Introducing E-Racer
Keep your data protected and always be ready for your users to leverage Copilot for Microsoft 365
In my last 3 blog posts, I briefly mentioned that we can come with some strategies to simultaneously bring your O365 platform into compliance and enable your end users to get the most out of Copilot for M365. After we help you discover and protect, you can govern and keep your M365 environment in compliance, but how can you keep up?
From the collaboration standpoint, let’s keep the following considerations in mind:
Data “at rest"… its not that calm
- Data…. changes!
- A document that was not considered sensitive may become sensitive after critical data is added to it
- New data
- From M365, fresh new data, or new versions of documents, may pop-up anywhere
- Teams chats
- Teams Channels
- Teams meetings
- All this new data will end up in
- SPO
- OD4B
- Desktop Synced with OD4B
- From M365, fresh new data, or new versions of documents, may pop-up anywhere
- Human factor
- People will continue making mistakes
- Uploading files to the “wrong” path
- Overexposing data to people that should not have to have access to it
- People will continue making mistakes
Technical constraints and considerations
- If you are thinking about scanning across your entire tenant, that is a gigantic task; ideally, you will not do it that often!
- Consistently scanning the entire tenant would be very expensive, not only in time but also in resources. To go over the content in this manner may take months/days to “revisit” a document again after its previous scan
The biggest limitation with the above is the 25k files per day and up to 100 auto-labeling policies and locations per tenant. For some larger organizations, it would be impossible to scan their infrastructure, as they have too many legacy files, and the number of files that can be scanned by M365 cannot outpace the number of net new or edited files that users upload/modify.
This process does not prioritize new or modified files; instead, it prioritizes specific paths and folders. For some organizations, where new and modified files may even outpace the inspection limit, the inspection process cannot keep up with user output.
- Besides the M365 capabilities, there is a challenge for any app that wants to consume a SaaS service, as the service providers (in this case, Microsoft 365) have their own way to set boundaries how much an API can be used. For example, using Graph API, a solution can scan a certain number of files per day. The service provider can slow down the response time or require the app to wait until the “next period” before continuing with the remaining files.
As you can see, out of the box, custom dev tools have a dramatic impact on the “how long/how soon” question and these limiting factors may not enable a timely compliance response to new or modified files. What are the options then? See the next section where Synergy Advisors has expanded our E-Suite solution portfolio to help businesses of all sizes to not just scan the entire environment, but then to keep it in the best shape possible.
E-Racer
Since E-Inspector v3.5, we have introduced several tasks that go beyond affecting the file itself. For example, E-Inspector can automatically perform tasks like label, encrypt, move, copy, and delete files. It can also simulate (what if?) actions prior to performing them.
E-Racer comes to play in the following scenarios:
- We will focus on just recent activity, regardless of past actions
- Scan content based on a schedule
- Scan content (diff that has changed) after some time (E-Quick Scan)
- One of the most impactful benefits is that we can go after content based on activity; this service prioritizes scanning the following:
- New files
- Updated files
- This includes the share links activity, including new shares or modifications such as adding or removing people
- You won’t have to incur costs associated with full scans, unless you want to take specific actions to previously scanned docs such as
- Relocating
- Rescan due to updated data sensitivity definitions made in your platform
- (New sensitive information type that you would like to find in your O365 files)
- Applying sensitivity labels (Purview IP)
E-Racer Actions
Let’s go over the different actions you can apply
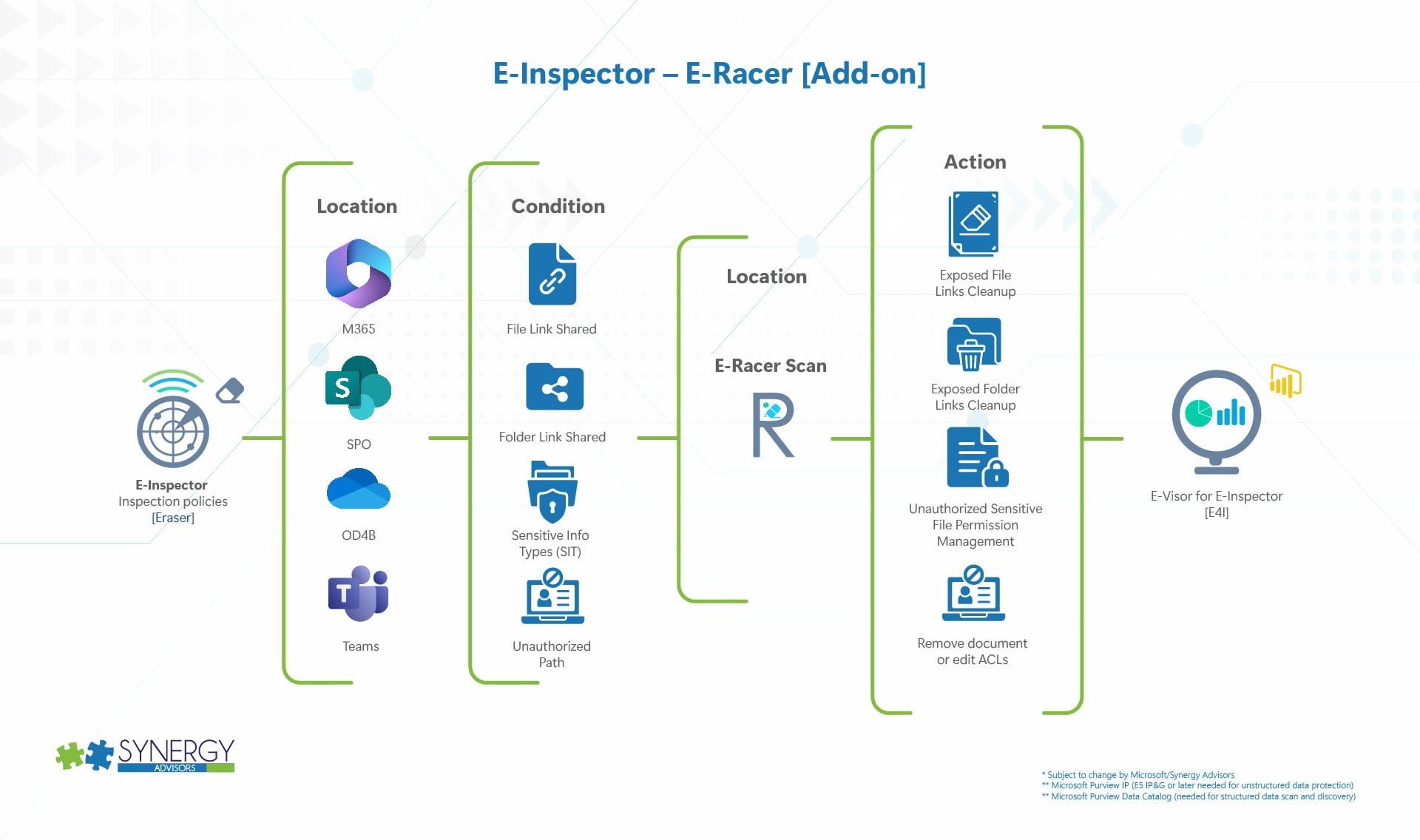
File Actions
- Move, copy, delete
- Apply and change Purview IP labels
- * Quarantine (Coming soon) / Available only when E-Vigilant corresponding capabilities are installed
File Share Links
- Remove overexposed share links (such as the entire organization) / specific groups of people
- Remove external/external-social
- ** Remove from the general list of specific groups identified as overexposed/general groups at your organization
E-Clearance Actions
- E-Clearance is an additional service (add-on) available to work with E-Racer; with E-Clearance, you can define
- Authorized
- Users with
- Access to specific sensitive data
- Clearance to access content with specific sensitive labels defined at your organization
- Paths
- Locations allowed to keep specific kinds of data
- Unauthorized
- Control users that should not have access to specific kinds of data
- Control locations that should not contain specific kinds of data
* Depending on E-Inspector SKU, E-Clearance may require a separate E-Suite add-on subscription
Teams App User Activity
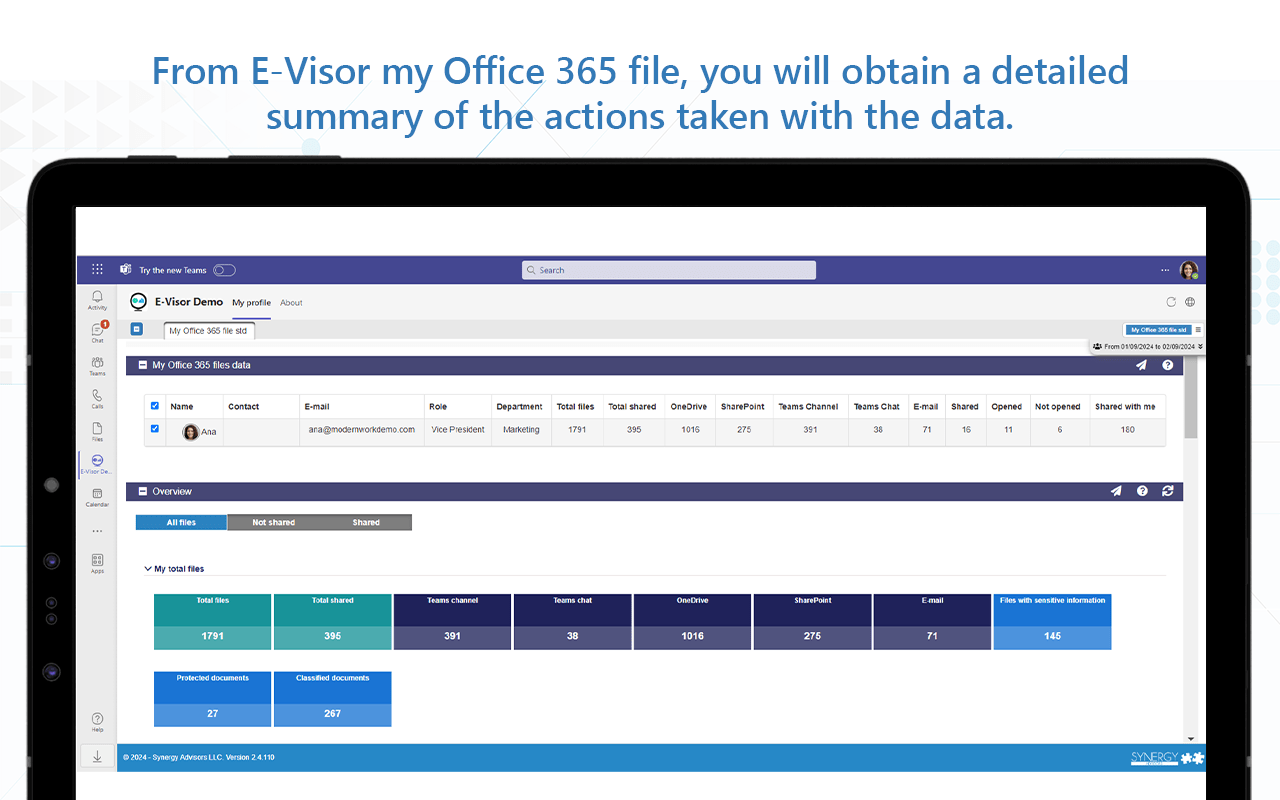
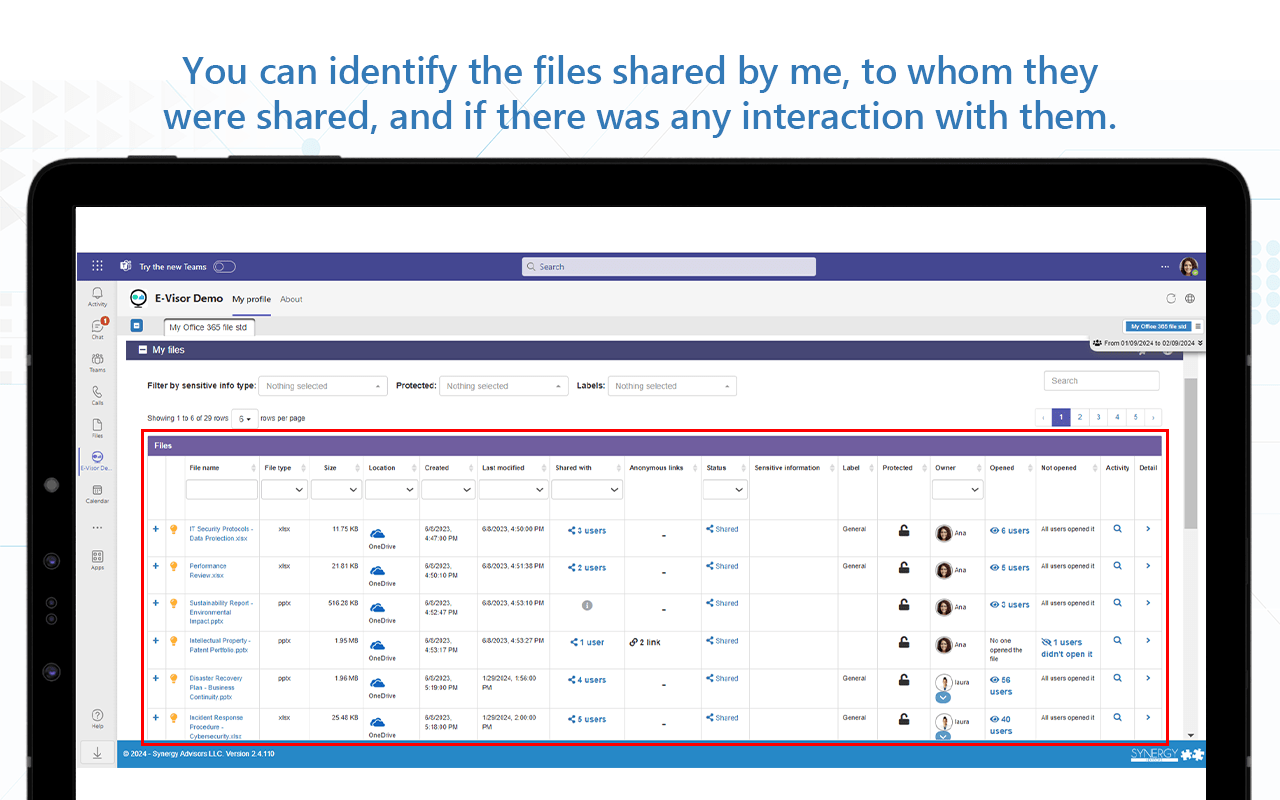
- Our E-Visor Teams app can provide general insights to end users about the documents they’ve opened or shared and even mention to an author or recipient when a new file has been shared, used, downloaded, or contains sensitive information
- Simplified collaboration
- Users can see all activity related to the data they create and share, from a centralized location
- The solution also provides visibility to specific files activity in such a way that users can validate the dynamics related to the shared docs
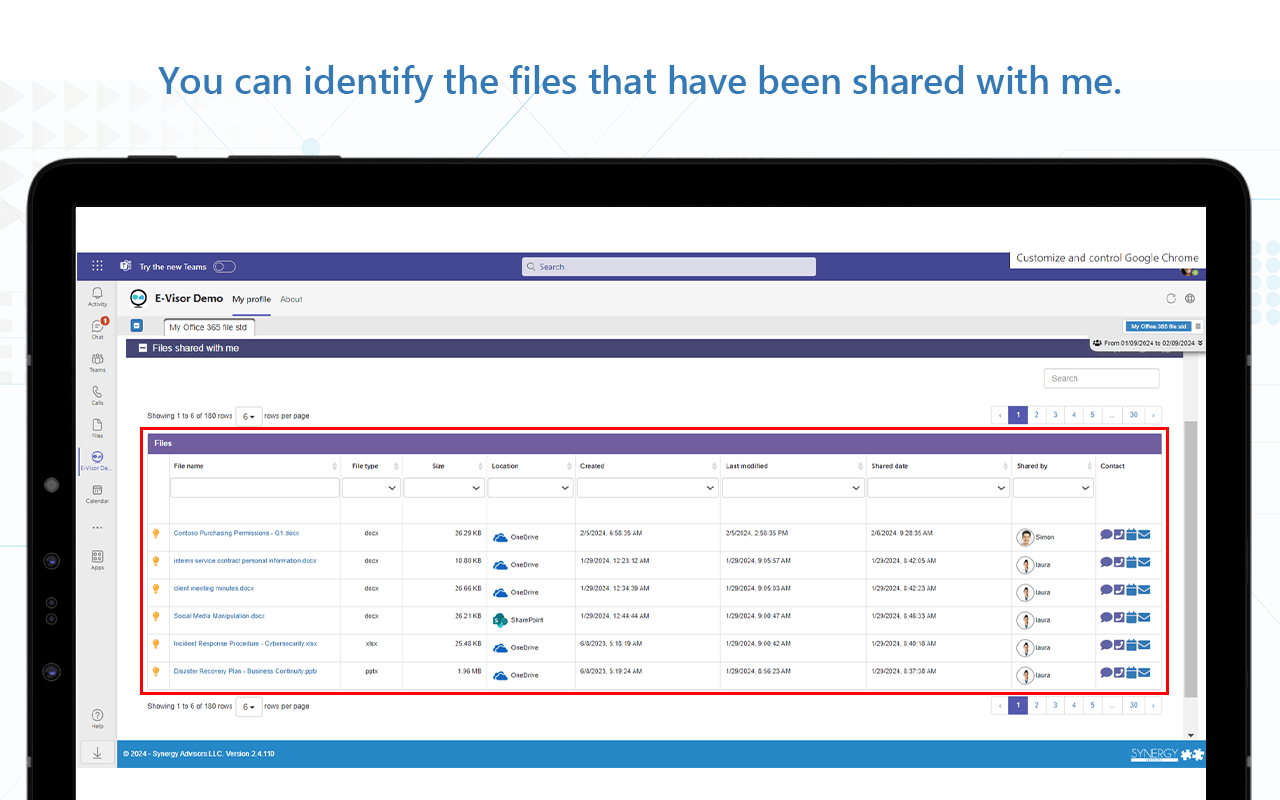
- Users can change share settings or stop sharing altogether right from the Teams app
- User Education
- As the tool also provides notifications, users can identify the following:
- Sensitive data in shared files
- When a file has specific label/protection applied
- We provide tips and reminders when a document is sensitive and has to be handled with care
* Depending on E-Inspector SKU, E-Visor Teams App for the end-user may require a separate E-Suite add-on subscription
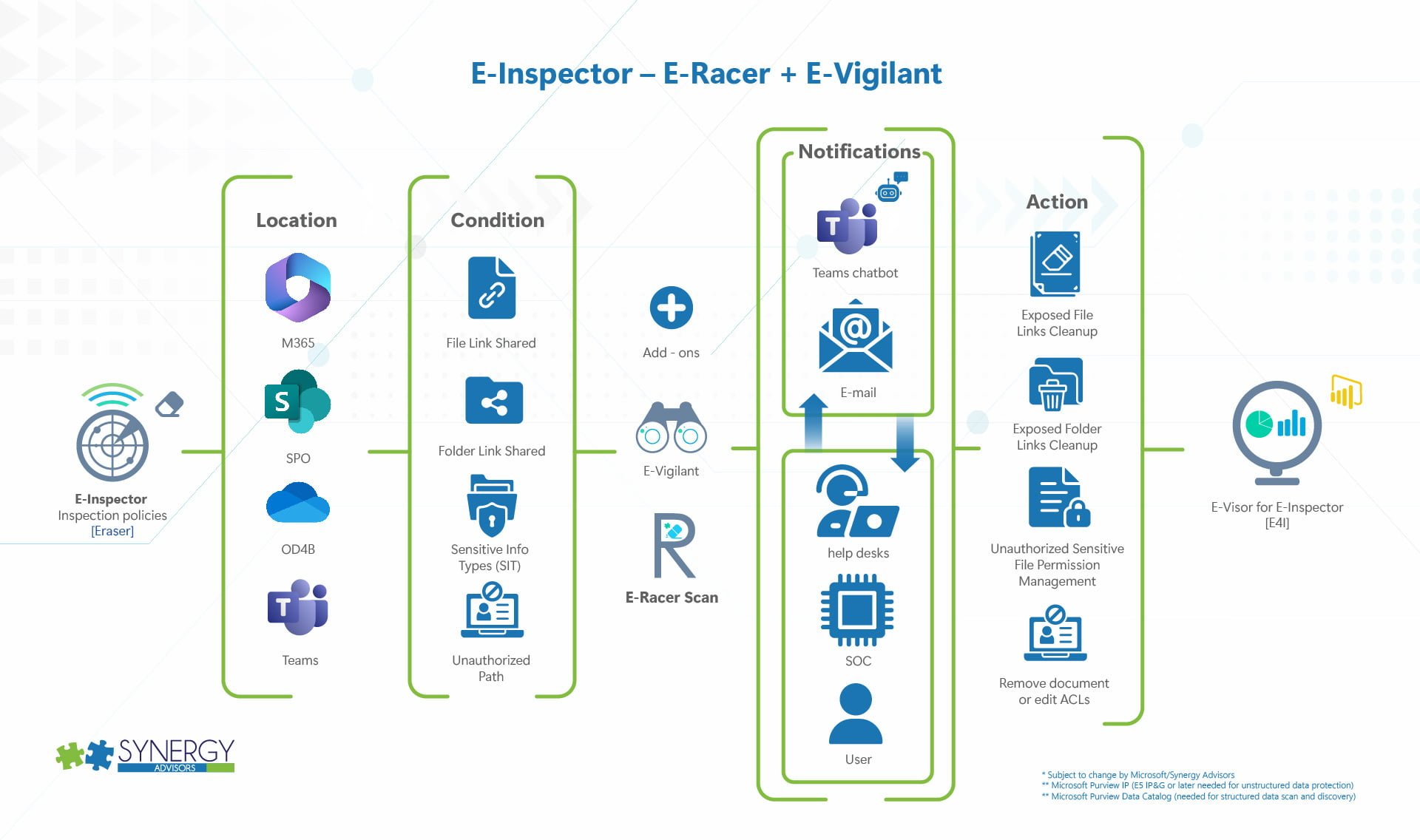
Chatbot Notifications and Workflow-based Actions
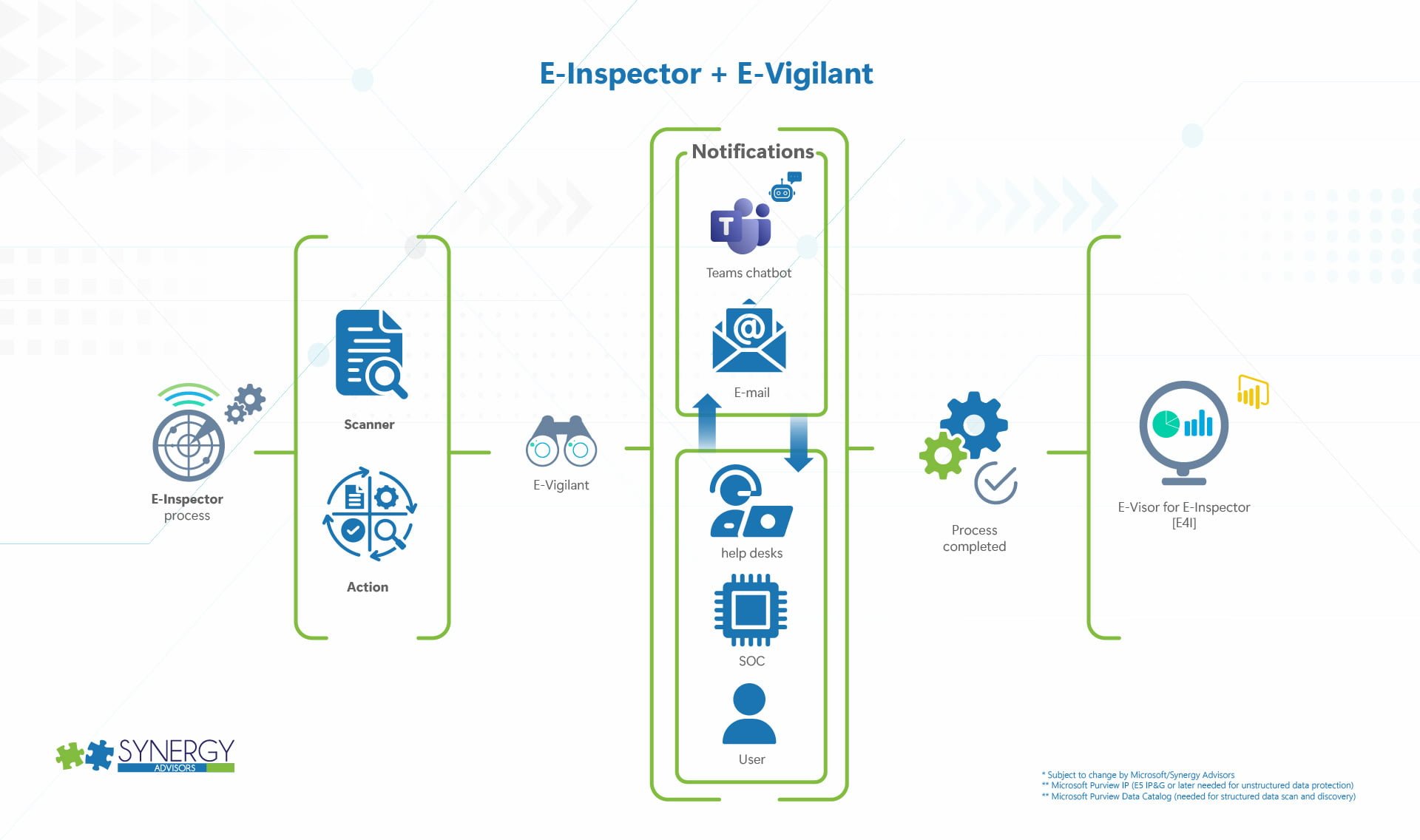
By default, the E-racer activities are performed without user intervention or notifications. Technical personnel can see the activity within the E-Visor for E-Inspector reports.
However, we can also involve different users, such as the author and recipients, in the process. For example, you may want to interact with the user PRIOR to removing a link or stopping a share. You may want to proactively notify an author to explain why a file was labeled with Purview IP. For these use cases, and beyond, you can leverage another E-Suite technology called E-Vigilant
- E-Vigilant additional actions
- Chatbot
- You can let users know about a decision made, you can provide education, you can redirect them to specific training/documentation where the user can learn more about protecting sensitive data, and more.
- Workflow
- Beyond a delete /notify action, you can set workflows where the manager, or another stakeholder, can also be informed of the activity. You can even confirm if the manager approved the use of this kind of sensitive data and activities
- This can also let the manager or user select a different action (such as move the file) that your organization would like to have including the generation of a more restrictive link that can, for instance, exclude externals
Path actions
- E-Racer can also check for ACLs misconfiguration. This means you can have per site and document library a baseline configuration that our system can check and correct as necessary. Note that this can be connected with a baseline configuration.
- As mentioned before, this can be also considering actions based on E-Clearance collections.
Site Configuration
- In addition to specific paths, we can review specific settings related to group of people allowed to access specific sites, and the kind of links allowed. This can also be set as a baseline configuration to specific paths that can be auto-corrected, chatbot confirmation corrected, and, of course, users can be notified about the change.
Global Configuration
- In addition to specific paths, we can review specific settings related to groups of people allowed to access specific sites, and the kind of links allowed. This can also be set as a baseline configuration to specific path that can be auto-corrected, chatbot confirmation corrected, and, of course, users can be notified about the change.
E-Racer best practices
- As you start defining the baseline and actions, perform an E-Inspector simulation.
- This will provide you with a better understanding of all the different policies and actions that can be taken by E-Inspector and what the user will experience, such as changes to classified files, ACLs, and share links.
- This can help you polish the rules and see the user actions when leveraging E-racer.
- This will help the compliance/solution owners and SharePoint sites owners validate and optimize how the process will be going forward.
As you have seen, you can not only align your environment with your data collaboration policies, which will naturally make it ready for “Copilot for M365,” but also keep it optimized by combining solutions like E-Inspector and E-Racer with Microsoft SPO Security and Microsoft Purview!



