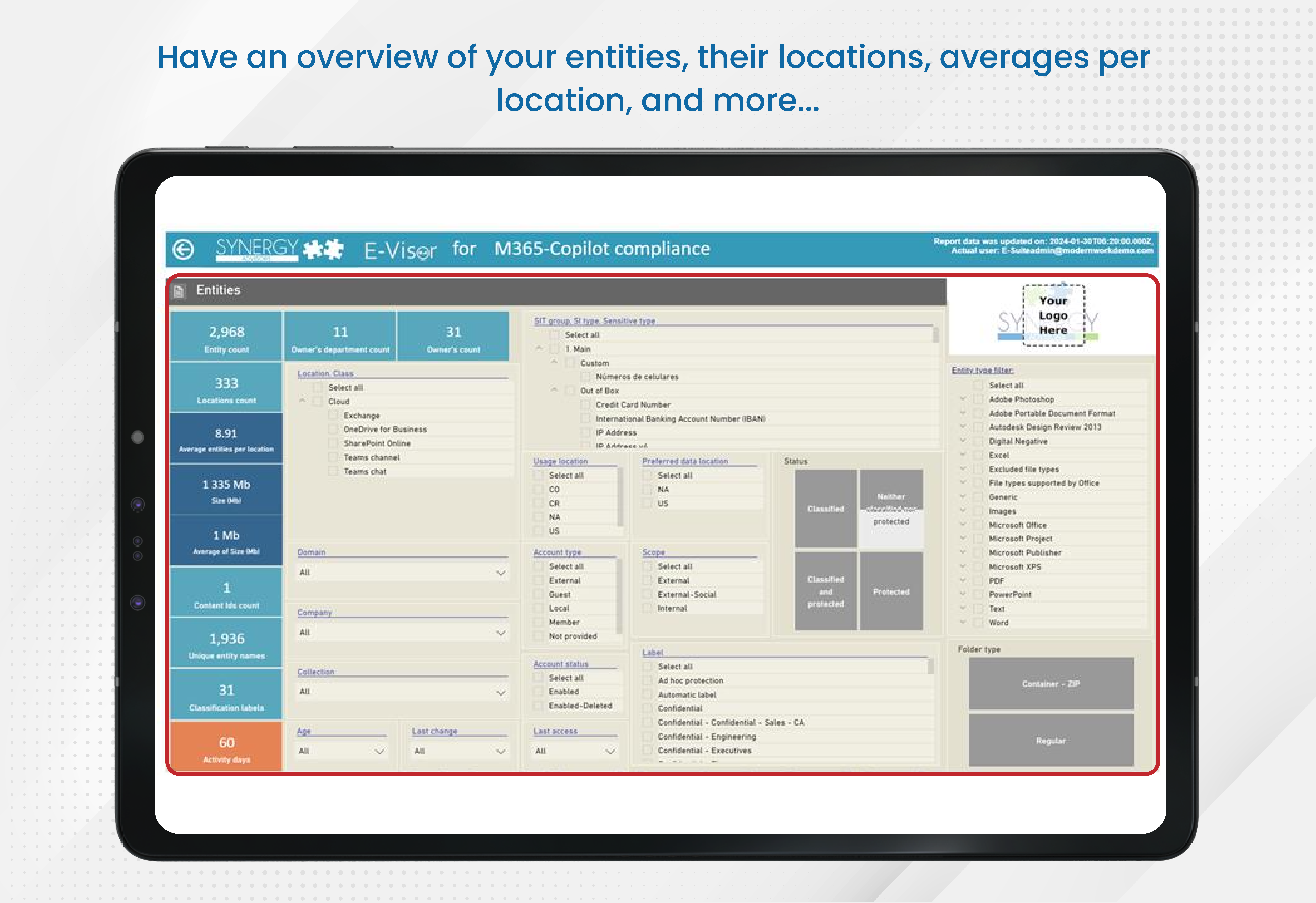
Where this content is located, such as across different repositories, business portals, Teams channels, Teams chat, personal OneDrive, shared with others, and more
Who?
Who has access to it, including the file and the folders; here is where we validate the identity and data governance situation and how Copilot will reply back?
When?
If files have been used and how often there is activity there
Execution
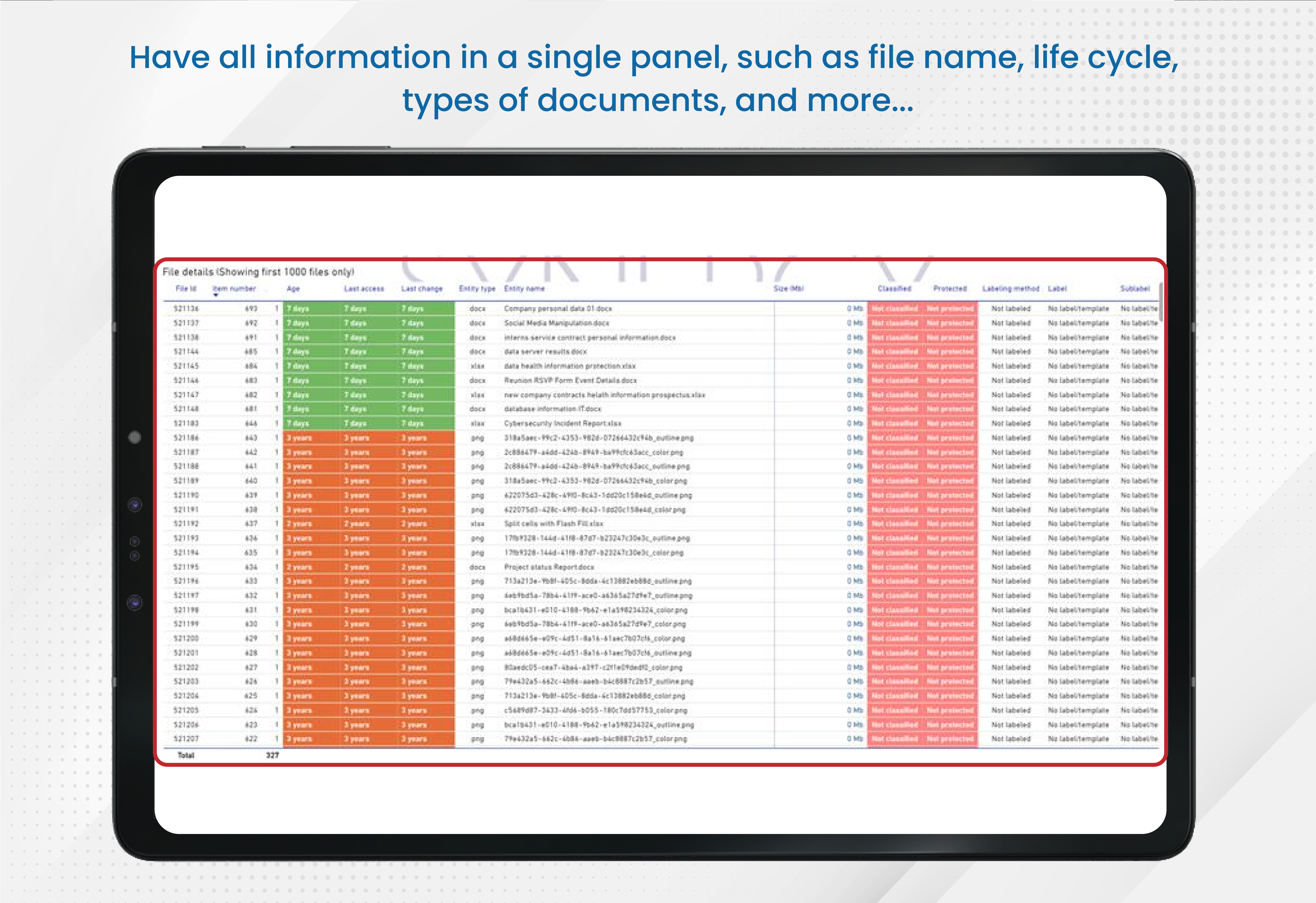
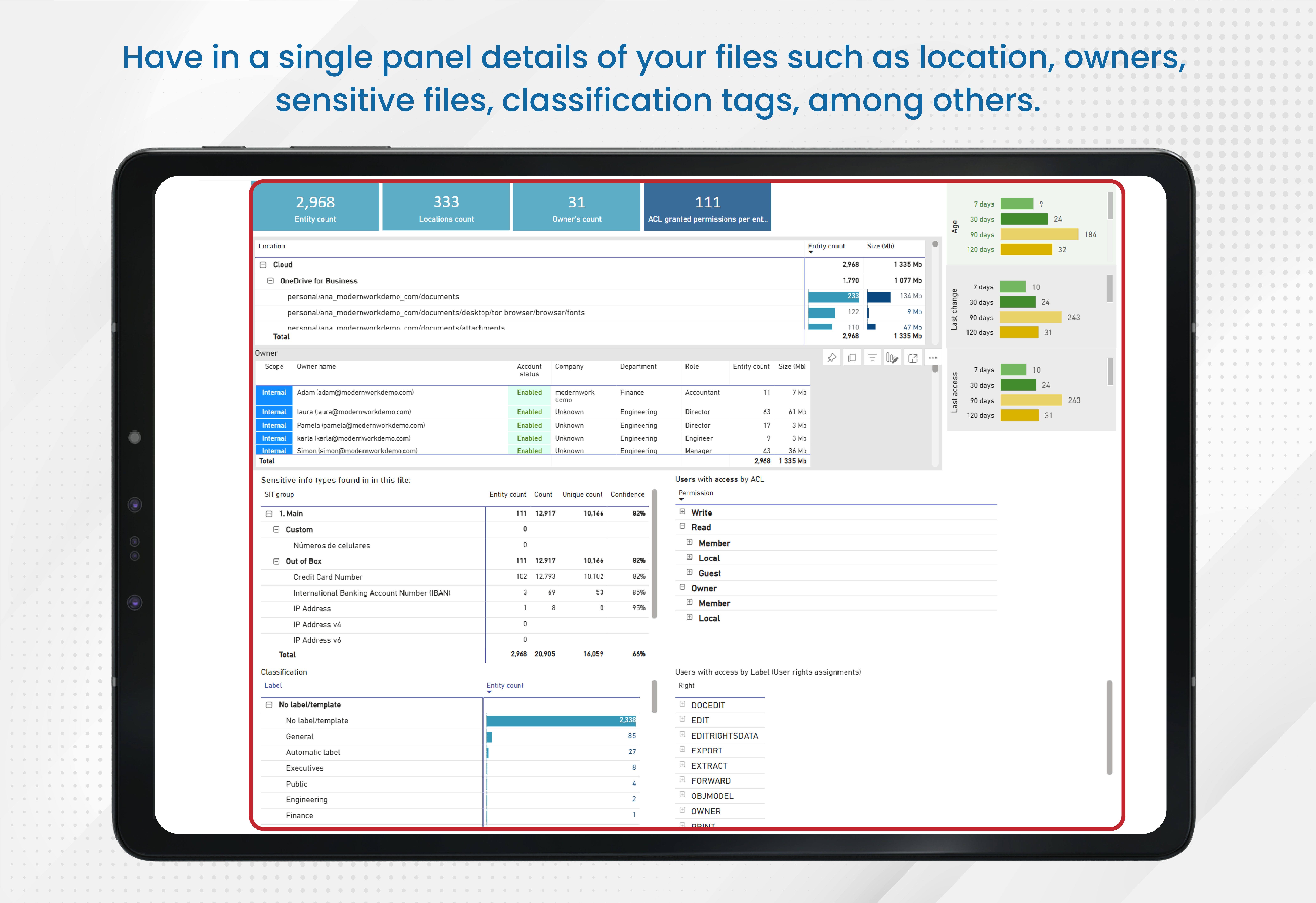
The next step is to deploy our tool directly in your tenant, using Azure resources. This approach ensures that your data, files, and platform details never leave your Microsoft 365 environment. After installation, the tool scans your repositories and provides rich reporting and analytics using PowerBI
Scanning and reporting platform:
Synergy Advisors E-Inspector is used to perform the analysis of the workloads and paths where it will inspect documents content and access
- The solution runs in your Azure subscription. Your files and the reporting data remains in your tenant and Synergy Advisors does NOT have access to this information
Timing and Azure resources (ACR) needed? We provide you a calculator/estimate prior to running the tools according to the scope/repository size.
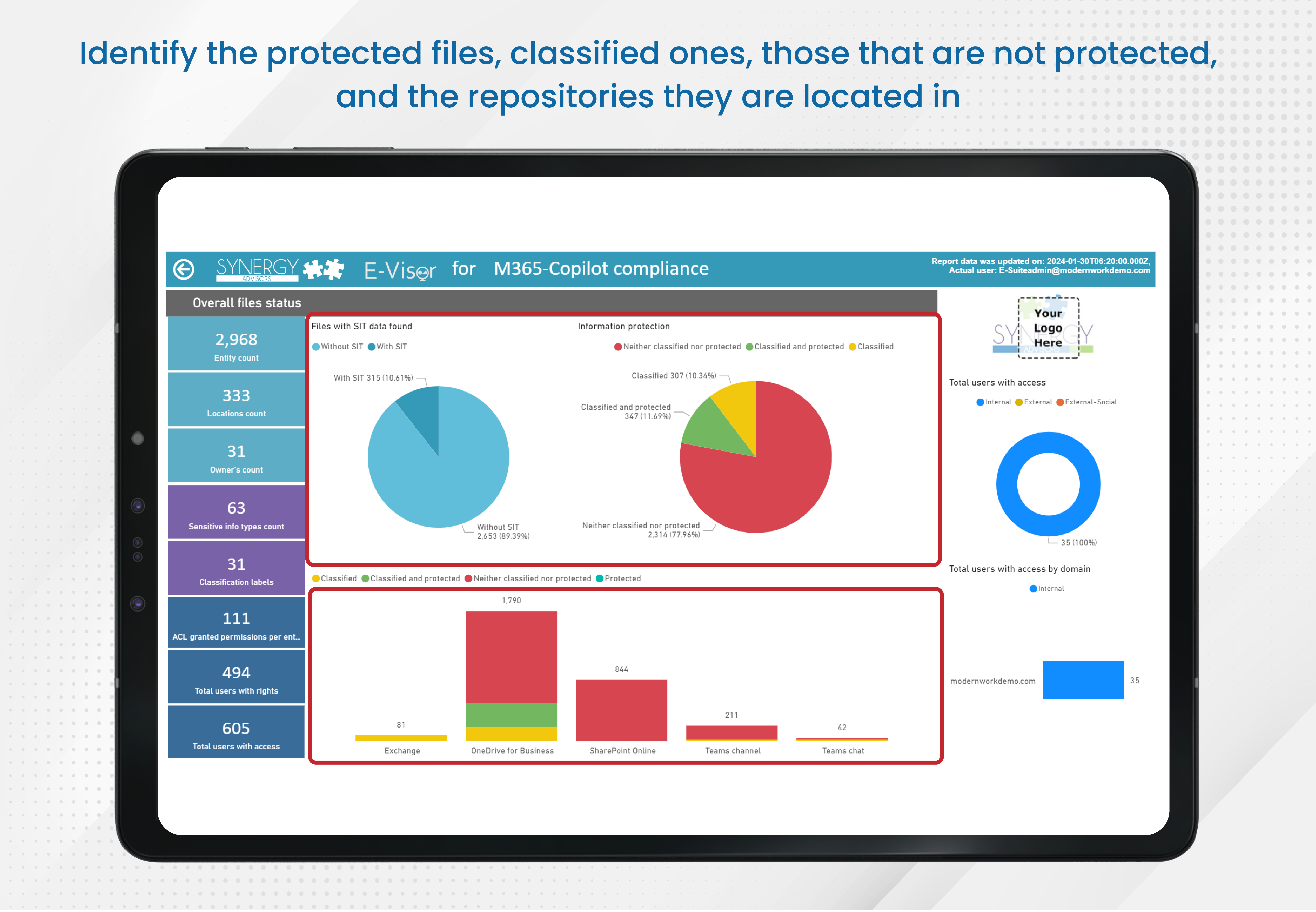
- Once the scan is complete, we can review the information in our E-Visor tool, which leverages your PowerBI Premium to view and analyze the results
- PowerBI provides the perfect way to combine multiple conditions and see the information you need with the ability to filter data using multiple conditions at a time and as needed
- From here you can filter with all the parameters, who has access to your most critical information, who should have access to the content, where it is located, and more
- PowerBI provides the perfect way to combine multiple conditions and see the information you need with the ability to filter data using multiple conditions at a time and as needed
NOTE: For your convenience, access to this report has no expiration; you can retain and use it as much as you want as a point of reference for that one-time assessment.
Findings and recommendations
Lastly, as part of our assistance, one of our compliance architects will go over the findings and provide advice on the corresponding next steps for:
- Files containing SIT info
- Mitigation actions leveraging Microsoft 365 E5 (or similar, depending on your SKU)
- Purview actions such as Auto Labelling and SharePoint Online ACL architecture
- Strategy changes
Next steps
- In case you want to quickly perform specific actions such as:
- Archive old data
- Identify duplicate files
- Move or migrate files to a new, more secure location
- Change workload ACLs
- Apply specific labels and encryption policies
- Or a combination of all the above!
Read the next blog post about how E-Inspector can provide fast remediation to the findings provided in the previous phase – Driving compliance success while getting the most of M365 Copilot – Part 2
MORE INFORMATION – Similar topics
- E-Inspector Overview
- E-Suite Overview
- E-Suite Offerings [E-O]
- E-Suite Discovery Offerings [EDO]
- Others



