
Driving compliance success while maximizing M365 Copilot – Part II [Quick remediation]
In this 2nd blog article in our Microsoft 365 Copilot readiness series, we continue to show you how Synergy Advisors’ solutions and experts can help your organization quickly identify and, more importantly, apply practical controls within your environment to achieve data compliance.
In our previous post, we introduced how tuning your M365 environment can help you scan for and identify where your most important content resides and who has access to it. This includes both the built-in 300+ Sensitive Information Types (SITs) created by Microsoft and well as custom SITs that you can build to discover sensitive information specific to your organization. Perhaps your findings may shock you or perhaps not. Either way, it is better to validate your data state than to leave it to chance. However, identifying where your sensitive data lives and who has access to it is just the beginning. Now what?
There are several different scenarios that may require a drastic change:
Both protected and unprotected files
Both protected and unprotected files
- This includes permissions policies that may need to be revised due to the following most crucial fact (Again, this is a reminder of a critical aspect mentioned from the previous post):
Even if data is protected with Microsoft Purview, users may still be able to access that information and misuse it!
- Read/View permission
- Anyone with such rights can ask M365 Copilot for data and Copilot can return results from the file
- Extract permission
- Anyone with Owner, Co-owner, Co-author, or simply Read + Extract rights can ask M365 Copilot to summarize the information and use it to create a new unprotected document.
Having said that, even if you have documents protected, you may have to optimize both the document-level permissions and also your group nesting strategy
With those considerations in mind, let’s see the different options Synergy Advisors provides you within our E-Inspector solution, beyond the discovery scenarios we looked at in the previous post:

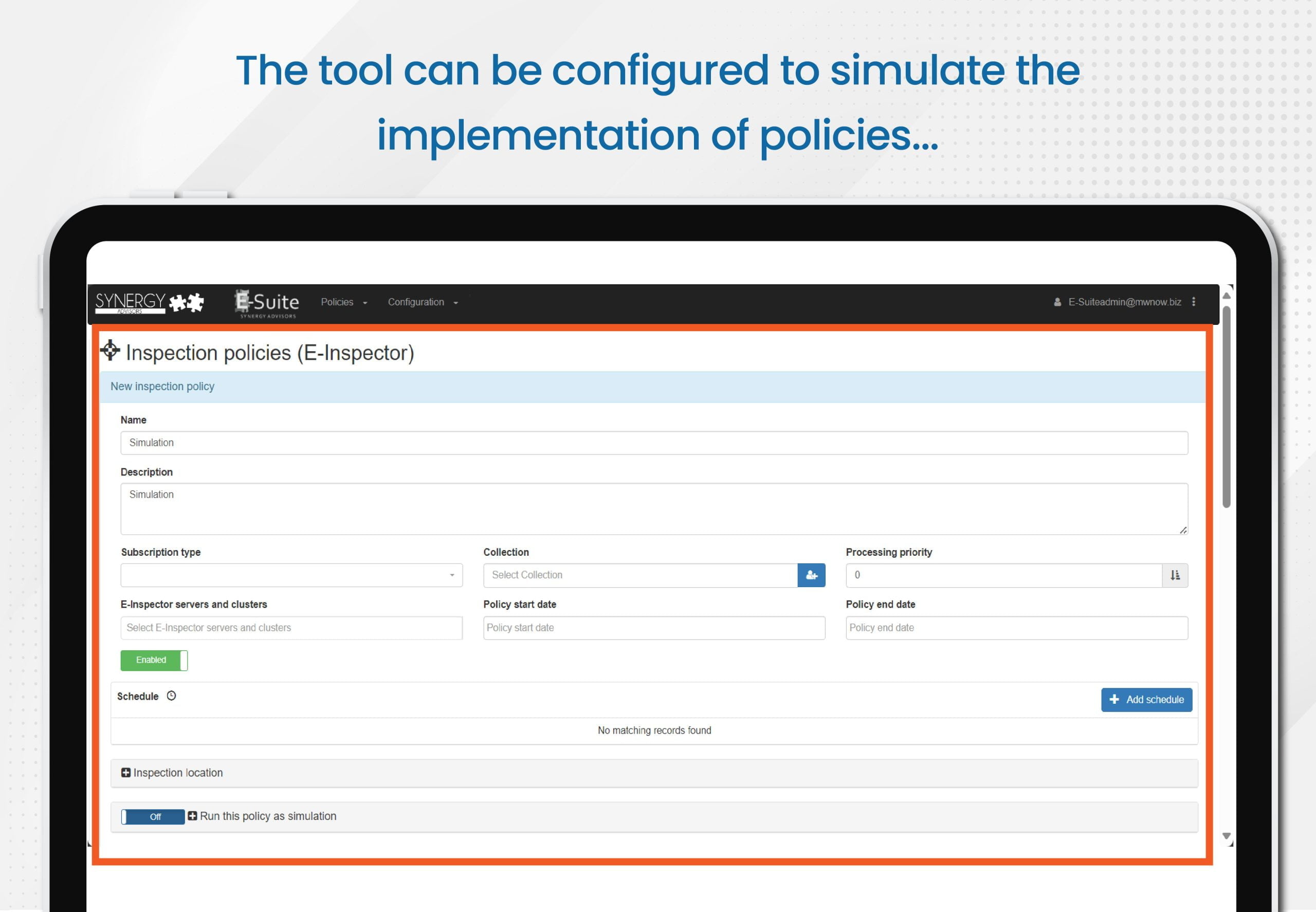
Simulate (what if)
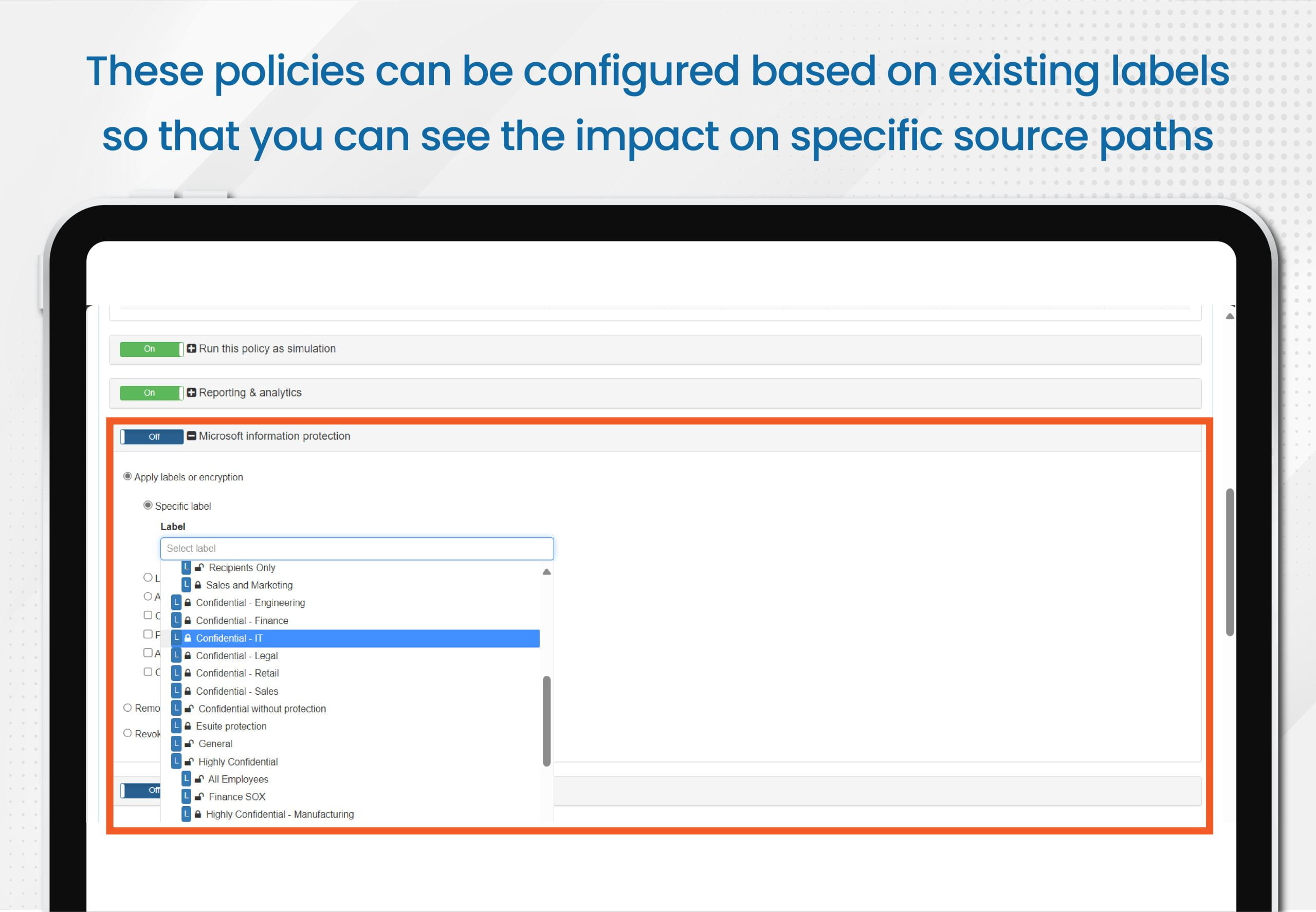
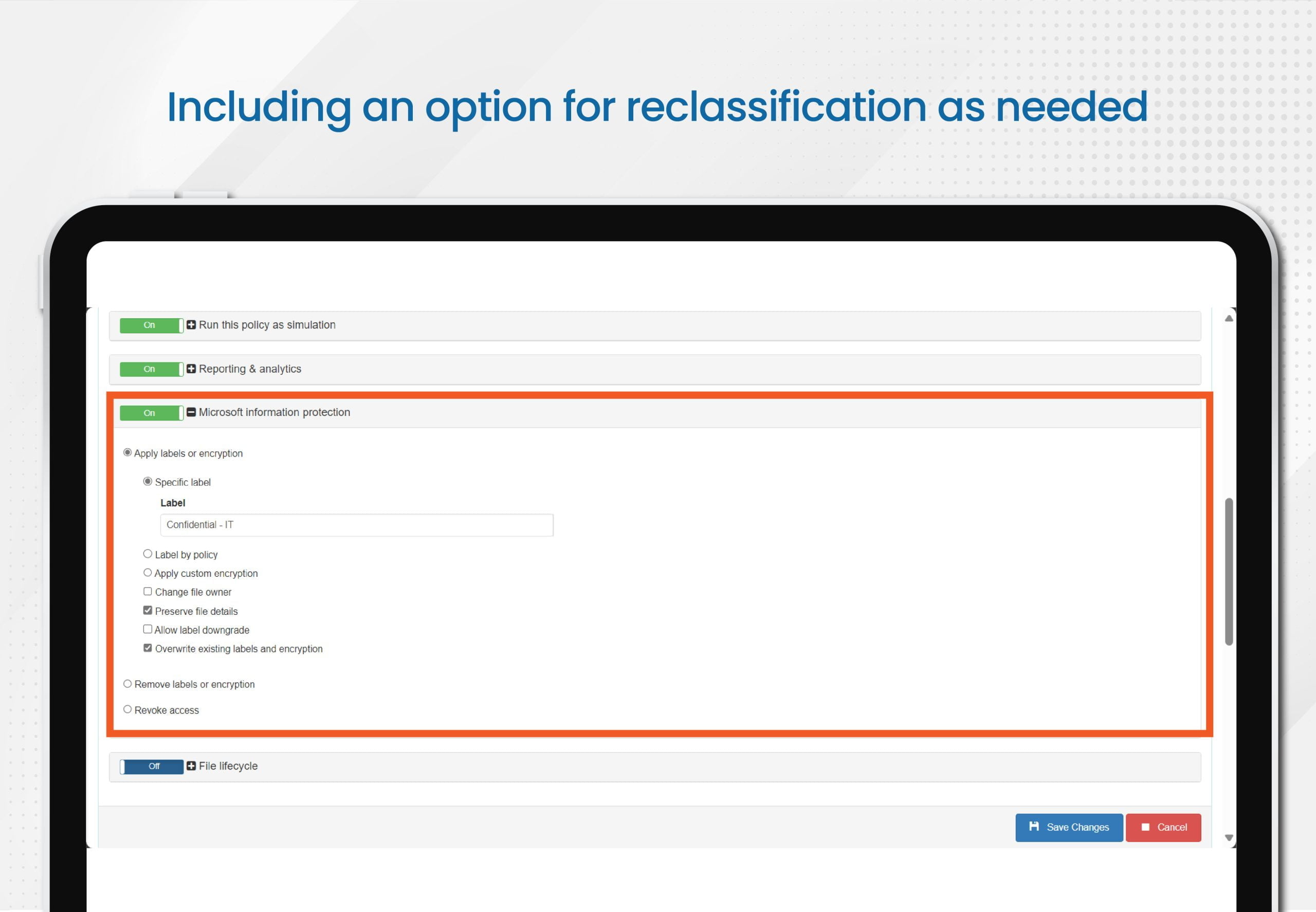
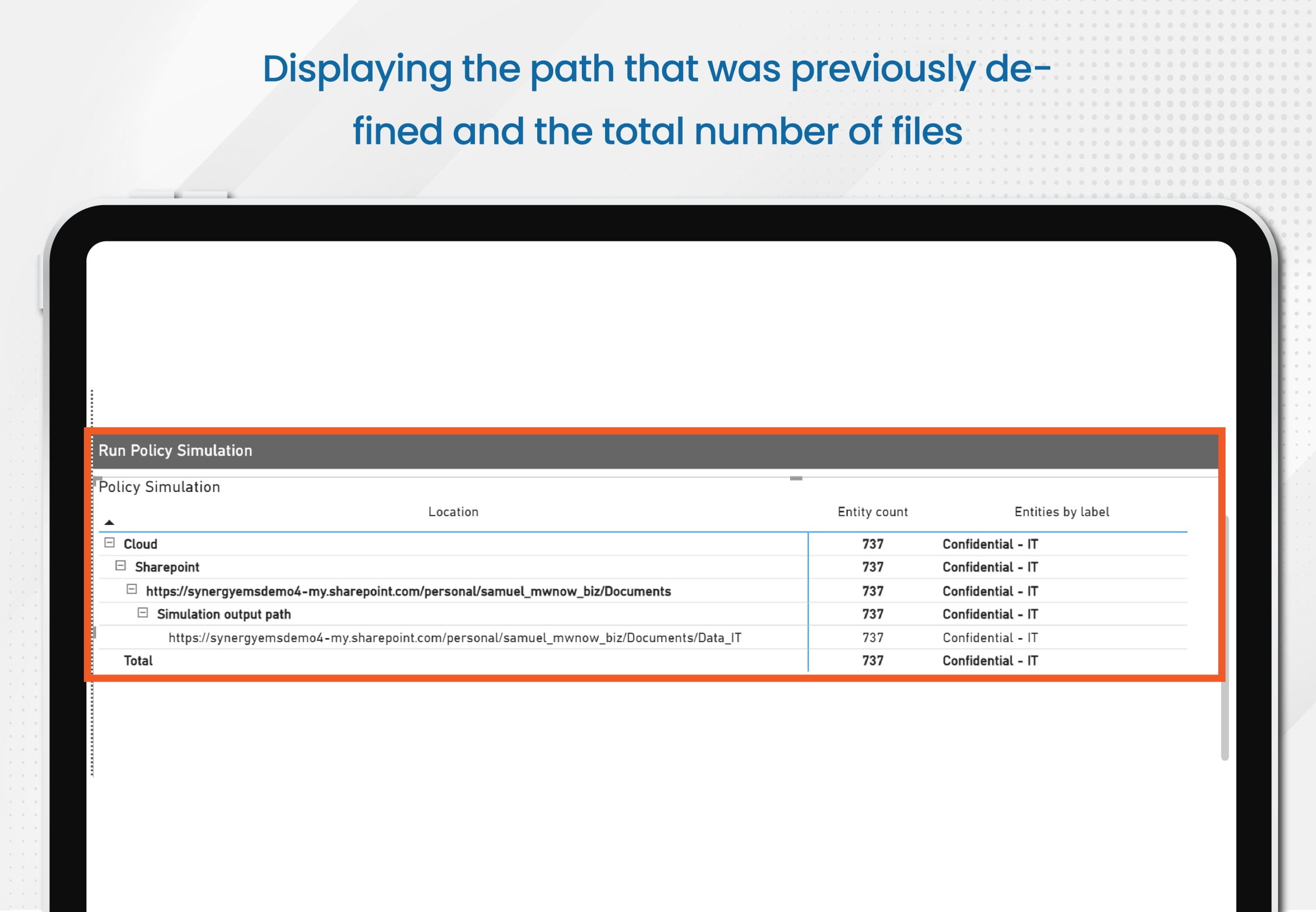
- In this scenario, the system can be configured to simulate the application of policies based on your existing labels so you can see the impact on specific source paths, including a re-classification option as needed
- All data will be a structure/ACL replica of your existing data repository in a different /duplicate path
- Outcome
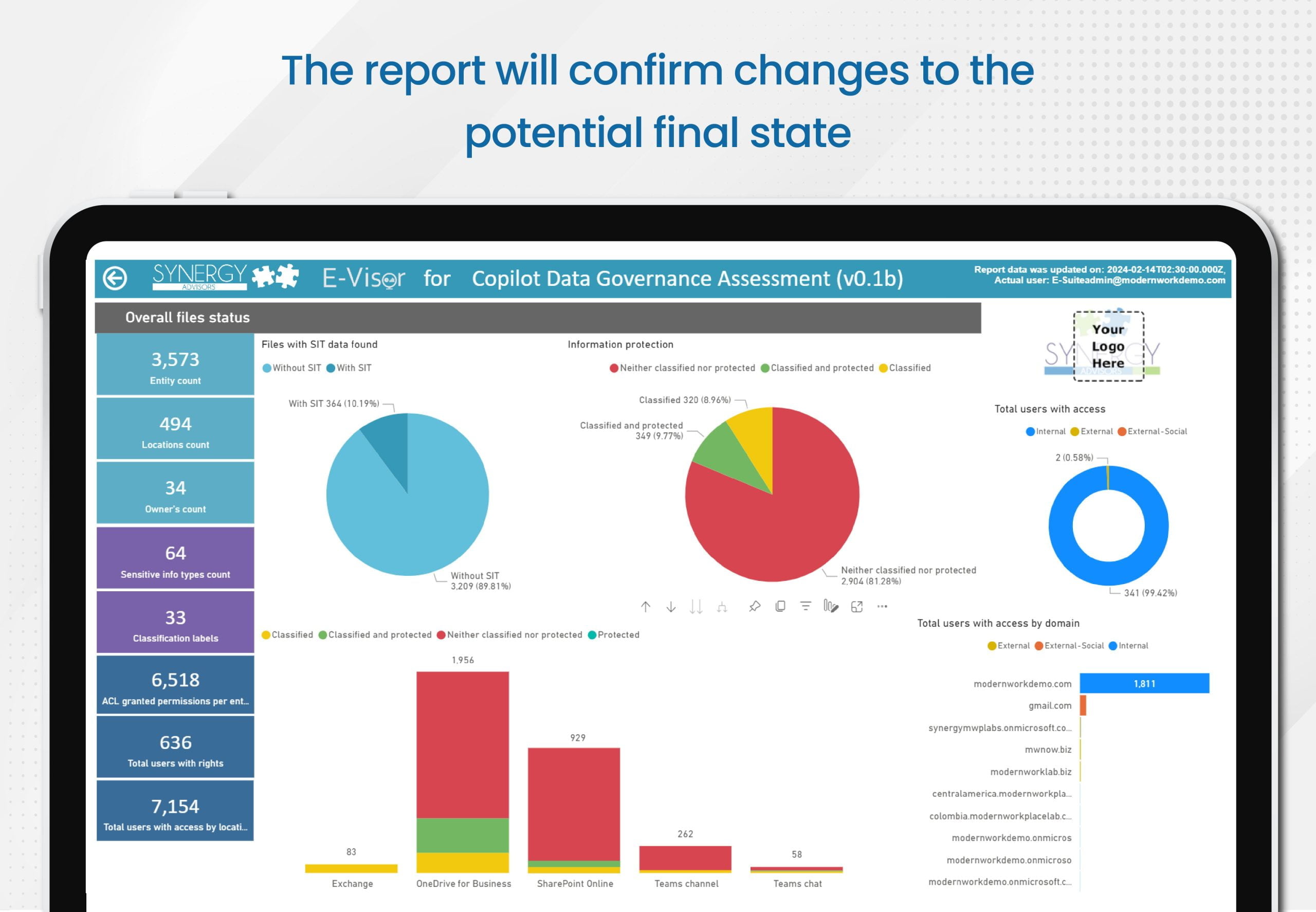
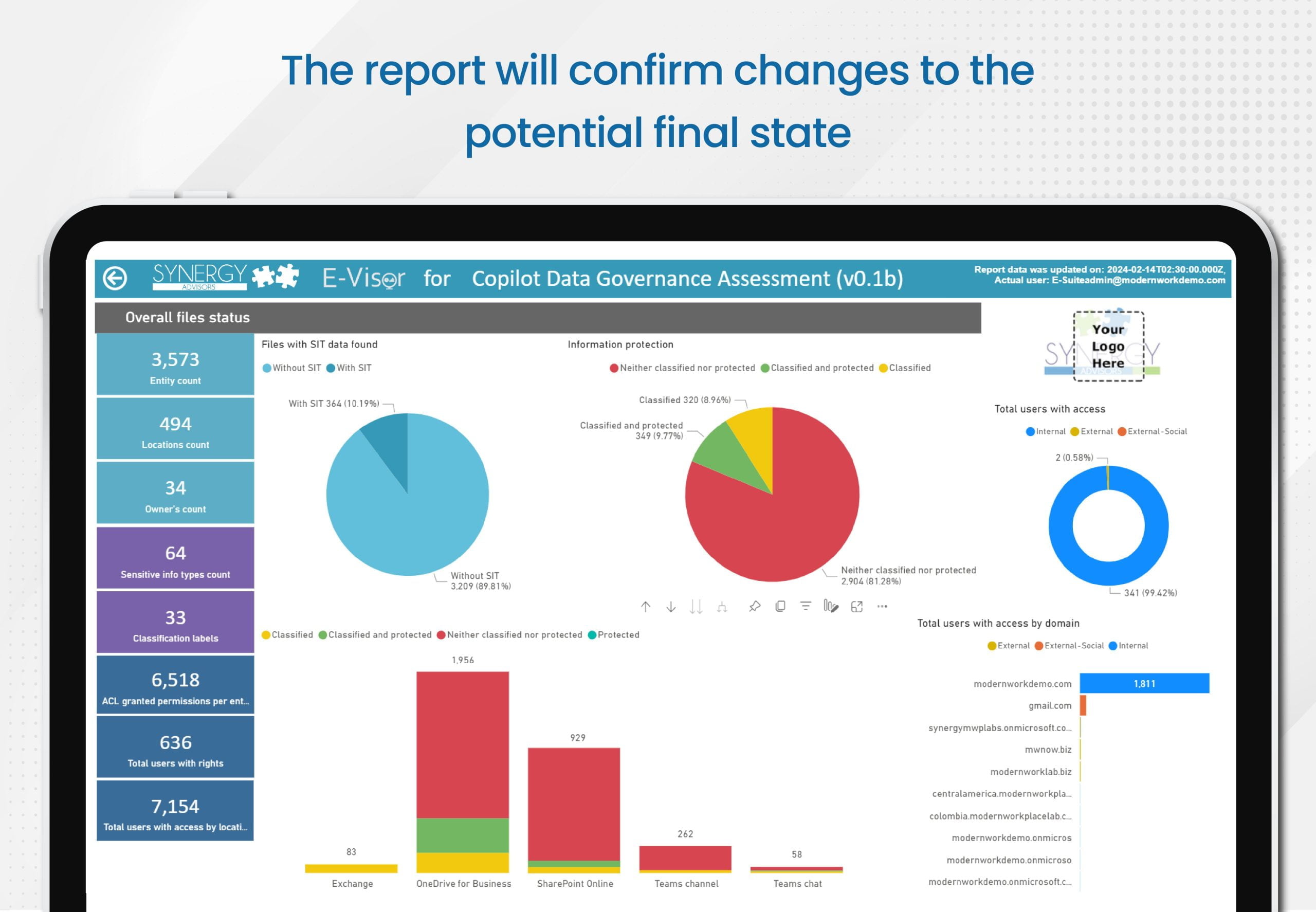
- At the end, the report will confirm changes to the potential final state, including who will continue having access after you specify a policy within the report
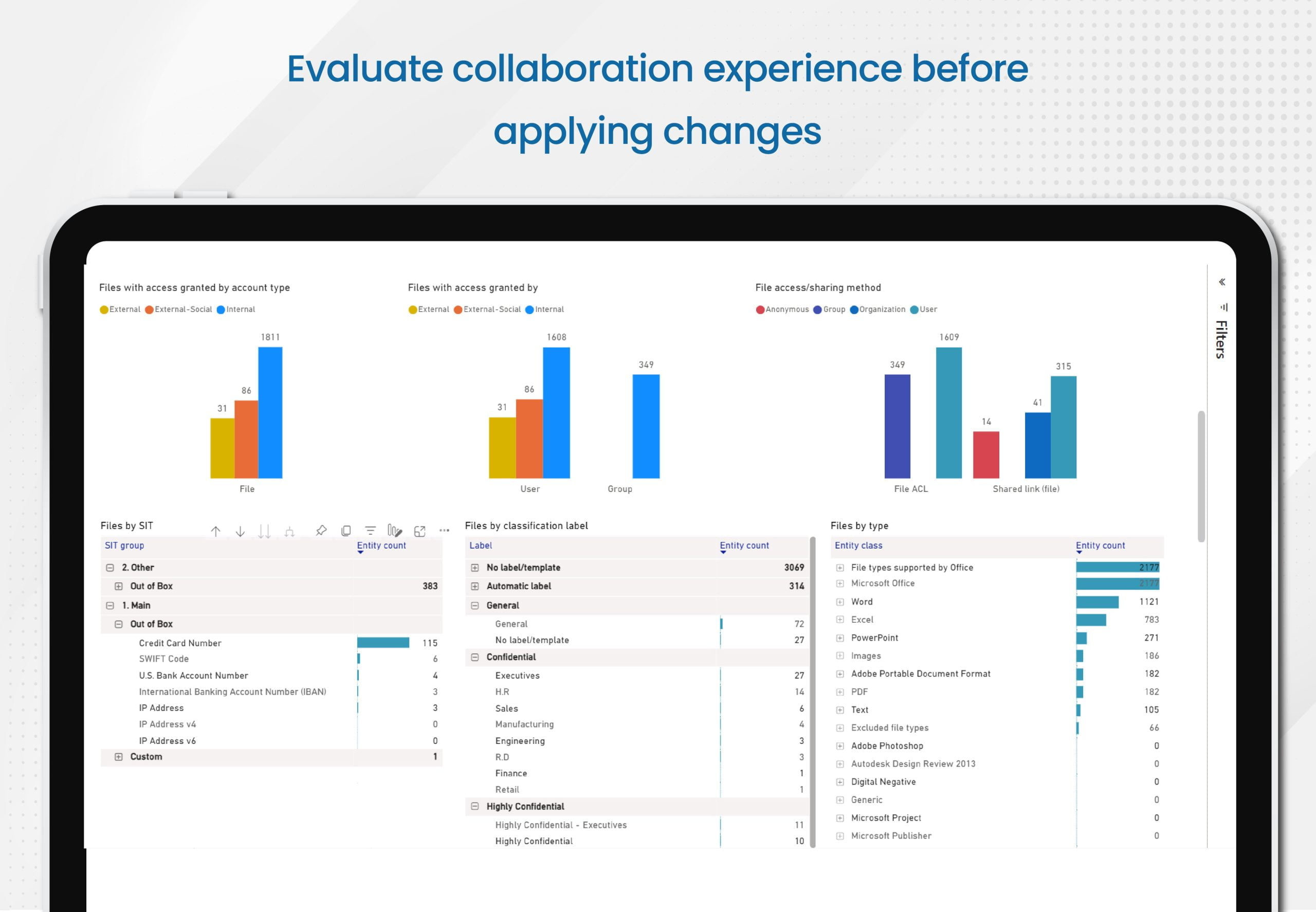
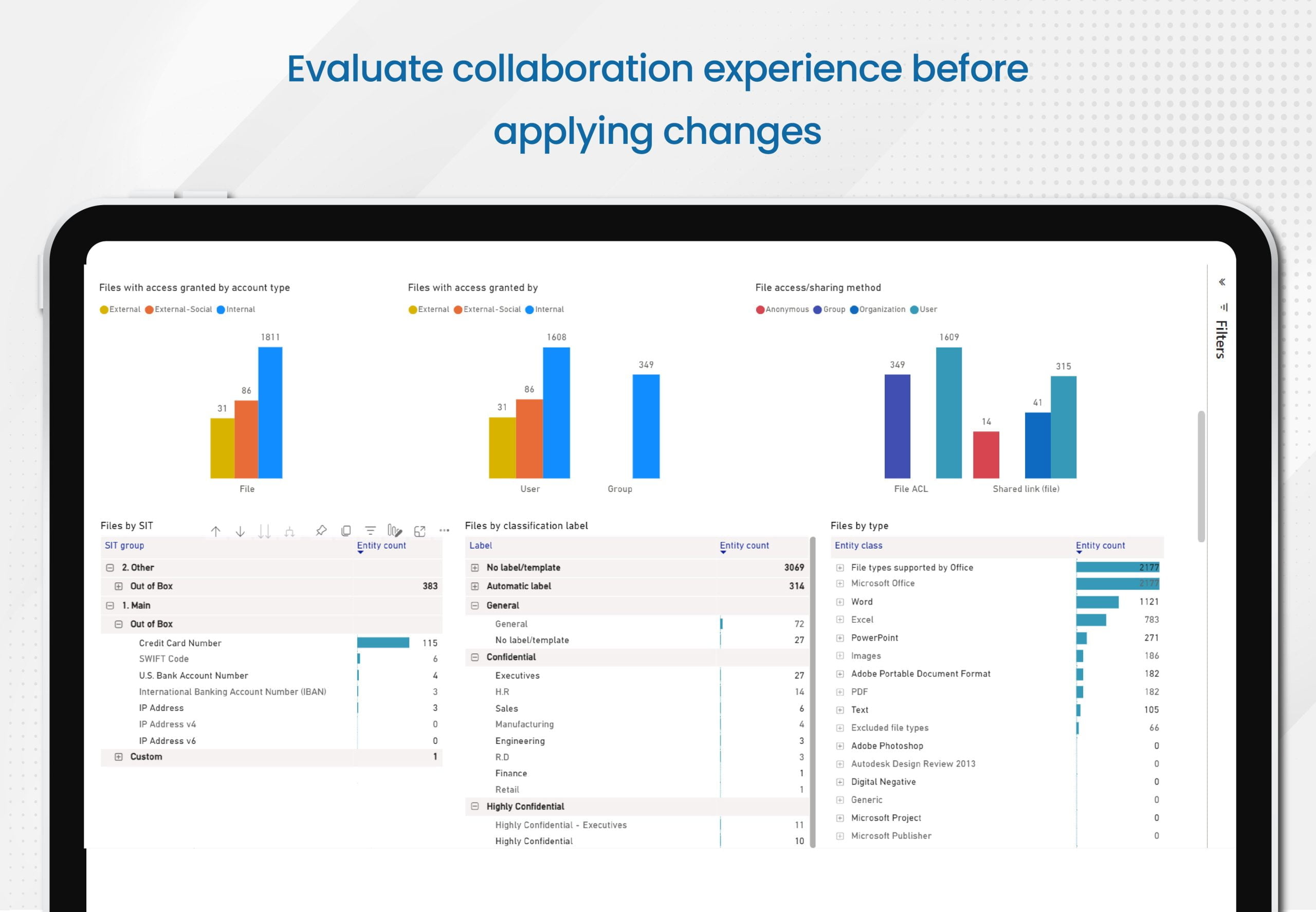
- Also, the tool can check if the user collaboration experience within those files satisfies your requirements prior to the application to the source documents
- At the end, the report will confirm changes to the potential final state, including who will continue having access after you specify a policy within the report
Policies:
Outcomes:
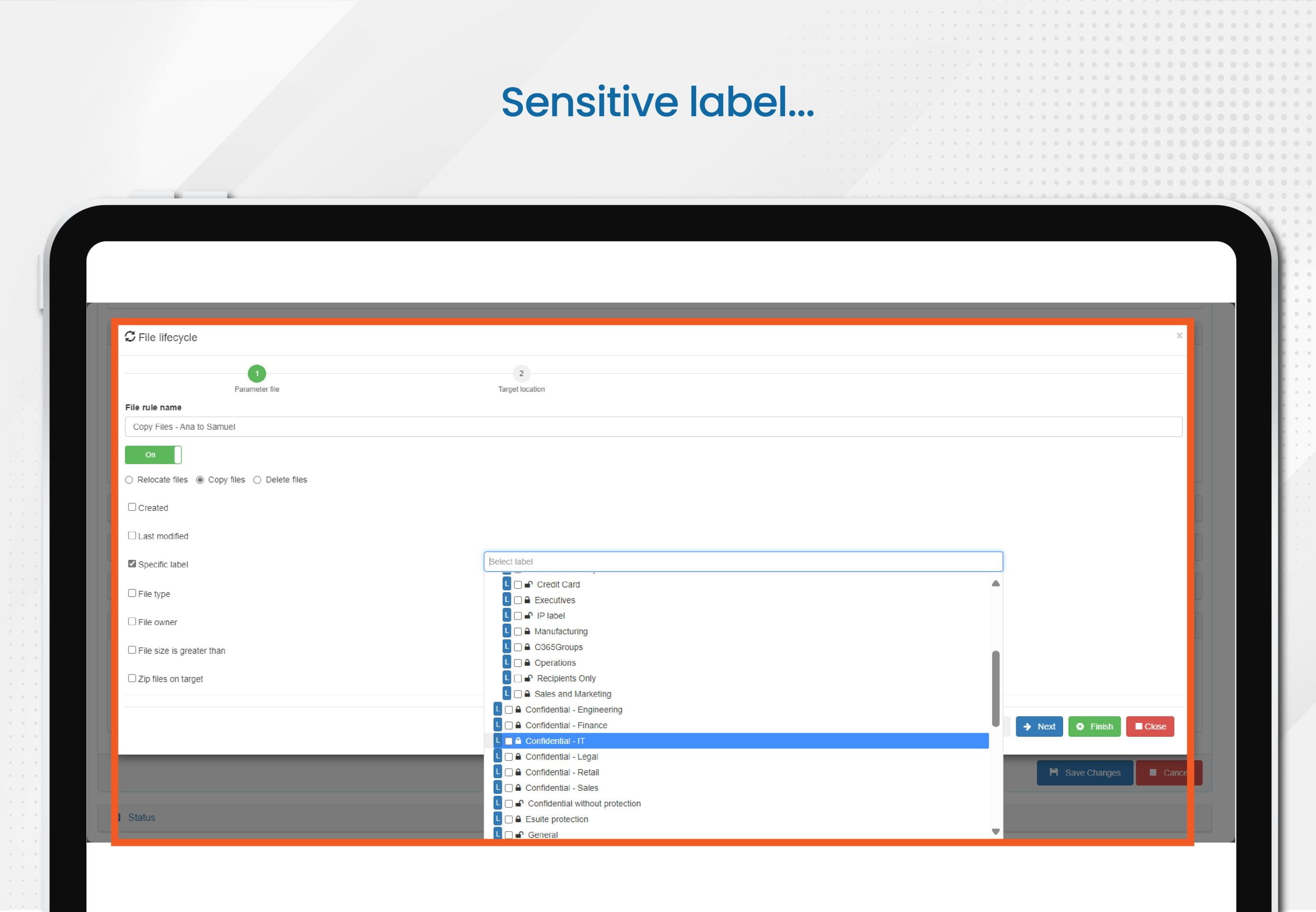
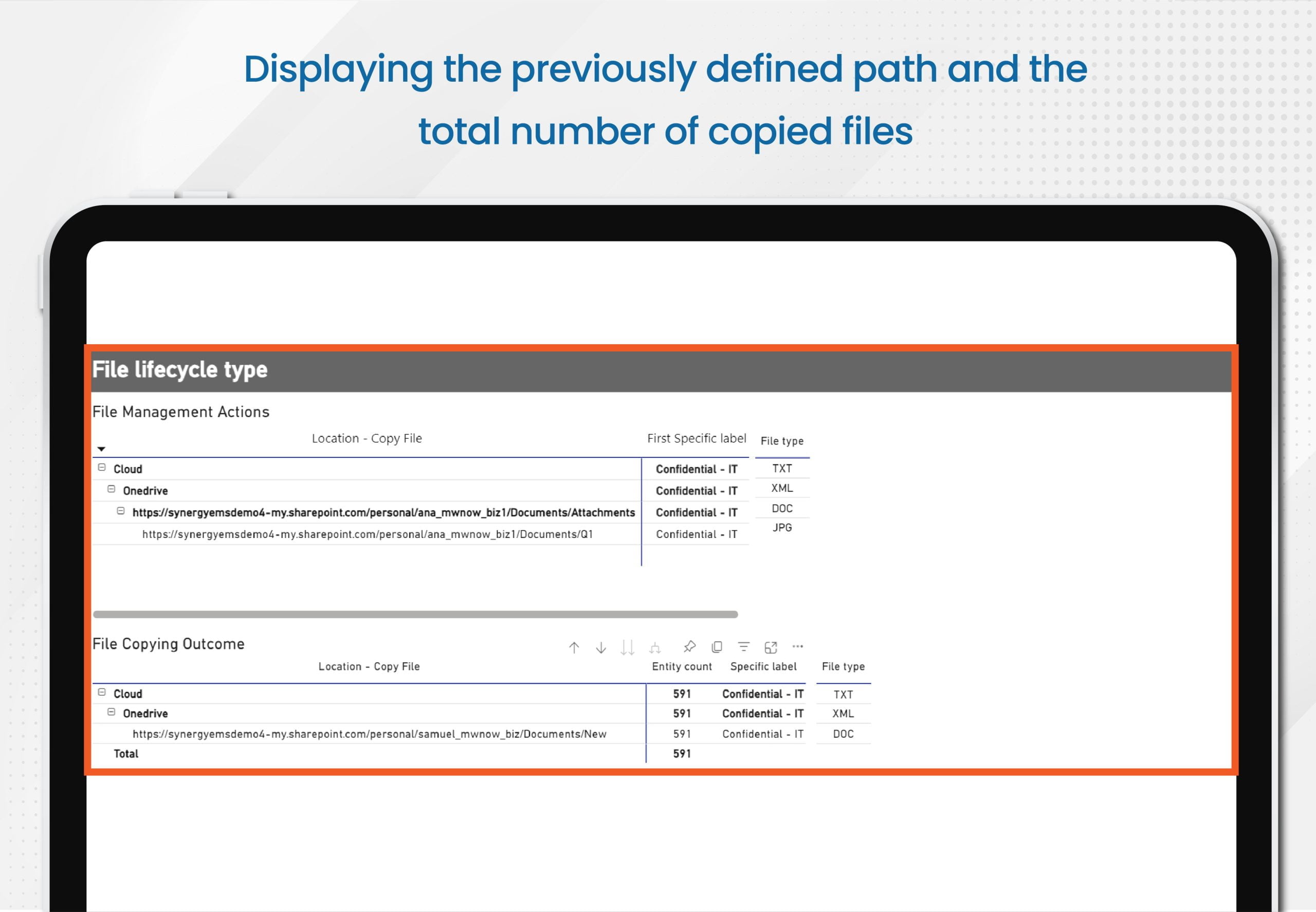
Copy
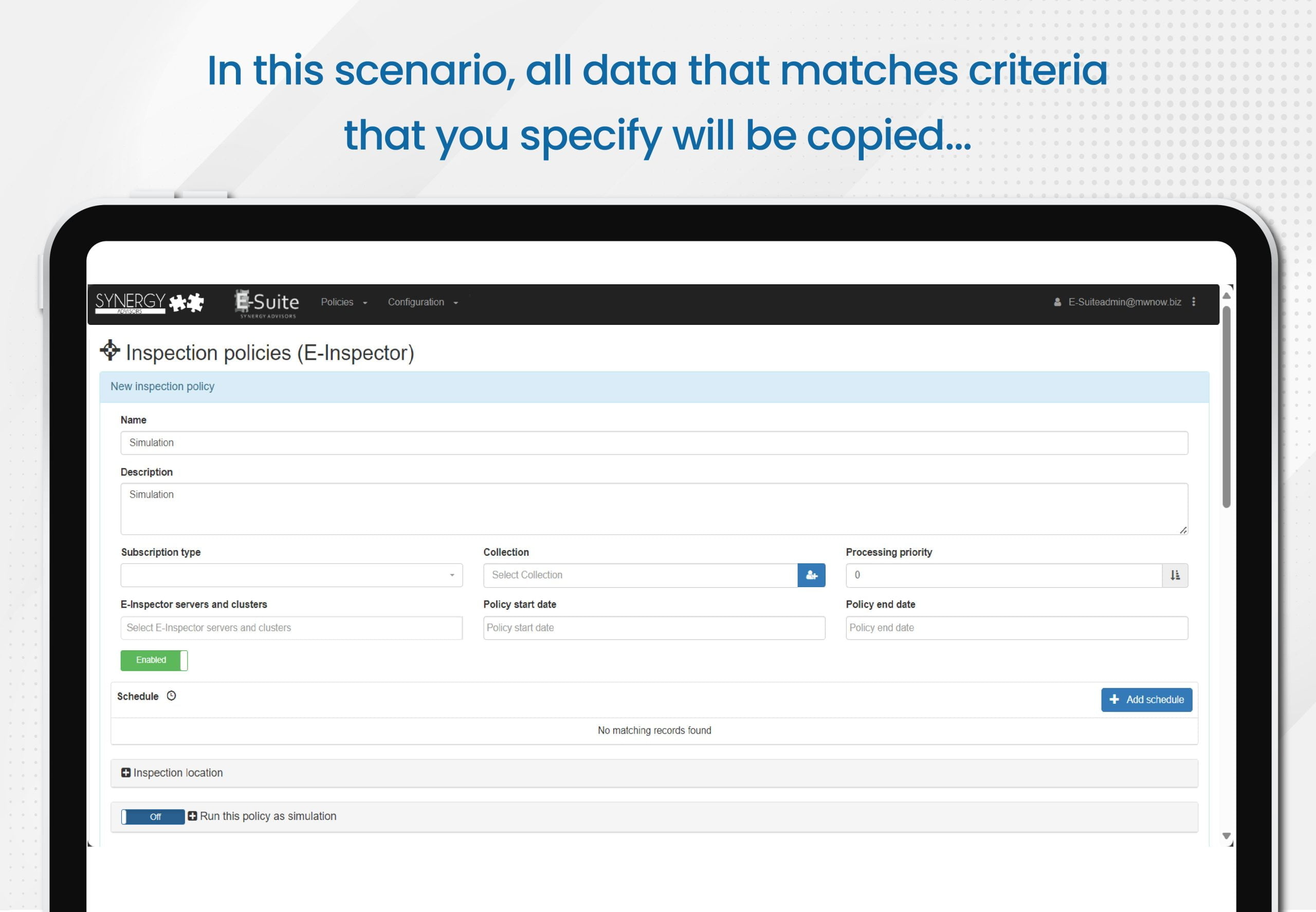
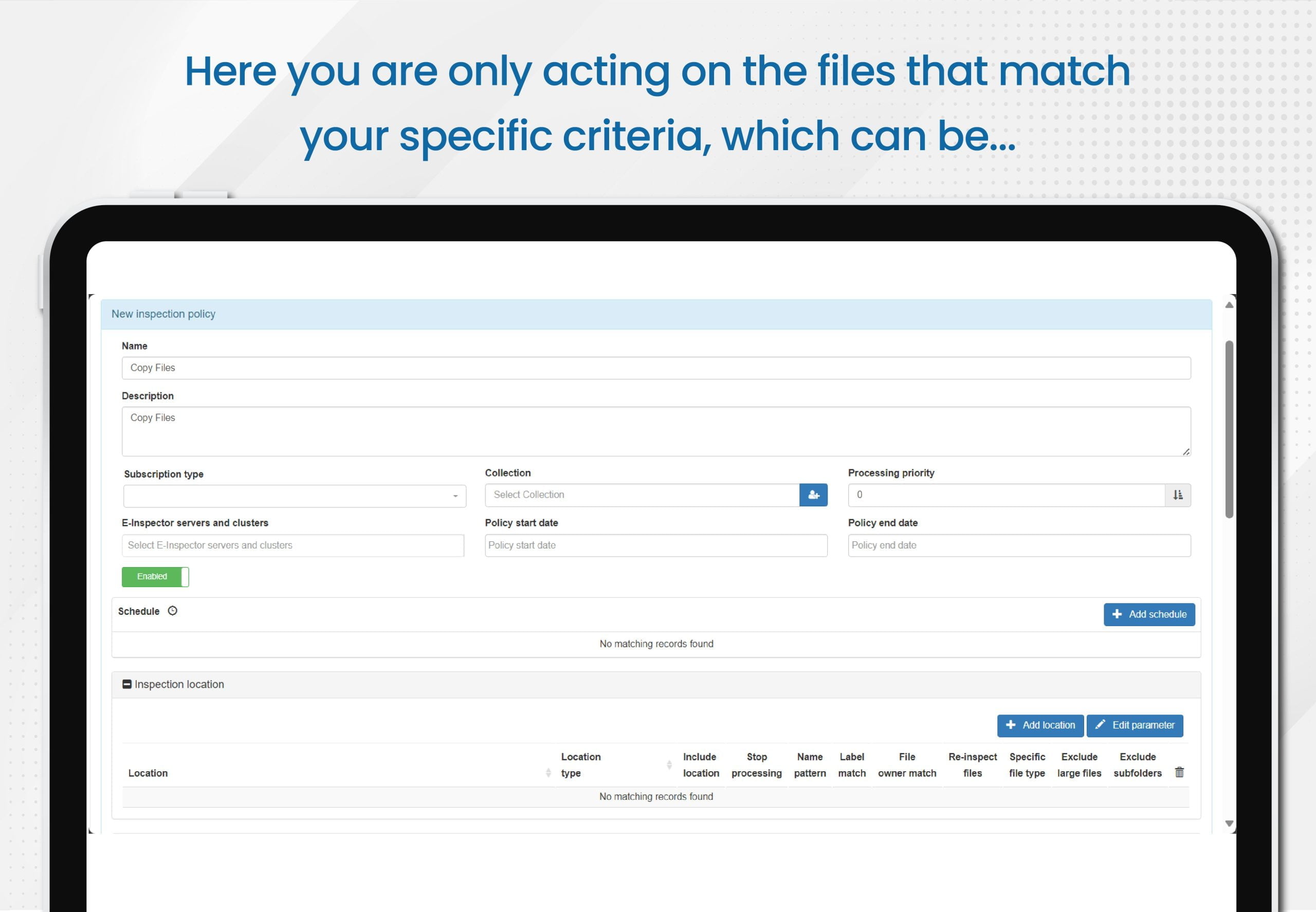
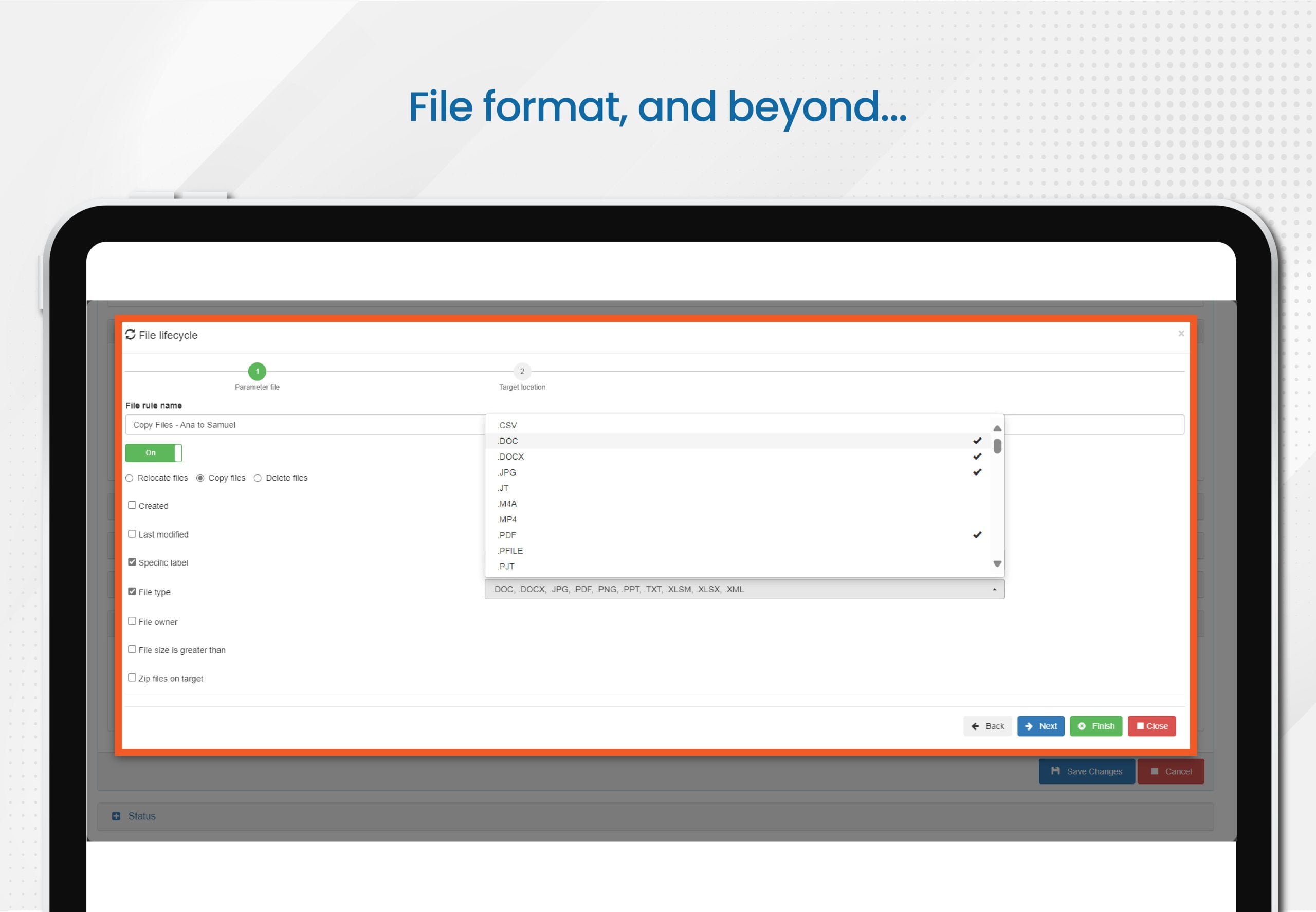
- In this option, all data that matches criteria that you specify will be copied. Note that, unlike the previous discovery scenario, here you are only acting on the files that match your specific criteria, which can include one or more of the following: sensitive data, sensitivity label, stale status, file format, and beyond.
- Outcome
- At the conclusion of the scan, the report will confirm changes to the potential final state, including an outline of who will continue to have access after you enact the policy
- Also, the tool can check if the user collaboration experience within those files satisfies your requirements prior to the application to the source documents
- Example:
- Copy all files with PII, apply a specific policy, and then people can validate their access
- At the conclusion of the scan, the report will confirm changes to the potential final state, including an outline of who will continue to have access after you enact the policy
Policies:
Outcomes:

Now that you feel comfortable applying changes, note that among all upcoming options listed below, you can combine them all, Serve yourself!
NOTE: Please consider making a full backup of your SharePoint Online (SPO Premium/separate method) prior to implementing these changes.
- Original Files Changes/Path
Pre-conditions
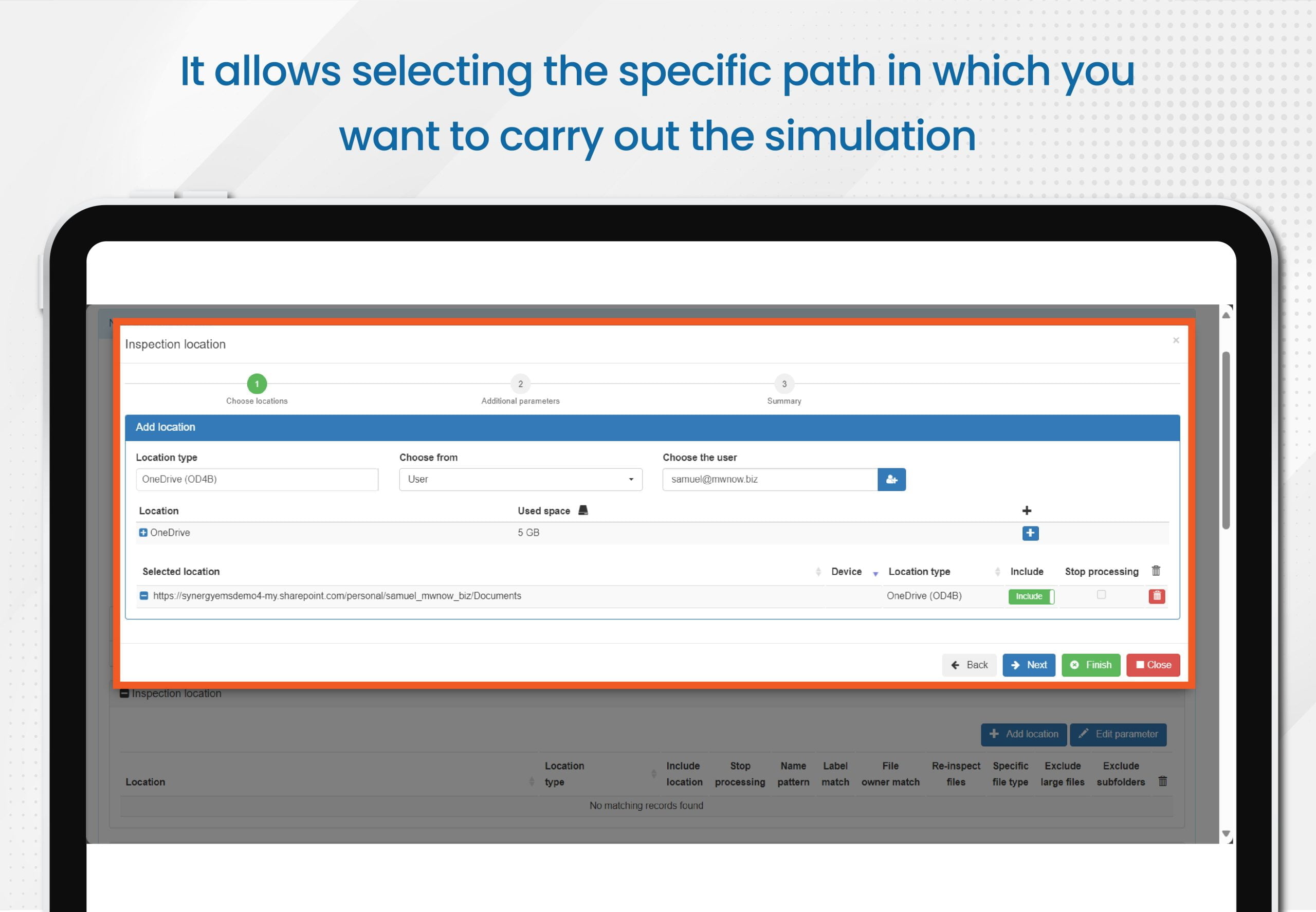
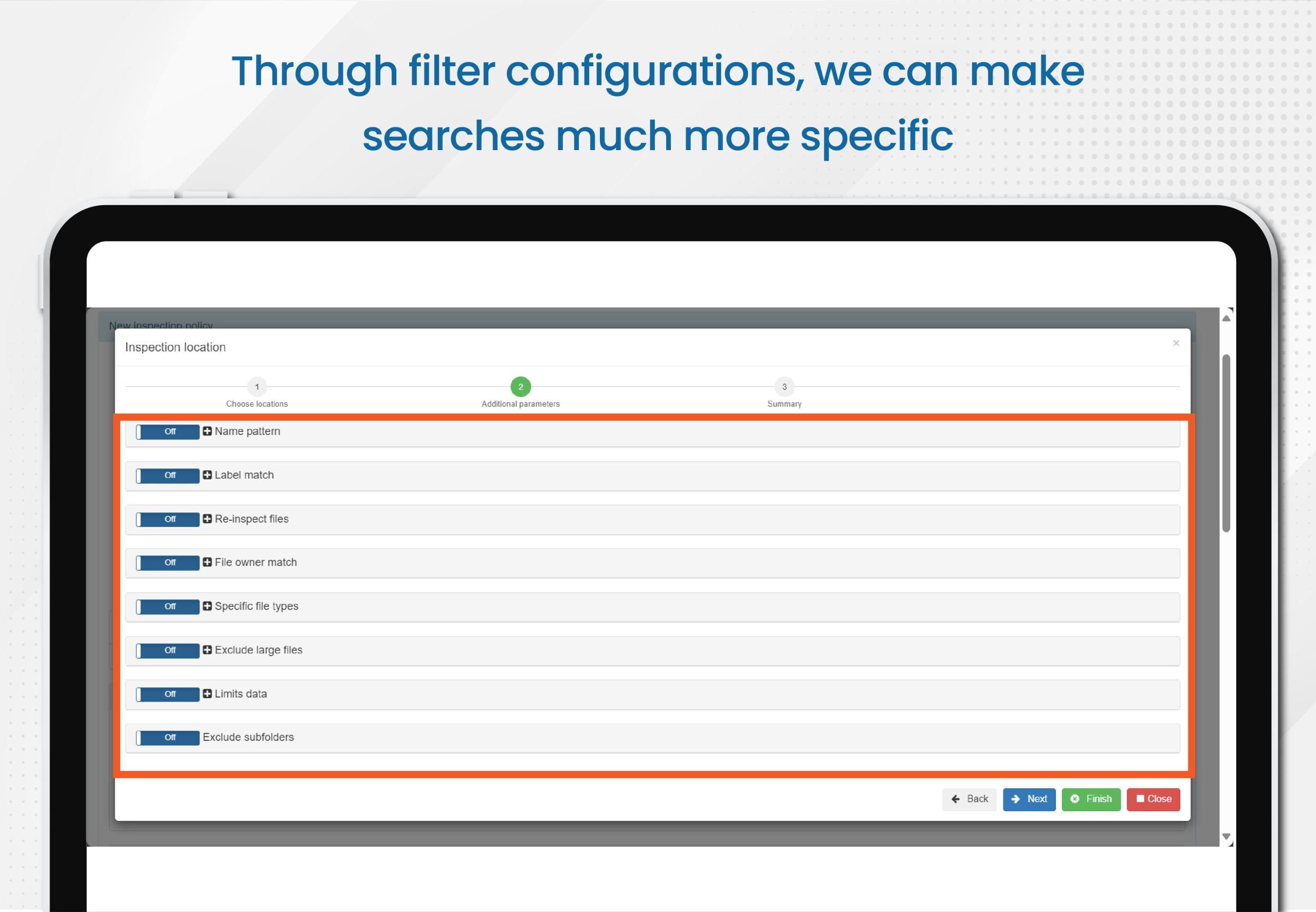
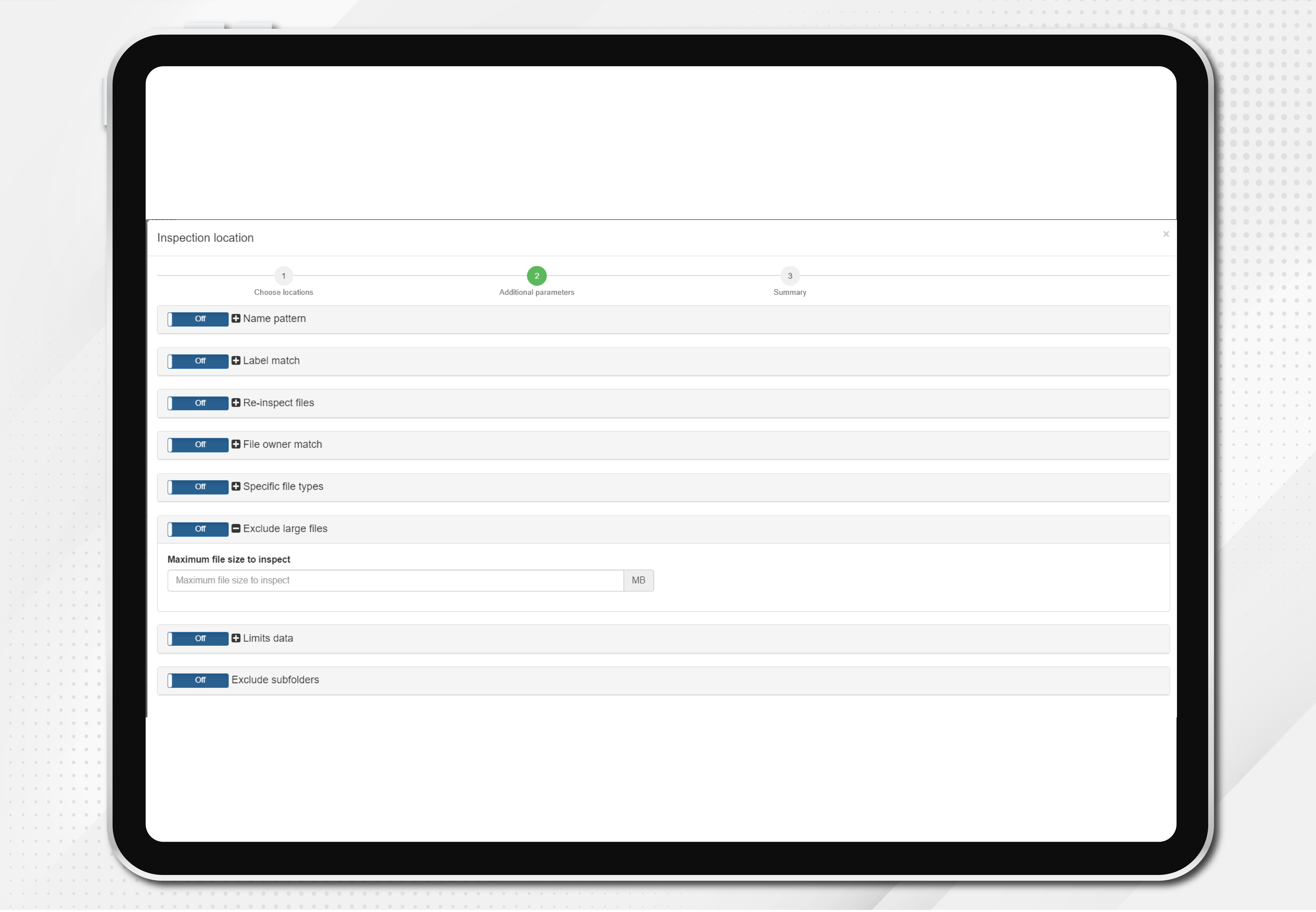
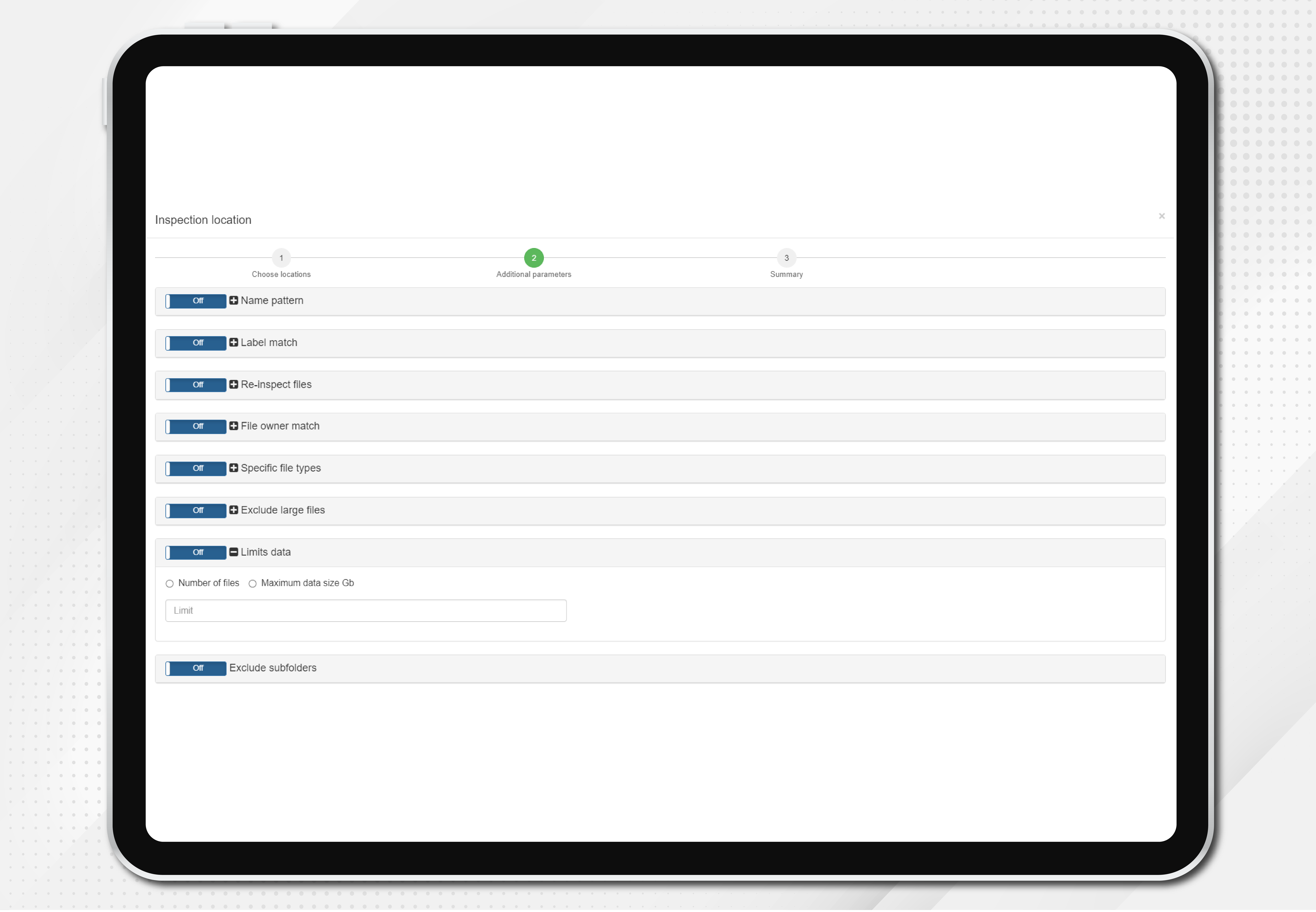
With E-Inspector, you have the ability to define specific parameters for more precise and effective searches. This enables you to quickly and accurately identify relevant data within your documents.
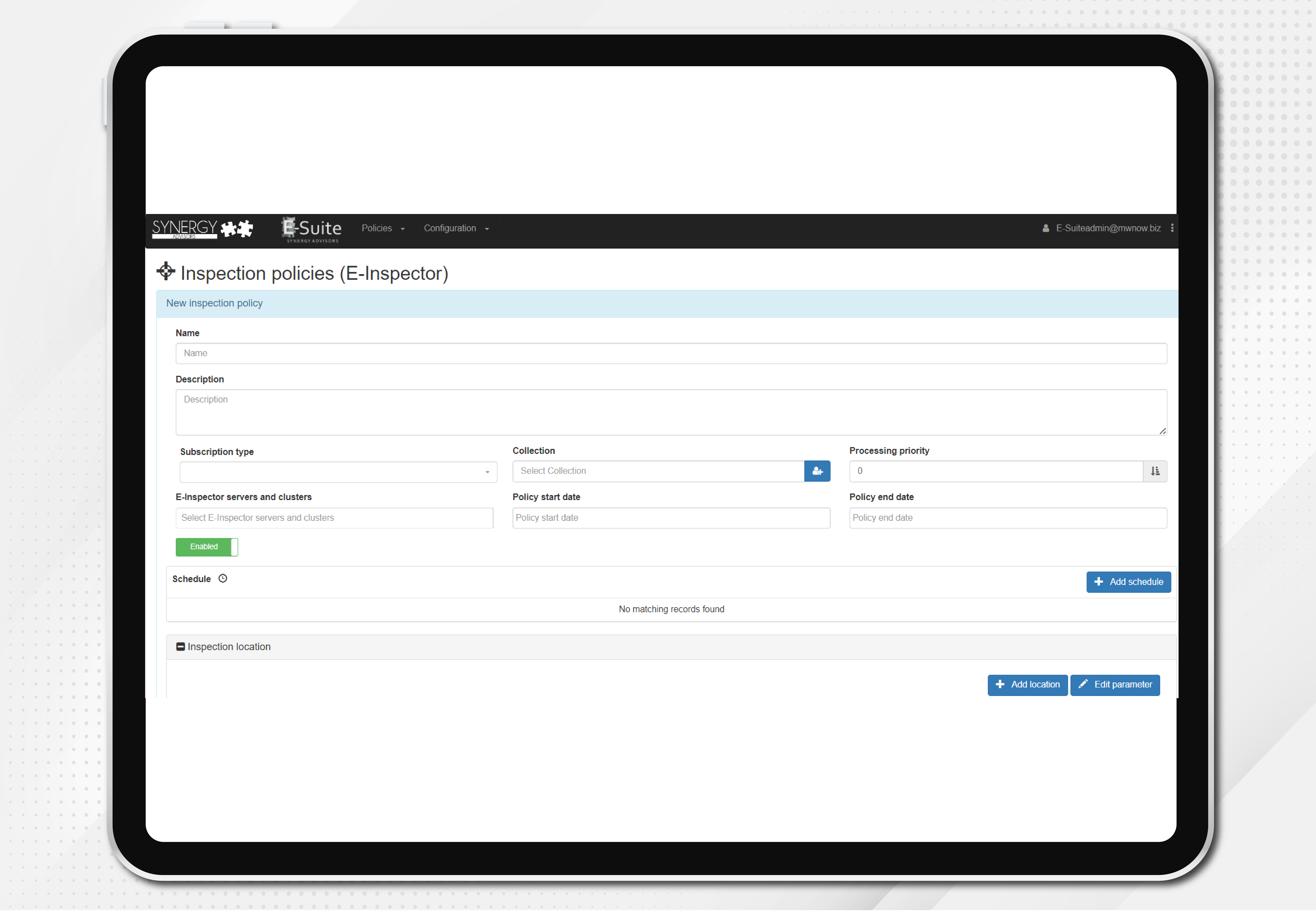
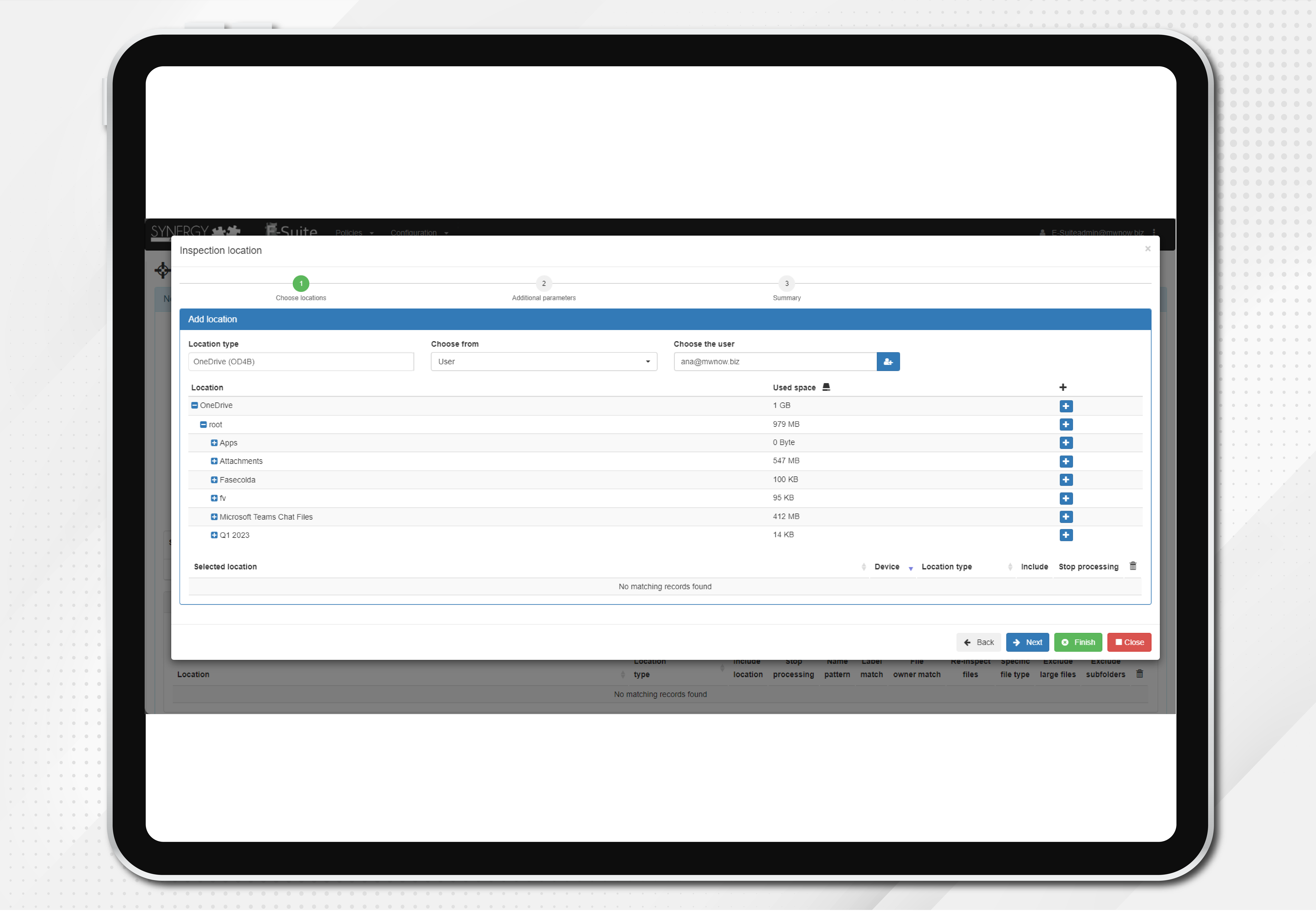
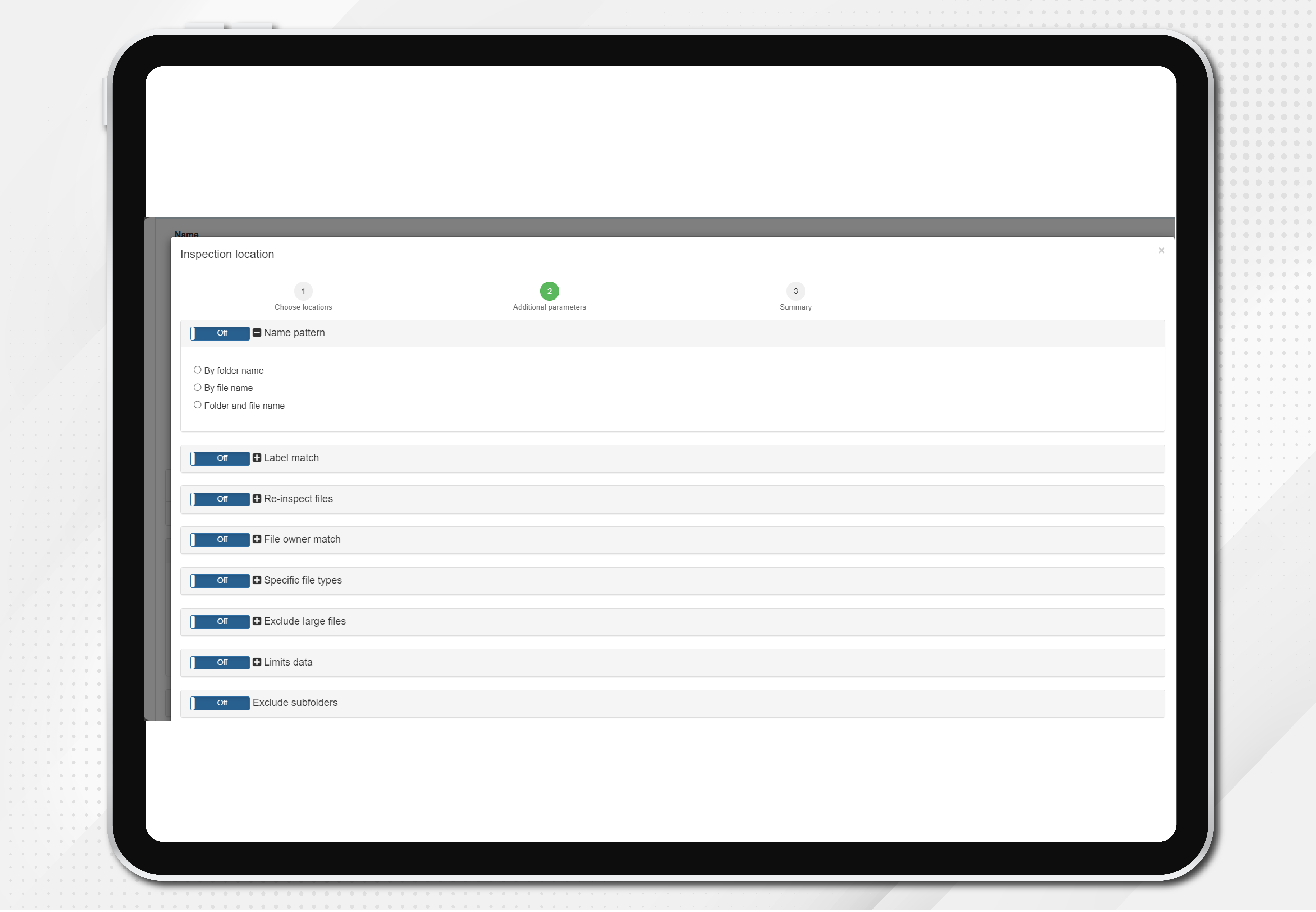
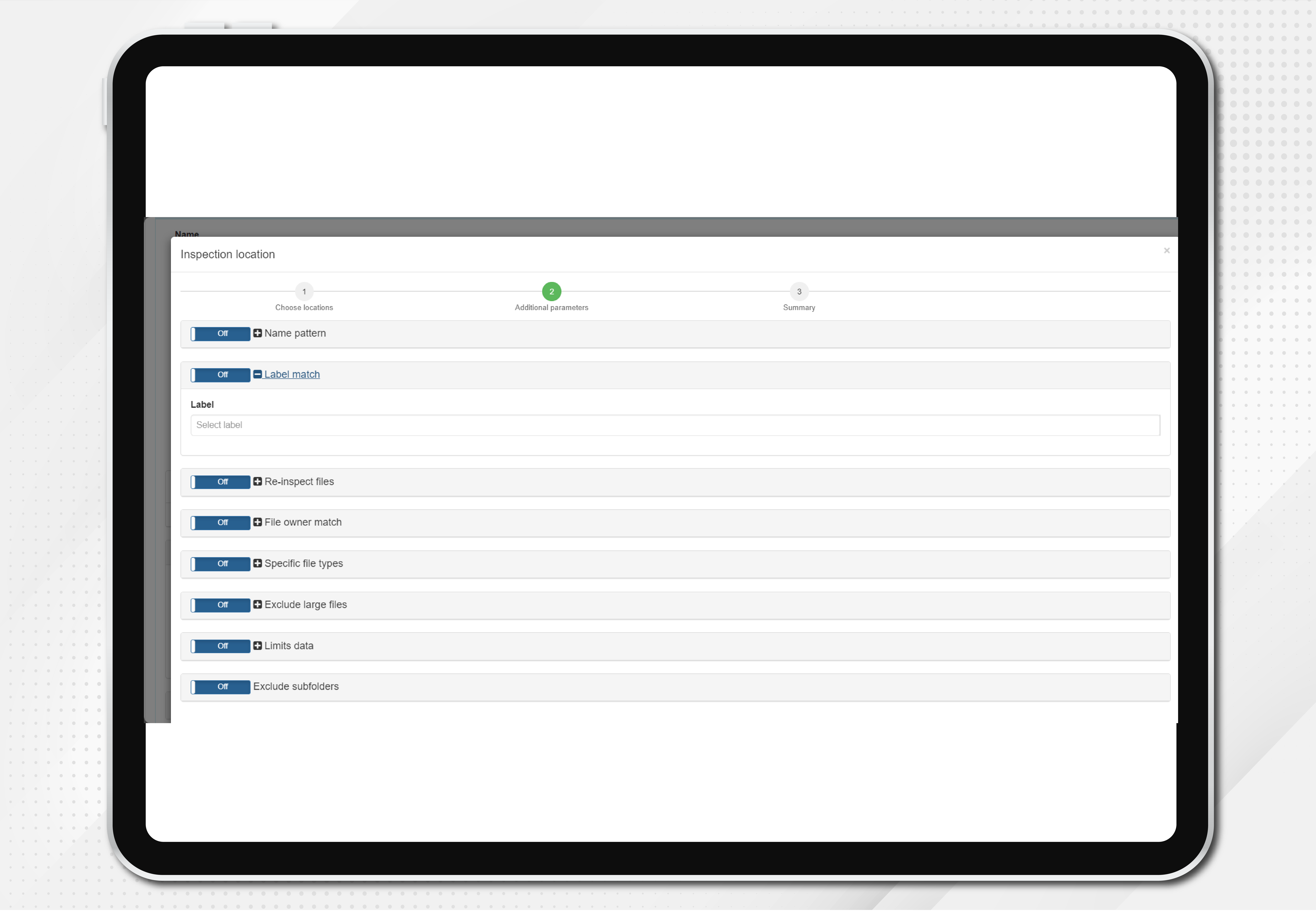
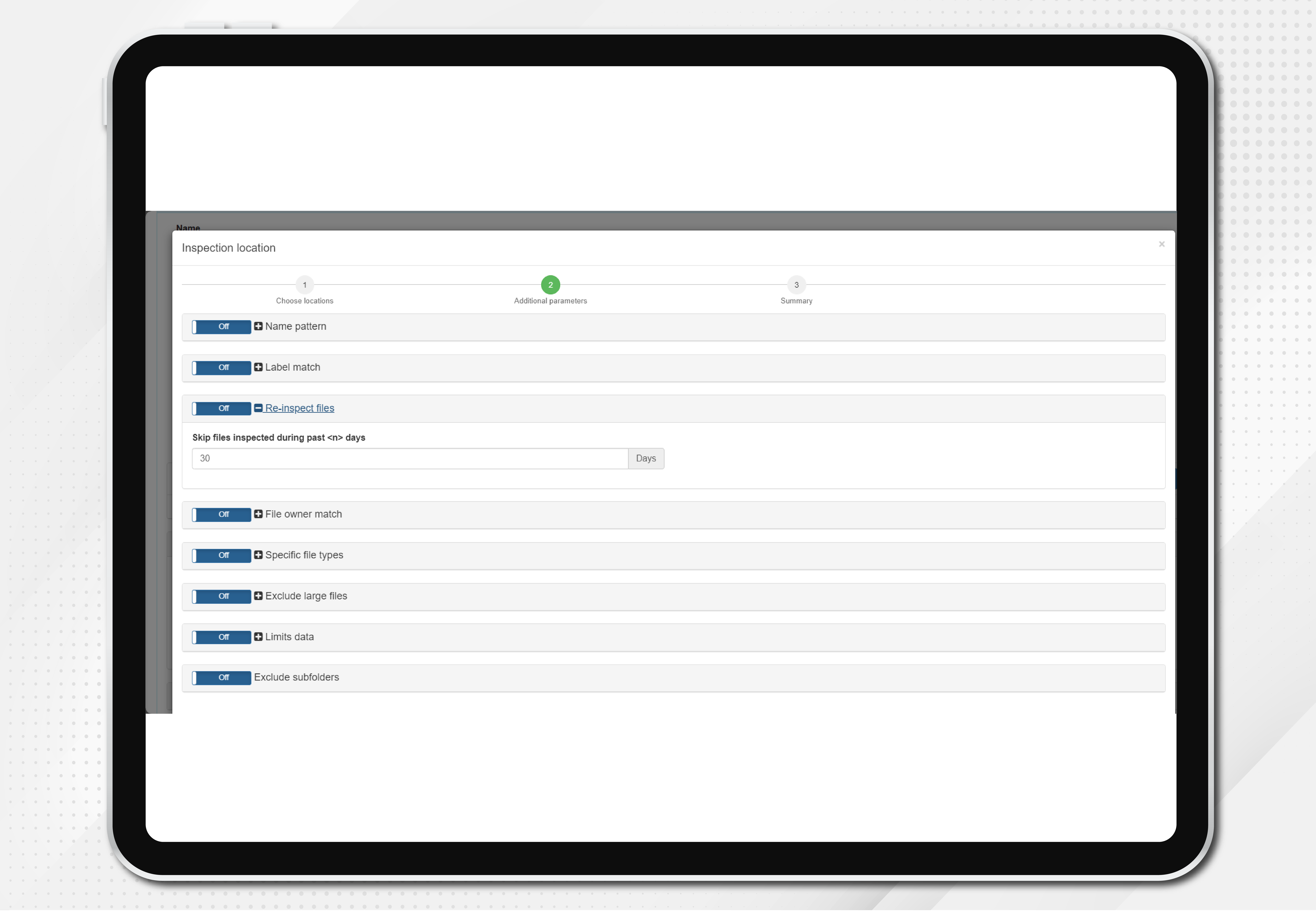
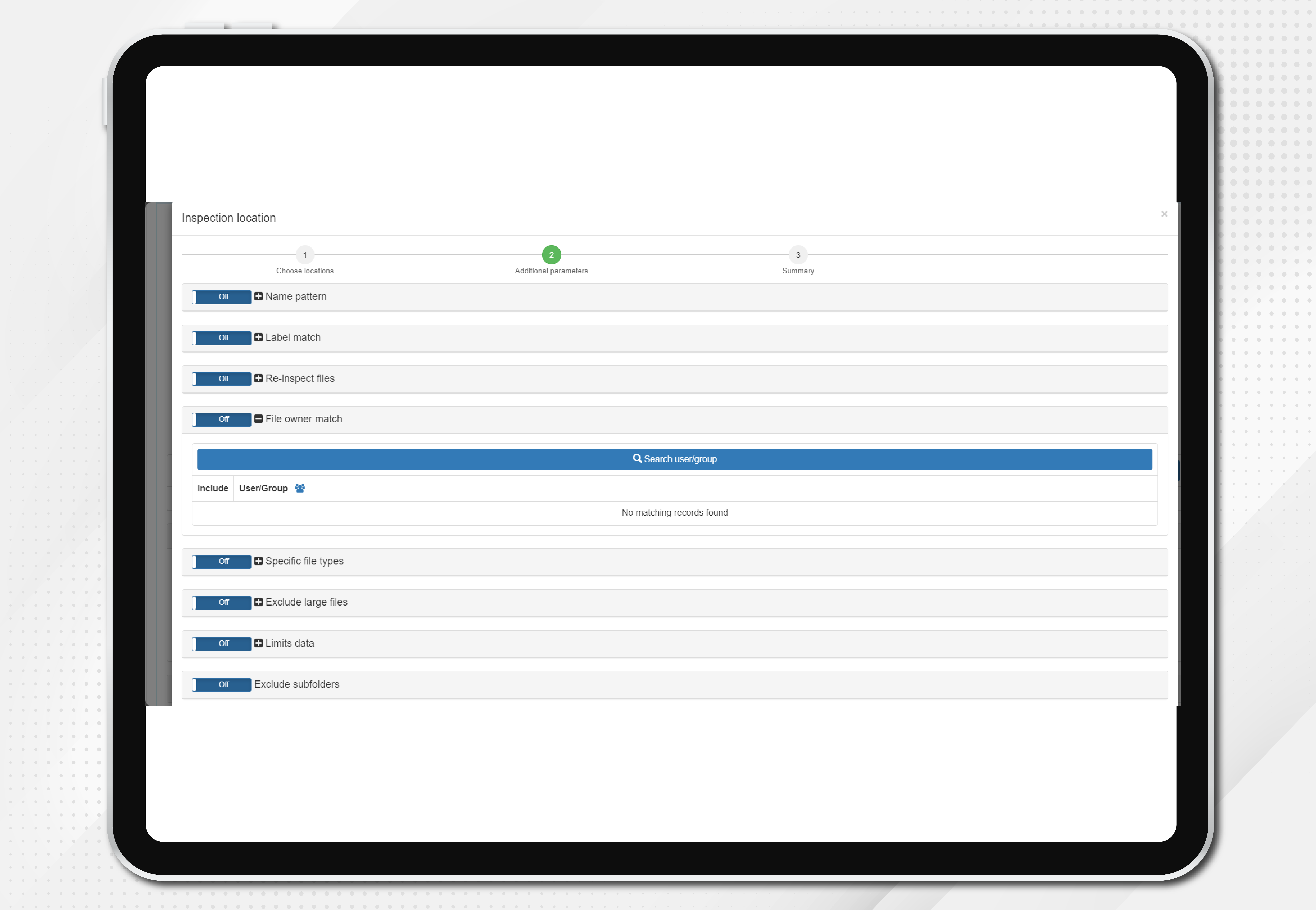
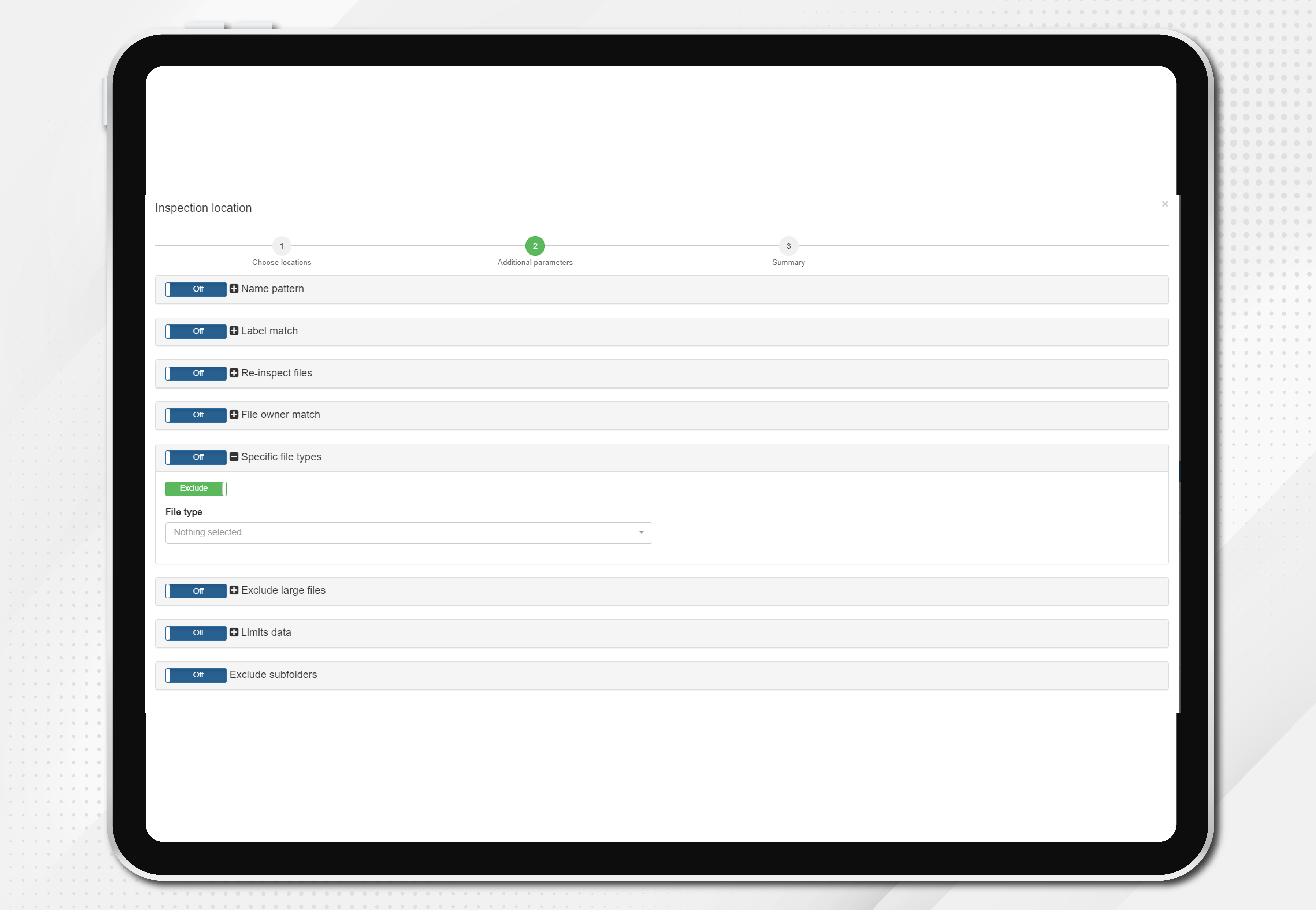
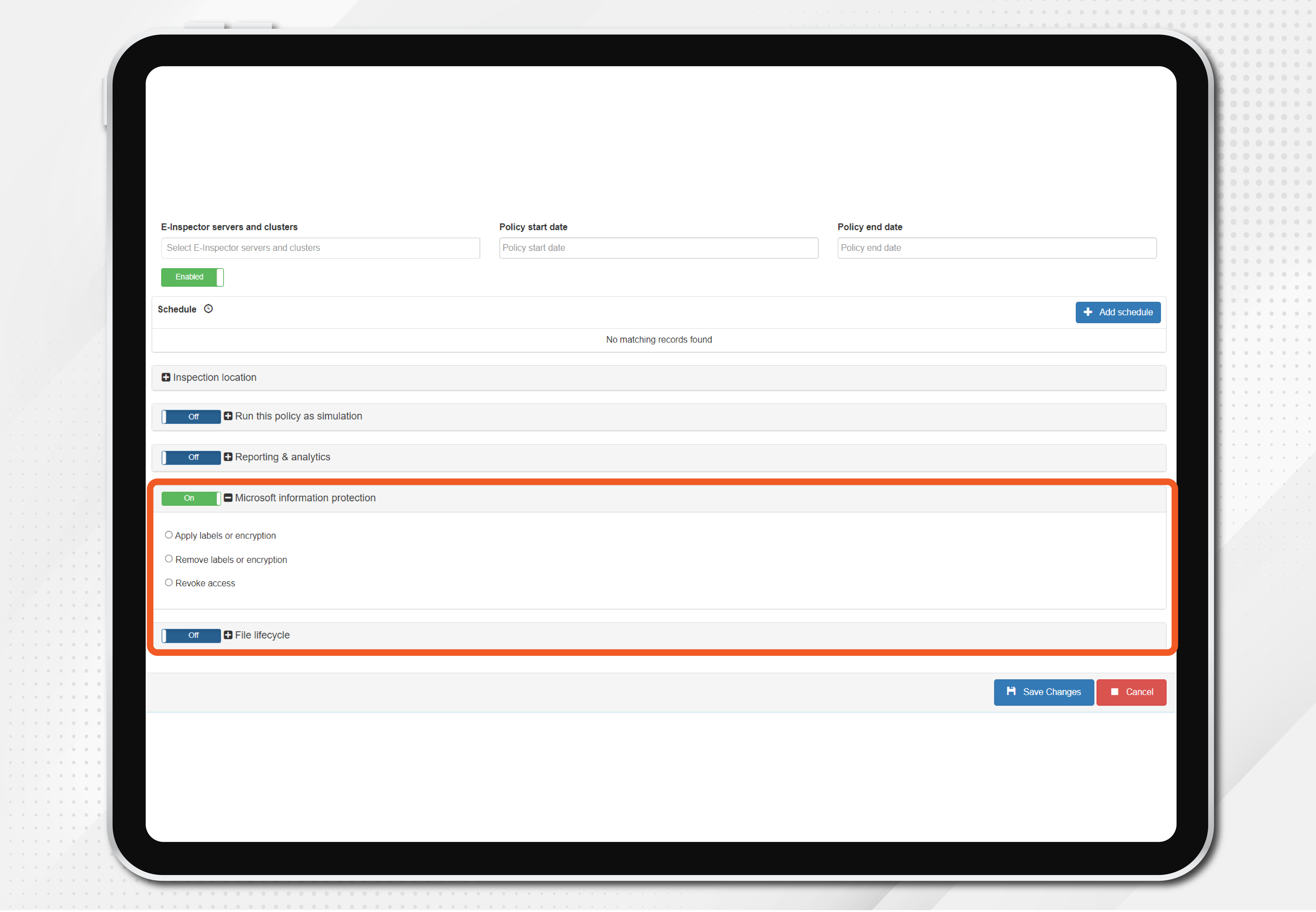
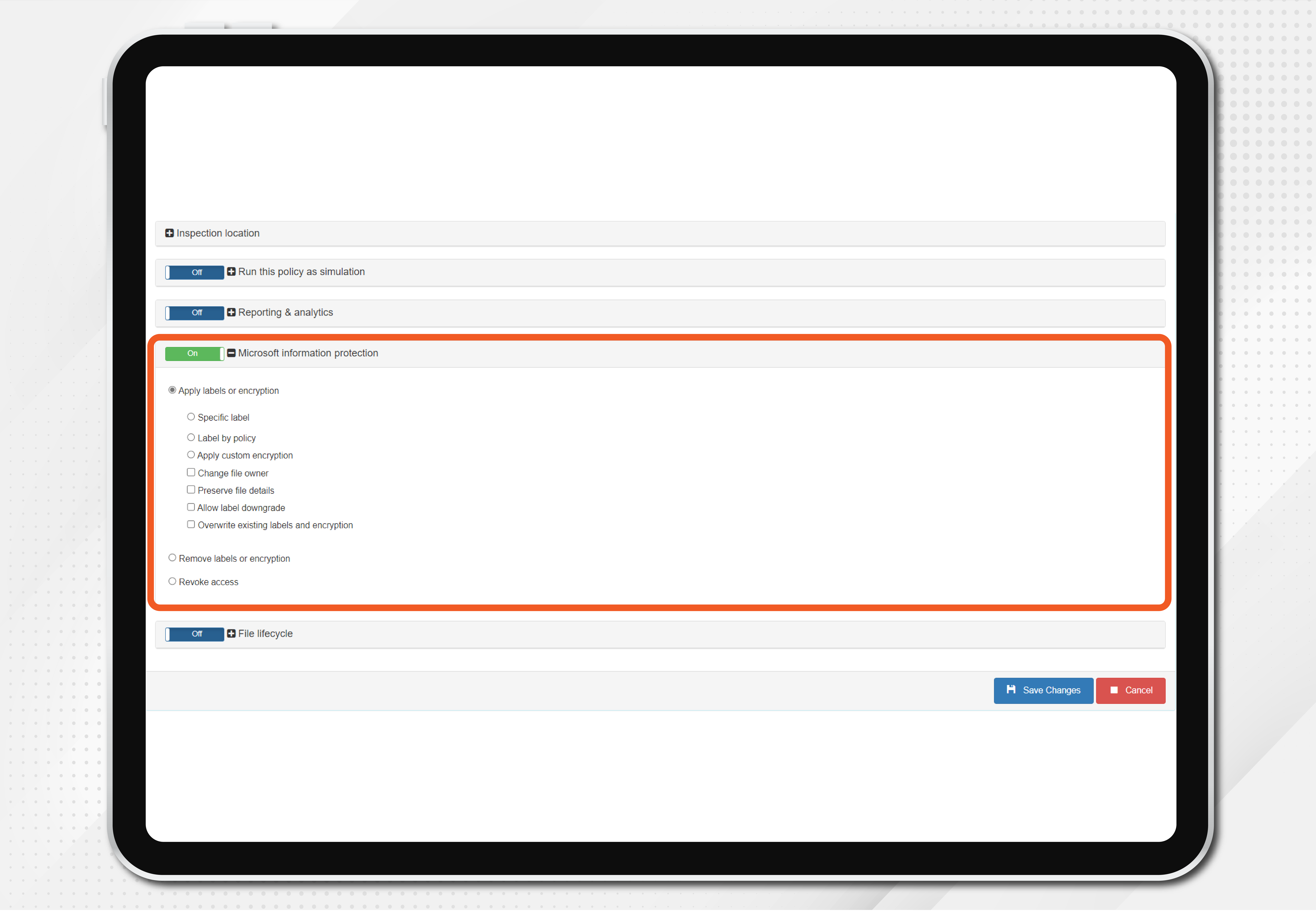
Information Protection Actions
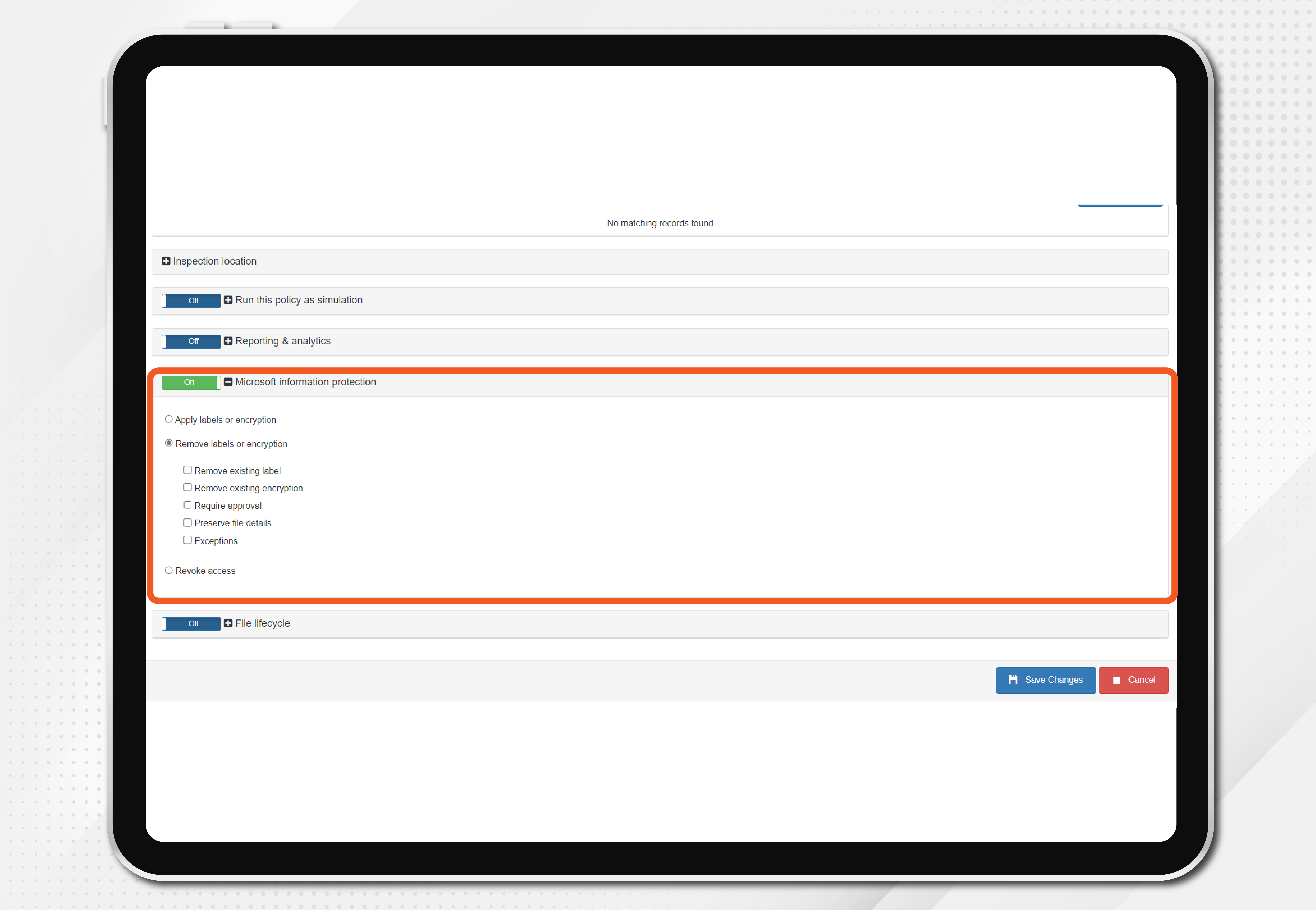
With E-Inspector, you have full control over your sensitive data through key options:
Labeling or Encryption: Classify and label documents based on confidentiality levels. Apply custom labels to specify access permissions and protection. Encryption ensures that even if someone accesses files, they can’t read the content without the right key.
Removing Labels or Encryption: If information no longer needs protection or has been shared appropriately, you can remove labels or decrypt files for agile and flexible data security management.
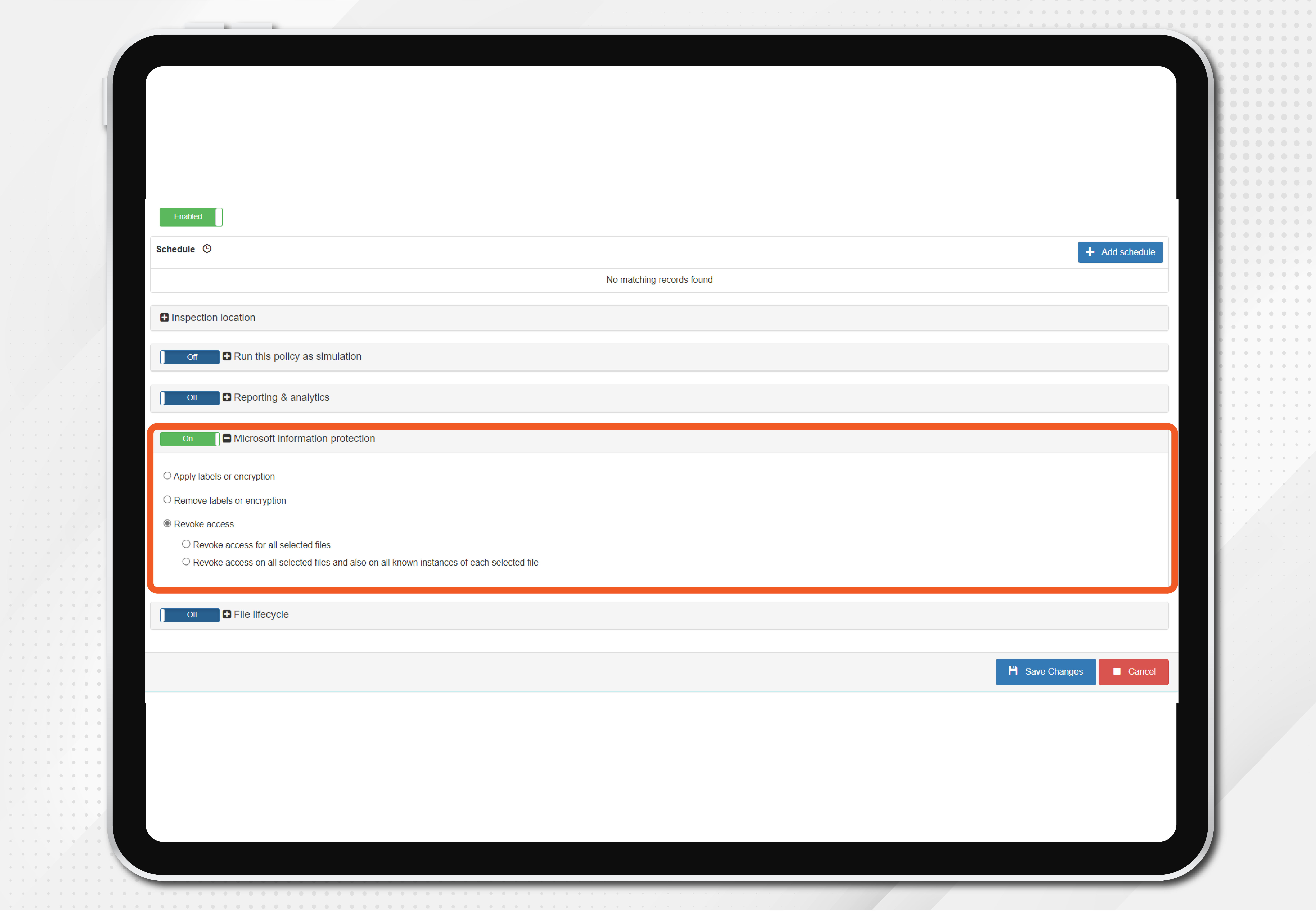
Access Revocation: In critical situations, like device loss or employee departure, immediately revoke access to files. This ensures confidential information remains secure from unauthorized individuals.
Special Treat
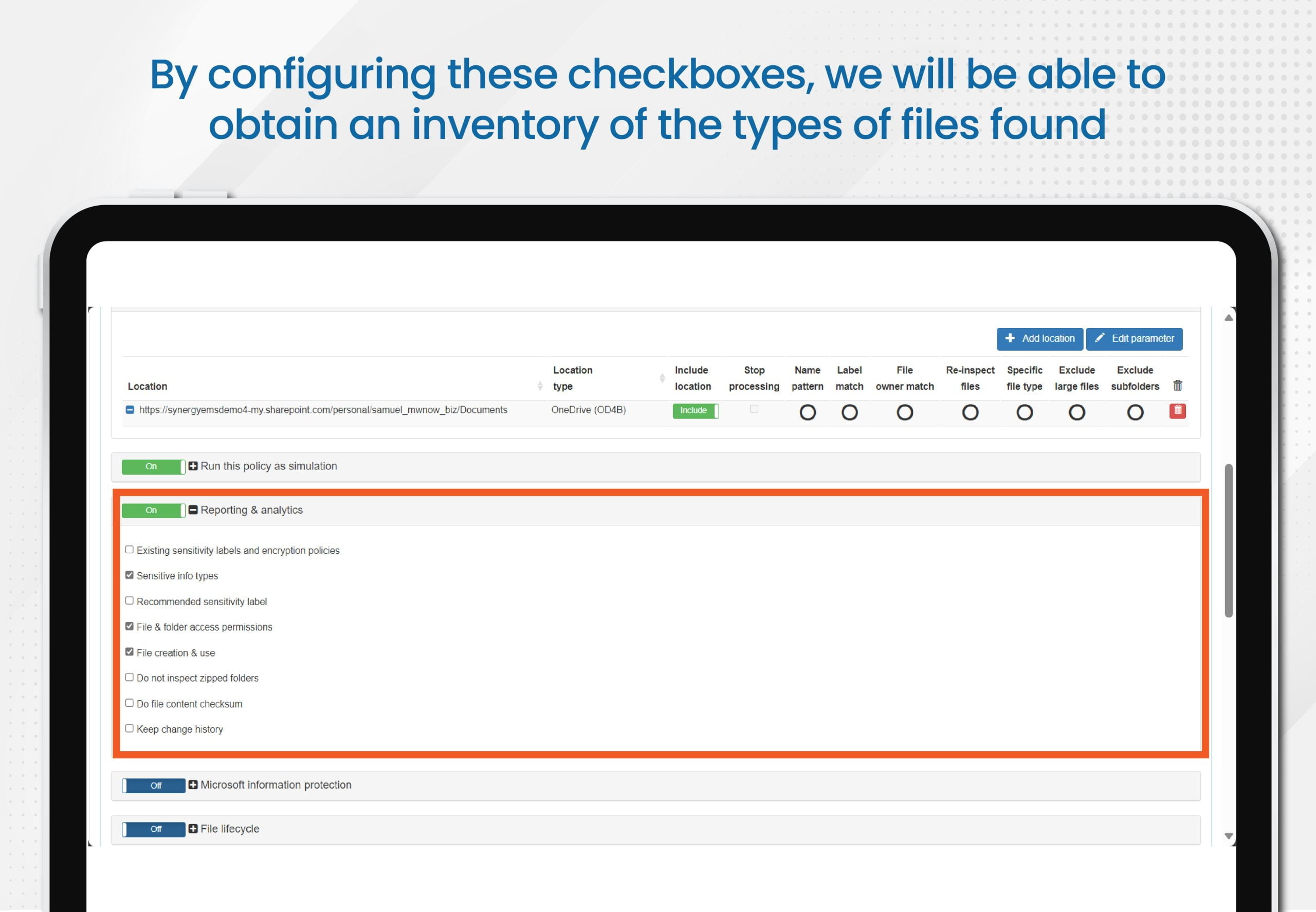
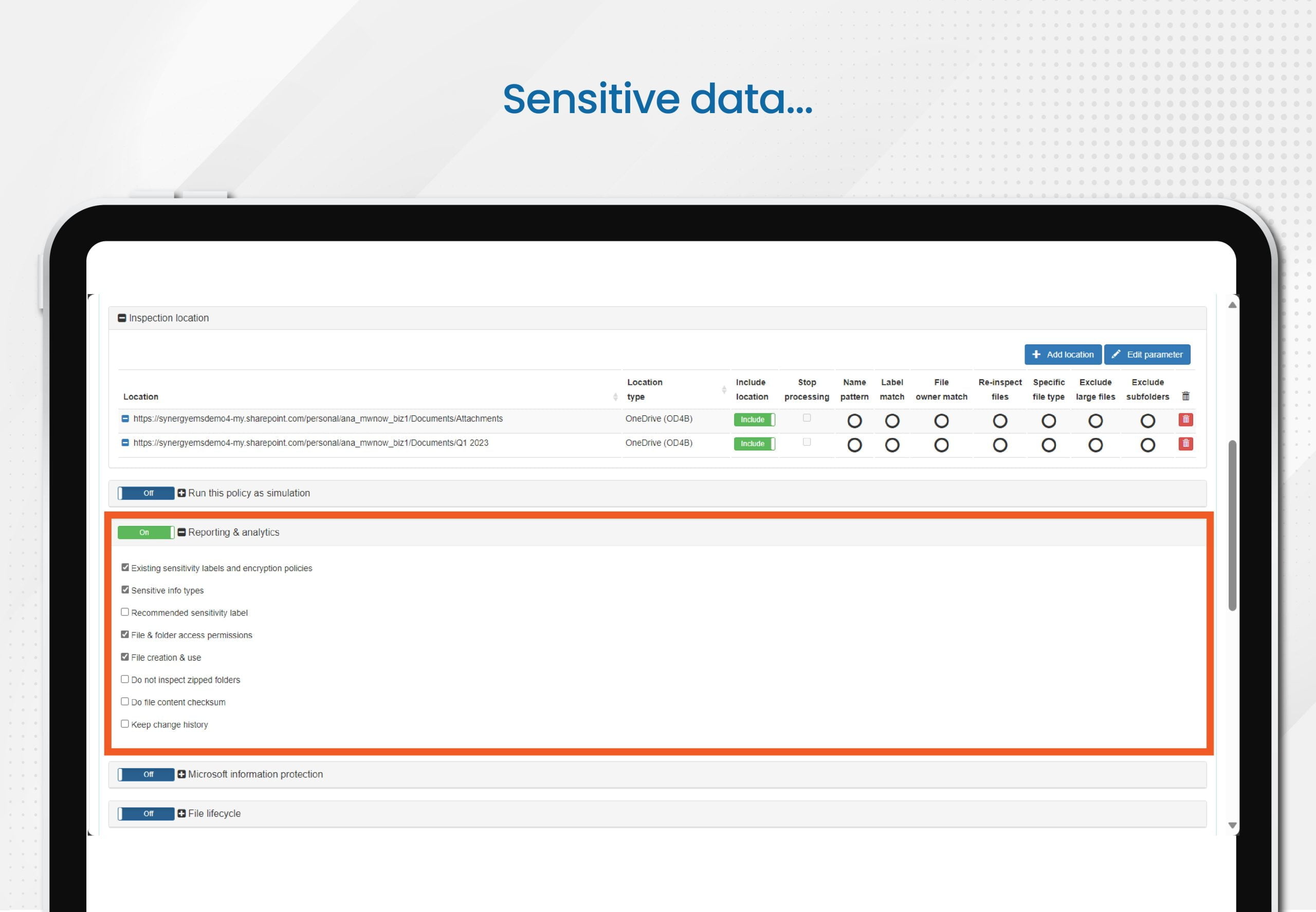
You can choose which data to include in your reports. Select key attributes crucial for your business and showcase only what truly matters. E-Inspector allows you to apply specific filters for in-depth data analysis. Present your analyses in a visually appealing and easily understandable manner with charts and tables that help communicate your findings effectively.
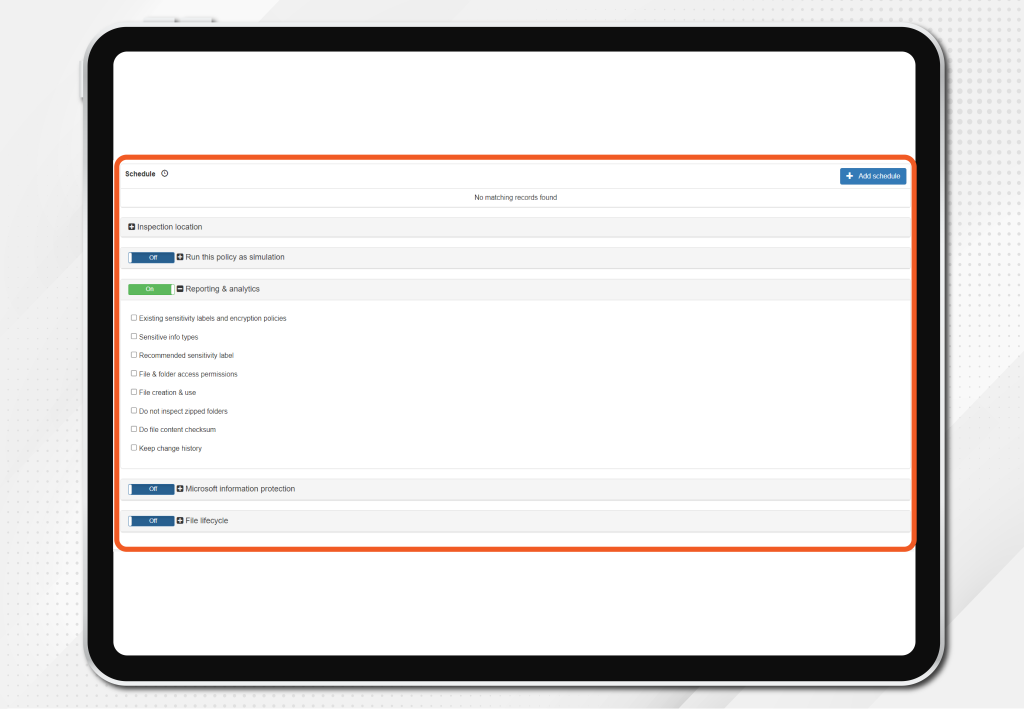
- Move the original file
From the filter set, you can move the file to a different path



- Delete the original file
From the filter set, you can delete the file



- Archive the original file
From the filter set, you can archive the file



- Recycle Bin
Also note that we offer a way to restore some of the changes to the files
- For this you can specify an Azure Blob storage repository so you can get these files back as needed.
Happy? Of course! Currently you have made tremendous improvements, not only for the sake of compliance and data protection, but also to ignite your organization to get the most of best-in-class AI through M365 Co-pilot!
Hopefully, at this stage you have a clean state; however, … for how long? More and more data is created as we speak! Data is edited and moves across the organization. Some of these data lifecycle actions can lead to holes in your carefully curated compliance remediation. See in our next blog article how you can keep your environment shielded so nothing can slow down your Copilot use.
MORE INFORMATION – Similar topics
- Blog 1…
- E-Inspector Overview
- E-Suite Overview
- E-Suite Offerings [E-O]
- E-Suite Discovery Offerings [EDO]
- Others



