
- Zero Trust
- Dec 30
- Comments (0)
Beyond the cybersecurity trends that 2023 bring us
At this time, it is very common to find many posts, articles and documents about cybersecurity trends that are on the way with the arrival of the new year; Although, in some cases, the trends set out differ from one author to another, in general terms many of these coincide and the industry is moving towards it.
From Synergy Advisors, our team of experts have analyzed the trends raised by some of the most important expert companies in the industry to deliver this article today with nine trends that make most sense, facing the reality that we find in our clients and the market. But that is not all, in addition to telling you about these trends and predictions, today we want to share how Synergy Advisors can support organizations to be prepared for them and for the potential challenges your organization be facing in 2023 and subsequent years.
1. Ransomware continues to be a headache
Expected is a record year for cybersecurity breach notifications, not only because of the sophistication of threat actors, but also because of substantial changes in the world that will affect an organization’s ability to mitigate, remediate or prevent a problem. With the distinct possibility of a global recession on the horizon, we expect to see ransomware attacks spike in 2023. However, larger organizations in regions heavily impacted during the ransomware boom are the most prepared for this wave after investing time and money in fighting back.
At Synergy Advisors we have a comprehensive portfolio designed to support organizations face cybersecurity challenges, adding a productivity and user experience component to it. From our CONSULTING services we support you in the implementation of security solutions that enable to anticipate and respond to security threats. Likewise, through our MANAGED SERVICES, we provide best in class, end-to-end, proactive and reactive IT operation services, leveraging Microsoft 365, Azure, and proprietary solutions across several scenarios and threat protection.
But that’s not all, our proprietary solution E-Vigilant is an advanced analytics and alerting tool that uses Microsoft solutions to collect information from different sources (workloads), alert different audiences to different types of incidents, provide a comprehensive view of the cybersecurity ecosystem, and facilitate more effective management.
2. Consolidation of providers
As budgets tighten and economic uncertainty takes center stage, a key CISO metric for the coming year will be to consolidate security solutions from multiple vendors, thereby reducing risk and saving cost.
Palo Alto Networks, an American cybersecurity company, argues that shifting the focus towards converged platforms for SASE, XDR, Cloud and within the same SOC will be vital. Going a step further, security teams will need to align these efforts with overall business value metrics, thus ensuring levels of protection based on the risk level defined by the company.
We have technologies, people and processes that enable us to deliver state-of-the-art SOC services that converge and complement each other, enabling organizations to have a single service provider that comprehensively covers security needs. Some of our services include:
- Cybersecurity Monitoring
- Network Security
- Correlated Incident Management
- Application Security
- Threat Protection and Intelligence
- Managed Detection and Response
3. Cloud security
The need to provide an optimal user experience, regulatory concerns, and data protection in the cloud will be trending in 2023. Social engineering begins to wreak havoc in the cloud, and attackers will shift from their software toolsets to their powers of persuasion designed for the cloud, focusing its attention on entrepreneurs and organizations that are amid this transition, or looking to migrate to the cloud.
Synergy Advisors has developed a comprehensive offering for repository modernization and secure data migration to the cloud, including integration with cloud tools to ease the transition. This offering will help you centralize organizational information, take advantage of the capabilities of cloud repositories and the document management capabilities they provide in a secure manner, protecting data end to end.
- Inspection of several data sources
- Detection of sensitive data
- Document protection using MIP and DLP
- Migration of the data to the cloud
- Monitoring and reporting of the unique environment by E-Suite
Learn more about this offering HERE.
4. Identity management issues
A push towards non-federated identities will help provide a new level of services, however, if not managed correctly this can pose a higher level of risk in terms of security and potentially become an identity and access control nightmare. The size and scope will feel truly infinite, which malicious actors can exploit by generating, in addition to security breaches, an additional burden and a greater investment of time in management.
The best of our portfolio comes together to create an Identity Governance strategy for our clients, supported by Microsoft Azure AD and powered by the power of our E-Suite:
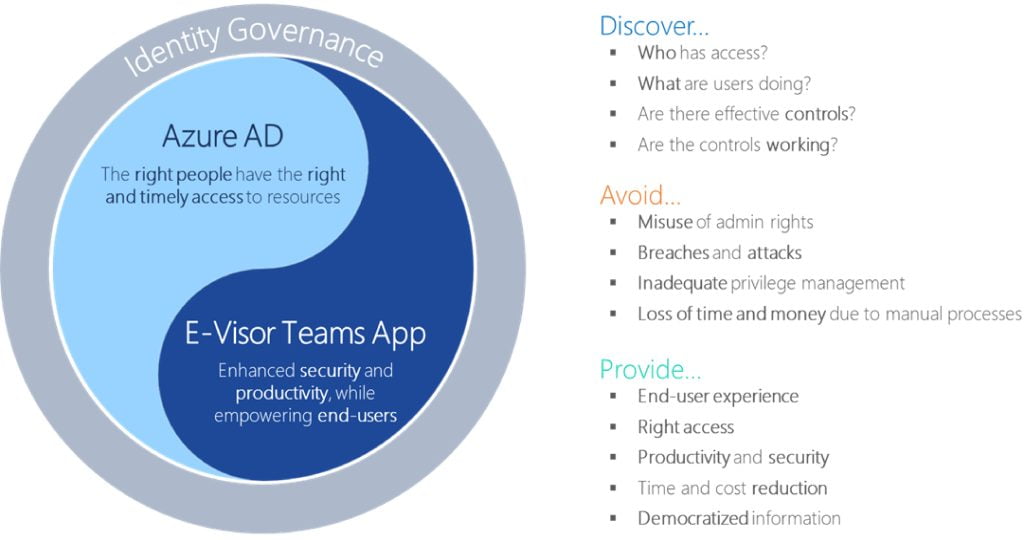
Contac us to get a free consulting session to discuss about your needs on identity governance, HERE.
5. Challenges of hybrid work
In 2023, with workers more likely than ever to use personal devices to connect remotely to work networks, a new set of challenges has emerged, in a scenario with higher levels of risk and where these devices are used for work and left unattended.TTechnological growth derived from the increase in hybrid and remote work modalities will also bring some risks. Next year will see mass adoption of 5G capable devices: Juniper Research estimates that there will be six hundred million more 5G connections added in 2023 alone. Technological trends will be compounded by demographic trends, such as “productivity paranoia,” where workers want to show they are being productive, no matter where they are. What does this mean for CISOs? New working styles, new networks, and new devices mean new attack vectors. In 2023, be ready to protect your workers who are working from anywhere, not just from home.
The E-Suite set of solutions, developed by Synergy Advisors, was designed to meet two main objectives: improve security posture and increase productivity, with special emphasis on the remote and hybrid workforce, democratizing information, empowering employees, and providing a robust layer of security involving users at all levels, not just Security and IT departments.
How do they E-Suite solutions that?
Synergy Advisors’ E-Suite is a bundle of solutions that seamlessly intertwine with each other and with Microsoft 365. They help extend the features and functionality of different Microsoft 365 services to provide analytics, alerts, self-service actions, incident management, data governance, and meeting optimization, to solve advanced use cases we have found common amongst many of the organizations we have worked with.
E-Suite solutions:
- E-Visor: Optimize analytics, monitoring, and security with rich data presented in Power BI reports.
- E-Visor Teams App: Collects information, presents it and alerts end user about their identity, device, information, productivity, and more, all inside Microsoft Teams
- E-Vigilant: Analytics and alerting solution that notifies about security incidents, integrated with ticket platforms.
- E-Inspector: Enterprise automated discovery, audit, and protection of stored sensitive information.
- E-Cryptor: Document lifecycle management and governance while improving data control.
- E-Migrator: Easy and quick Zoom to Teams migration
6. AI in cybersecurity: a double-edged-sword
According to IBM, companies that use AI and automation to detect and respond to data breaches save an average of $3 million compared to those that do not. However, thanks to the increasing availability of AI, hackers and criminals are also becoming more adept at using it, using it to identify systems with weak security and/or to create several personalized phishing e-mails, designed to evade automated e-mail defense systems.
Our extensive Consulting portfolio includes technologies and services for e-mail protection, secure collaboration, device protection, information protection, threat protection, and platform protection. To face this specific concern, Synergy Advisors can provide the best of market for e-mail protection, including:
- Routing optimization
- Passwordless authentication
- Sanctioned and unsanctioned applications control
- E-Mail services hardening
- E-Mail secure access services
- E-Mail advanced threats protection
- Advanced data encryption
- Data leak protection
7. Cybersecurity culture
Today, it is no longer enough for employers or employees to consider cybersecurity only as an issue for IT to deal with. In fact, developing threat awareness and taking basic precautions to ensure security should be a critical part of everyone’s job description in 2023.
You do not need to be technically savvy to learn how to be aware of the distinct types of attacks leveled towards each employee and take basic precautions to avoid falling victim. Similarly, basic security skills, such as the secure use of passwords and an understanding of multi-factor authentication (MFA), should be taught and continually updated. Taking these kinds of basic precautions to foster a culture of cybersecurity awareness should be a central element of the business strategy for organizations that want to ensure they are prepared and resilient over the next twelve months.
CISOs need a novel approach to shed light on these growing concerns. Beyond implementing the right technology, an organization needs a strong security culture . The needs, concerns, demands, and habits of an organization will help security leaders better “speak the language” of staff to ensure effective training. Educate all users within the organization on how, with simple actions, they can help support security, data privacy, compliance, and risk management, which will help to reduce costs and increase productivity, while letting users know when and how much they can help, and when they need to reach out to IT.
We can help strengthen the cybersecurity culture of your employees through our E-Visor Teams App solution, designed and hosted inside Microsoft Teams. E-Visor Teams App is a centralized place to involve and empower your end users in the security and productivity of the organization by presenting unique information leveraging data from Microsoft 365 and Azure Active Directory, while ensuring identity governance.
[FREE: Download a trial version of E-Visor Teams App and test its power]
Likewise, we offer your organization the ‘Azure Perimeter 4-Day Training’, made up of strategic sessions, masterclasses, and hands-on labs, designed to take the user on a journey through the main models, concepts, and protocols related to managing, securing, and monitoring your corporate network. In 4 days, your team will learn best practices and tactics in network design, architecture and topology, network types, operation, perimeter protection, policies, and security from a Zero Trust model perspective. Learn more HERE.
8. Issues when implementing Zero Trust
Now that it is finally more than just a buzzword, security teams will accelerate zero trust adoption plans in 2023 — and make several missteps along the way. Without a deep understanding of trust relationships, implementations will fail. We already see security teams building “less trust” rather than “no trust” architectures, which opens the door to security gaps that adversaries may take advantage of in 2023.
For several years we have worked and supported many clients around the globe in the correct implementation of the Zero Trust model as the fundamental basis of their security strategies; Our portfolio has been developed based on this disruptive model, addressing different scenarios in which we can support your organization, such as:
- ZERO TRUST IDENTITY ARCHITECTURE
- Protect modern and legacy enterprise assets
- Protect all apps and services that the network simply cannot reach
- SOC MODERNIZATION
- Advanced threat protection and response
- Identity
- Devices
- Applications & collaboration services
- Cloud infrastructure
- SECURE ADMINISTRATION
- Protect all administrators’ credentials
- Create a secure administration workstation
- RESOURCE MODERNIZATION
- Enable Zero Trust for legacy applications
- Modernizing application architecture
- Secure publishing applications over the Internet
- NETWORK TRANSFORMATION
- Enable network segmentation for legacy applications
9. The end of basic authentication
In 2023, we expect to see cyber criminals set their sights more specifically on MFA technologies. With some attackers having succeeded at circumventing non-phishing-resistant MFA this past year — and more organizations relying on it than ever before — this technology will grow as a top target next year.
On the other hand, cybercriminals will continue to leverage large caches of leaked/stolen credentials to devastating effect. Consumers and businesses are gradually migrating to password managers, passwordless and hardware identity tokens. However, most of the population continues to reuse credentials or variations of credentials between environments, systems, or sites, becoming the basic and legacy authentication the target for phishing and other attacks next year.
As many organizations know, this year some initiatives have emerged that encourage the elimination or revocation of basic authentication technologies/features from their systems and resources. October 1st was the deadline set by Microsoft for the deprecation of basic authentication in its clients, an event in which we support many of our clients with our offer of Passwordless solutions.
On the other hand, The White House released Executive Order 14028 in May 2021, covering many key areas that need to be addressed to protect critical digital infrastructure. This is one of the most detailed U.S. executive orders on cybersecurity released by the White House, and affects many organizations, both in the public and private sector, that work with the government.
[BLOG: Learn more about the Executive Order 14028]
Most notably the executive order contains a number of specific mandates related to assessments, reports, and the deployment of specific security tools, such as multi-factor authentication (MFA), encryption, and zero trust architecture (ZTA).
[VIDEO: Benefits of Multi-factor Authentication – MFA]
Synergy Advisors has developed, and is constantly updating, a comprehensive PASSWORDLESS offering that enables organizations to eliminate passwords, adopt advanced technologies for access and identity protection, and enable them to rapidly advance in meeting the Executive Order 14028.
Get to know the complete offer of Passwordless HERE.
Sources:
- Microsoft
- Forbes
- IBM
- Palo Alto networks
- BeyondTrust
- Trend Micro



