Protect your organization’s devices using the E-Visor Teams App and Microsoft EndPoint protection technologies.

Hello again, everyone!
Today I am super excited to share with you some significant improvements that will show up in the next GA release of our E-Visor Teams App:
An end-to-end view of the health of users’ devices from the cyber security perspective, without those users needing to be an expert or an IT Admin to be able to see how secure the devices they are using are. This update to our app comes as part of the promise we have to all our existing customers who are embracing this new hybrid work reality, dealing with people working from anywhere and from devices beyond their corporate ones to access corporate information, SaaS, and other resources.
Overview – Simplicity is the key to get quick results
Before jumping into our solution discussion, let me mention a fundamental aspect we are looking to solve in a practical manner: the constant dilemma that some “Cyber Experts” are struggling with: The CyberSecurity Dilemma not helping our Zero Trust Efforts – Simplicity is key
It is funny to see how many non-technical people, and even some technical people, see a HUGE mountain to climb when talking about CyberSecurity, Zero Trust, Defense in Depth, and the never ending list of acronyms used (SSO, SAML, EDR, AV, AS, MDM, MAM, Reverse Proxy, CASB, SIEM etc. etc.).
Organizations are providing all kinds of technologies to protect customers; however, that does not guarantee a successful landing of your awareness campaigns, but why?
Users can easily get overloaded by information: Do not expect people will know things to the same level you do and, do not get me wrong, we all are learning about new risks and techniques used by attackers continuously.
The question is how to sim plify and provide a key message so non-technical people can get just what they need to know and what need to see. Hopefully this info is available in just one click in a summarized way that can drive auto-resolution and fewer (or shorter) calls to your help desk and additional support tiers in your organization.
plify and provide a key message so non-technical people can get just what they need to know and what need to see. Hopefully this info is available in just one click in a summarized way that can drive auto-resolution and fewer (or shorter) calls to your help desk and additional support tiers in your organization.
When talking to people about zero trust at Synergy, we want to keep it SIMPLE for everyone (yes, even the IT/Cyber experts):
End user simplicity!
I should know from a quick review, without training or a technical dictionary, if my devices are at risk or not. It’s as simple as that; all that info should be in a centralized location to get guidance for things that can drive self-service.
- No need for multiple links, applications, or technologies! Users need simplicity, just a scorecard and some info to take corresponding actions
Administrator simplicity BUT comprehensive!
IT support should not have to open multiple management consoles to review logging and alerts, end-user device status, and more. The quick “go to place” should also be provided to them so they can effectively assist users while saving time and resources.
- Let me be straight on this: most of the IT management consoles are great for broad goals, such as to create rules that reveal high level insights. Typically, they lack the necessary diagnostics and cyber inspection with insights across multiple technologies as they work in silos. Even reporting from solutions across the same provider are moving really slowly towards a centralized view. Furthermore, not all organizations and teams may have such analytics capabilities available, so:
Let’s see how the E-Visor Teams app can help the entire organization deal with these challenges!
My Devices – E-Visor Teams App
- Understand, and able to identify, actionable insights that can optimize your devices’ security posture
- All of this using a multi-layer/technologies approach
- See what kind of benefits this will offer to you
Simplified “one pane of glass” to see end-to-end cyber security health of devices in Teams:
Summary
Operating Systems Get to know the supportability status and more for your W10 devices and beyond- Device protection 101 If your device is not patched, you are vulnerable. Regardless of how many apps you have on top of the operating system, there is a limit to the protection that can be offered and probably a significant list of capabilities that cannot be fully leveraged.
* Note that “compliant” here reflects if the technical configuration of the device is aligned with the technical compliance policies set by your organization
Advanced Threat Protection Status Sophisticated attacks are on the rise and, to combat this, there are new technologies to review suspicious activities happening in the devices, even if they are not “seen” by the human eye at first. If you own, for instance, Microsoft Defender for EndPoint (MDE), you can mitigate those attacks and make IT aware of those risks. We, of course, also help provide information related to activity on your devices.Details
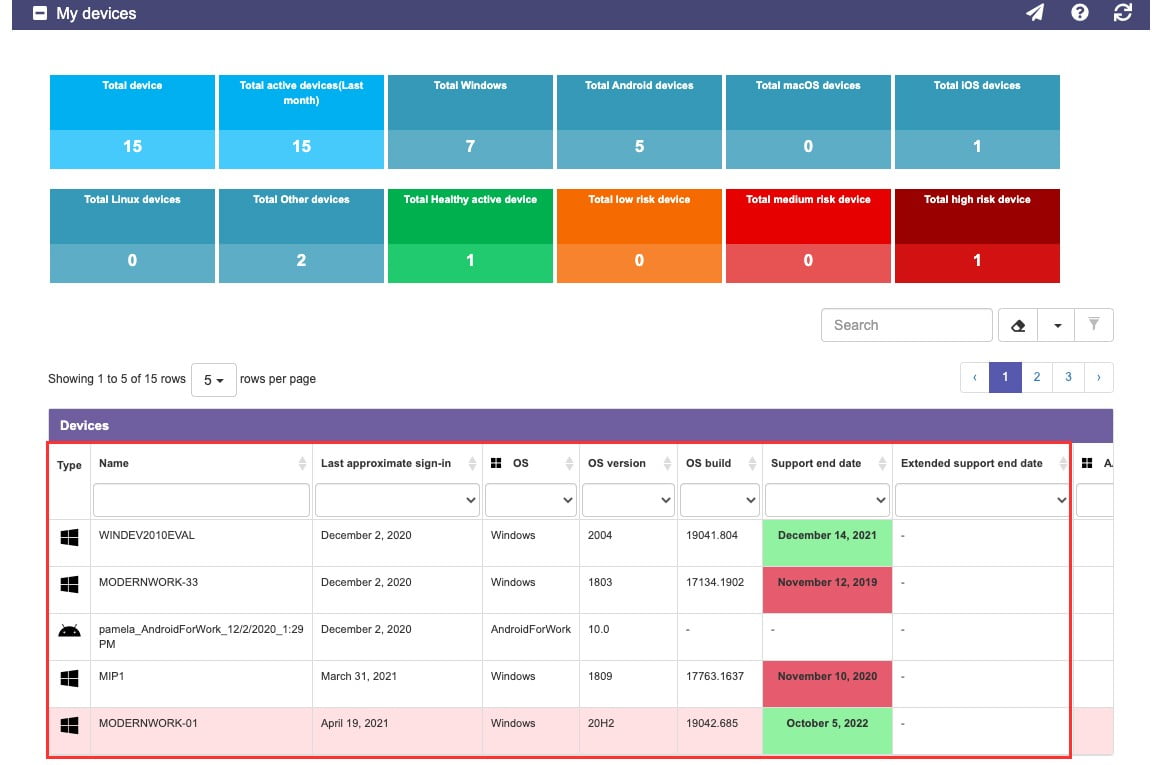
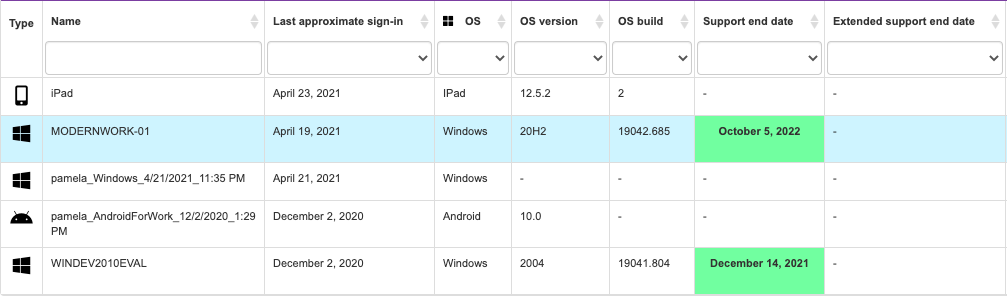
The following picture shows the all new “My Devices” section. Notice that you can filter using the boxes on top to narrow in on devices by platform, health state, and more.Operating System Information
Get to know general information about devices that have been used with your user account to access corporate resources:
| Functional name | Values | Explanation | Benefit | |
|---|---|---|---|---|
| 1 –Type | An icon representing the OS platform of the device | You can see here what kind of devices have been used with YOUR credentials to access corporate resources | Simply identify existing, and maybe forgotten, devices used in the past where you may leave your credentials in cache (browser question), such as a device belonging to a friend, one of your kiddos, or a relative. Yes, we tell you where you have logged in, right from the E-Visor app! | Microsoft Link |
2-Name | Name associated to the device you are using | Although self-explanatory, keep in mind this will give you a hint if you used a device you do not regularly use | Quickly identify your devices based on their associated names | Computer Names Locating Names |
3-Last Approximate sign-in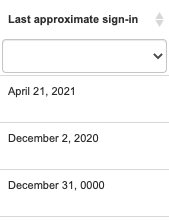 | The last time you used this device | Watch out!!! Here you can see how far away your user account was used to access corporate devices or resources | Identify the last time your credentials were used on thedevice | Microsoft Link |
4-OS | Details about the operating system used | (Product name) | Identify the operating system used | |
5-OS Version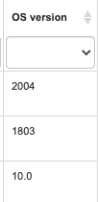 | For Windows devices, this is a critical value to identify how “up to date” your device is with Microsoft Updates | If a device does NOT have the latest version, chances are REALLY high that you are at a significant amount of risk. These updates contain sometimes not dozens, but HUNDREDS of patches to fix security vulnerabilities | Here we can save you significant steps to investigate the OS version per device In a few columns you will get a semaphore indicator of how much support time is left before expiration; get your device updated!!!!! | Microsoft Link |
6-OS Build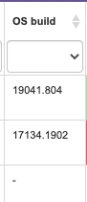 | Technical details that some of your support people may ask you for | Support should be able to confirm if any internal apps or security issues are related to the OS build, so keep this handy | Microsoft Link | |
7-Support End Date | The value presented here is CRITICAL to confirm how up to date your device is. More importantly, if the device is listed here in RED with an expired date, you may be out of support and urgently need to update your device | This list is based on the official support page from the different platform providers | Quickly identify potentially risky devices, so that they can take the necessary corrective measures [OS upgrade] | Microsoft Link |
8-Extended Support 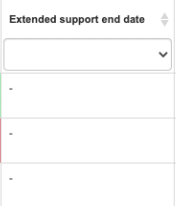 | In case your regular support shows as expired (Red), your organization may have purchased extended support. We also list when this expires; however, there is no guarantee it is applicable to your specific organization | Remember the best practice is that the value be in green. If it’s not in this condition, you may miss critical updates. It is NOT enough have the device in support; that’s the very minimum, so go ahead and patch it! | Quickly identify risky devices, so that they can take the necessary corrective measures [OS upgrade] | Microsoft Link |
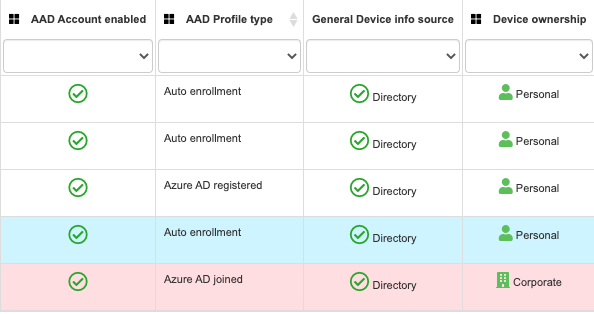
Corporate Device vs Personal Device Configuration
Depending on device configuration, see if your devices have been configured as corporate managed or personal devices. This validation has drastic implications about what kind of corporate resources you have access to and if the user experience can be simplified with less authentication prompts when accessing applications:
| Functional name | Values | Explanation | Benefit | Technical Reference |
|---|---|---|---|---|
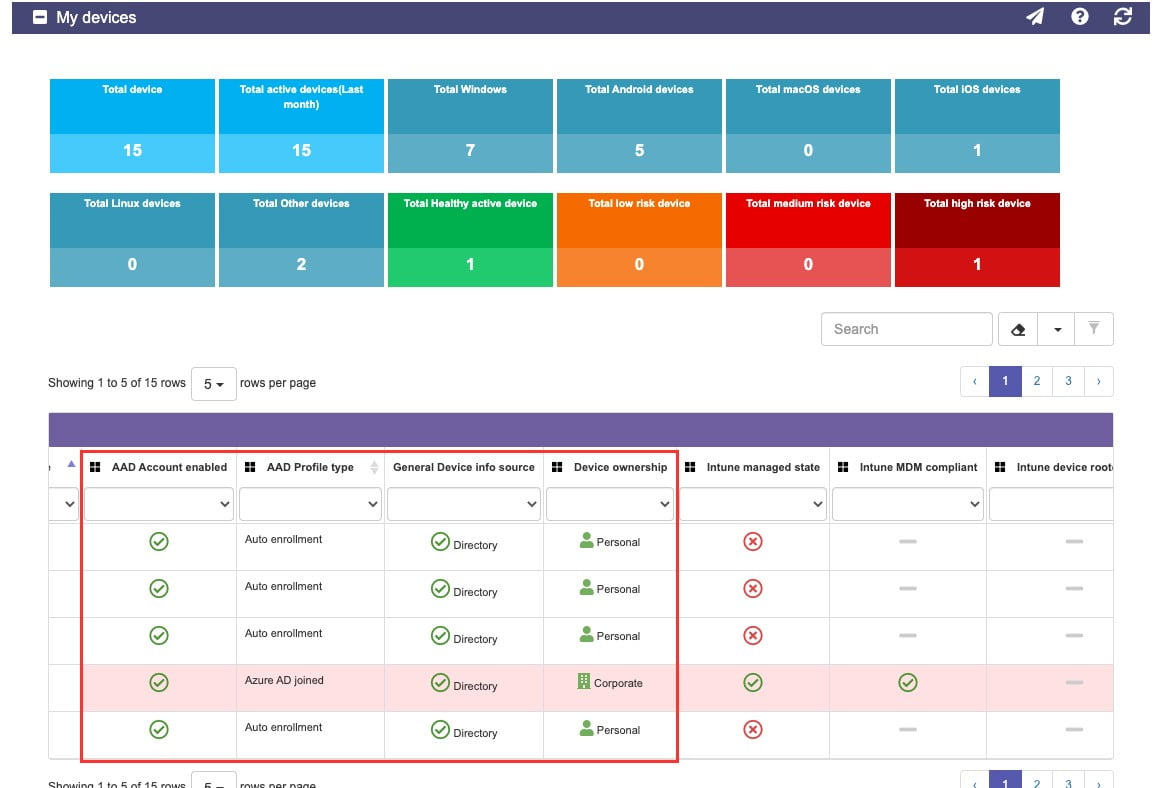
9- AAD Account Enabled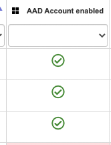 | Identifies if the device is enabled or disabled in Azure AD | If the device is enabled, it has some integration with Azure AD whichenablesusing SSO to access both SaaS and on-premises applications integrated with Azure AD in a transparent manner. | In lost and stolen devices scenarios, you can disable a device’s computer account to prevent it from accessingcorporate resources from that device. | Microsoft Link |
10- AAD Profile Type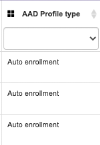 | This section provides more details about the integration type of the device with your organization policies | Represents the type of relationship that exists between the device and Azure Active Directory | Depending on your organizational corporate policy, you may be prevented from accessing applications from this device | Microsoft Link |
11 -General Device info source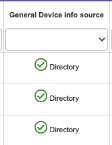 | This section lists if the device access to applications is based on sign-ins (typically loaner or shared devices not linked to your organization) or if they are based on an identification of this device within the organization’s device list | Watch out!!! Here you can check if any suspicious devices have been used to access your apps. Pay particular attention to the ones identified as “sign ins data” | Quickly identify if your credentials are being used in unrecognized devices, so that way you can take preventive actions, such as password change. | Microsoft Link |
12-Device Ownership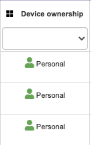 | Quickly identify the type of device used to access corporate resources | Based on the device enrollment method used to register the device in Azure AD, it is classified as Personal or Corporate | Depending onyour organization’scorporate security policy, you may be prevented fromaccessing applications from Personal devices. | Microsoft Link |
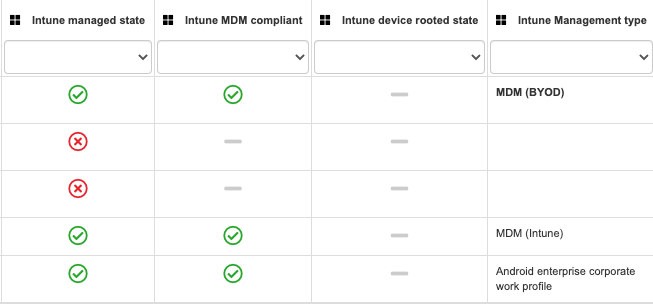
Corporate Compliance Status
Organizations can define a security configuration baseline and define when a device can be used to access corporate resources. The terms used in this evaluation are “Compliance” or “Compliant device”. The criteria set by your organization at the technical configuration level will define if the device is compliant or not.
| Functional name | Values | Explanation | Benefit | Technical Reference |
|---|---|---|---|---|
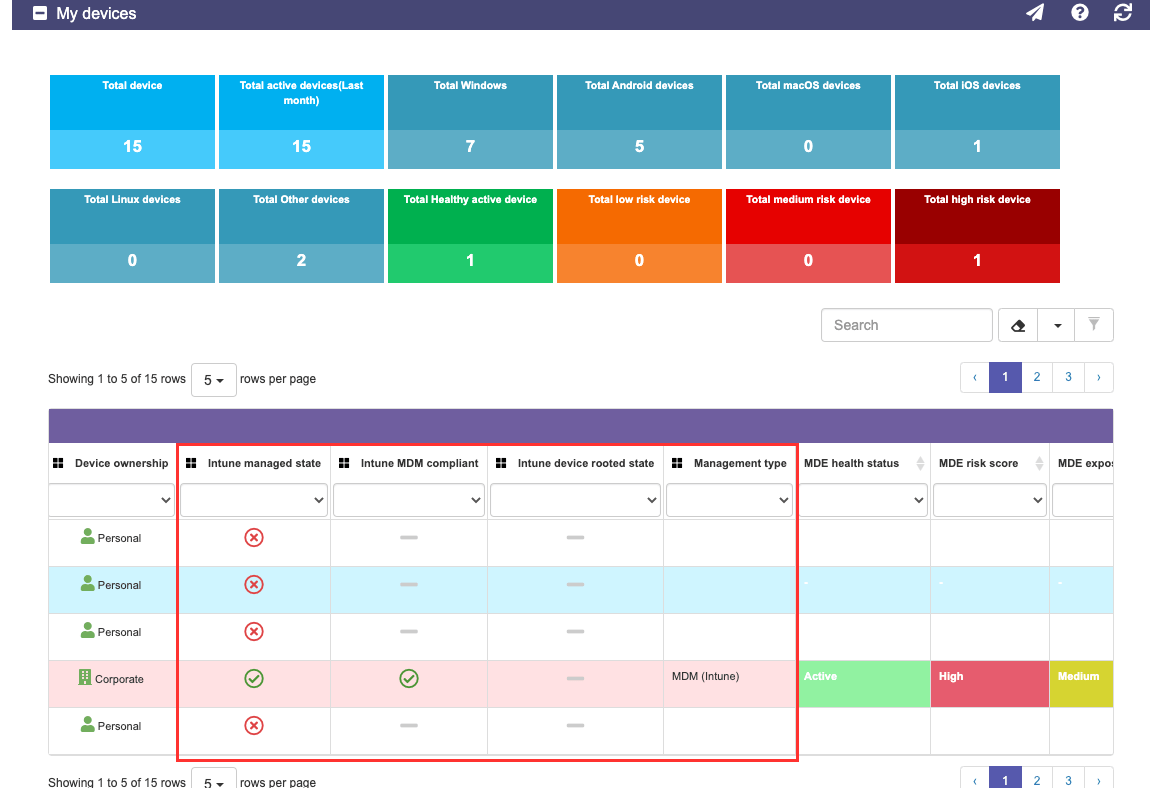
13- Intune Managed State | This section displays whether the device is managed by Intune or not | Make sure that if the device is corporate, to validate if that is needed. Assuming your organization is using Microsoft Intune, that should be the case | Get to know, in just one line, what could be the potential root of not getting updates, apps, and configuration settings deployed to your PC | Microsoft Link |
14- Intune MDM Compliant  | The value presented here is CRITICAL to confirm if the device satisfies the baseline configuration defined by your organization | Validate that your status gets to green! Your IT team can confirm what to do and will help get you there | Microsoft Link | |
15- Intune device rooted state | This setting is primarily for Android devices and validates if the base configuration has been tampered with. | Most organizations will not allow a device with this condition to get into the network as it may expose high risk. Ensure that if you face this situation, you back up your data, wipe or factory reset your device, and do not use it for corporate purposes | Quickly identify potentially risky devices, so that they can take the necessary corrective measures, such as factory reset | |
16 Intune Management Type | Get granular details about how your device is managed by your organization | Primarily for Android for enterprise-ready devices, Microsoft has provided additional controls, depending on enrollment type | Identify the type of enrollment used to register the device in MDM andquickly understand the types of restrictions that may be affecting the device | Microsoft Link |
Corporate Advanced Protection Status
Beyond defining what is “good” or “acceptable”, organizations have to be prepared to assume they have been attacked and should have the correct resources to effectively protect, detect, and respond to cyber-attacks. For that, we are pleased to share this new E-Visor Teams app integration with Microsoft Defender for EndPoint (MDE)
| Functional name | Values | Explanation | Benefit | Technical Reference |
|---|---|---|---|---|
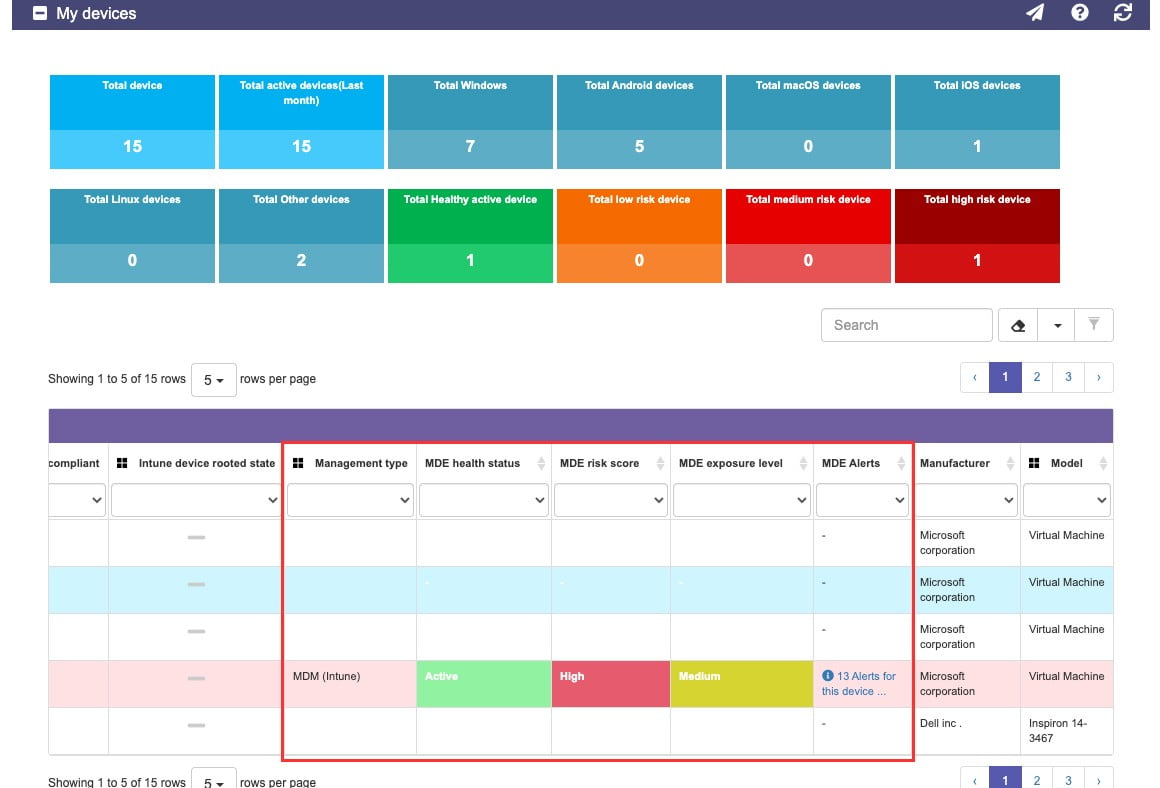
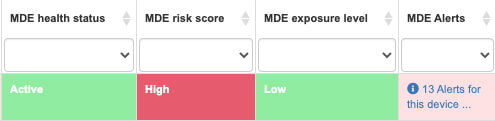
17-MDE Health Status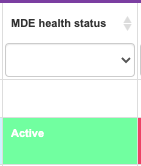 | This lets us know if the endpoint agent is connecting back to the service to validate the device and notify about any potential risks | Make sure if the device is corporate to validate if the service has been enabled on this device; collecting this information is critical to protect your device | Identify problems in the MDE sensors quickly to be able to escalate issues, solve problems, and reconnect with the MDE service and its protection. | Microsoft Link |
18-MDE Risk Score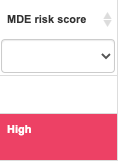 | Depending on your device conditions, your device will be assigned a risk score | Make sure you follow your organization’s guidance to respond to the risk reported by the system | For organizations using MDE, many of these issues can be inspected and remediated by MDE | Microsoft Link |
19-MDE Exposure Level | Going beyond the risk, there is an associated level of exposure | The considerations applied to define this value are related to: Threat characteristics Breach likelihood | This provides a holistic view of the level of exposure of a device, evaluating the different security parameters that require the attention of administrators and being able to take proactive actions more efficiently. | Microsoft Link |
20-MDE Alerts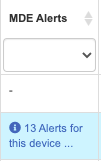 | Provides a number of alerts together with correlated incidents for the corresponding device | Make sure you can see potential exposures in this list: a USB drive you connected, a file you downloaded, a browser you navigated, and more. Some of this activity can trigger risks and MDE can list them here for you | Provides a quick view of the alerts associated with the device and thus be able to take action more quickly | Microsoft Link |
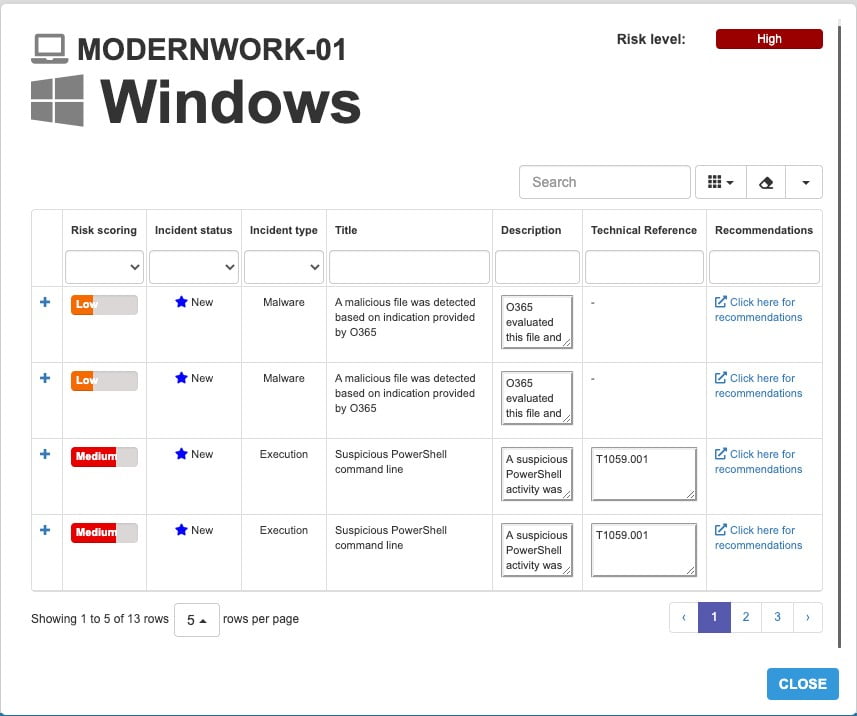
The great part of being able to see this in our app is that if you are concerned about a potentially impacted device and you received instructions to keep it offline, you can see your application virtually from every client that supports Microsoft Teams; even the Teams client from a browser can show these capabilities.
Summary
In this blog, we presented several of the E-Visor Teams App capabilities that provide an end-to-end #ZeroTrust view of device states along different workloads:
- Microsoft provides a comprehensive set of technologies to protect your devices:
- Windows 10 updates
- AAD device management benefits
- Intune compliance policies
- MDE advanced threat protection
- Give both your users and Cyber Team the support and information they need, with a simplified view of all that activity
Once again, consider the E-Visor Teams App your journey partner. Wherever you are at in your device protection strategy adoption and strategy, Let’s do it together!
Go ahead and download the E-Visor Teams App HERE and follow the steps to get the app configured HERE:
NOTE: Please contact us HERE to see how we can potentially facilitate E-Visor to a subset of your users, leveraging the Microsoft FastTrack Ready Program (LINK).
Before closing for today, do not miss our next blog post around simplified identity and access management for access to applications using AAD Identity Governance access with the E-Visor Teams App