
Insider Risk Management:
A key security component
As cyber-attacks continue to increase in frequency and sophistication, it is not enough for organizations to rely solely on traditional cybersecurity measures and controls. They must also address the risks associated with insiders – employees, contractors, business partners, and associates with legitimate access to systems and data. Thes stakeholders can pose a risk to the confidentiality, integrity, and availability of an organization’s sensitive information, critical assets, and intellectual property. Insider risk can be attribute-based (e.g., a person’s access, clearance, background, or behavior) or culture-based (e.g., a person’s attitude, loyalty, motivation, or awareness).
The 2023 Insider Threat Report by Cybersecurity Insiders states that 74% of organizations are at least moderately vulnerable to insider threats. And that’s understandable — in 2022, we saw lots of malicious insider attacks and leaks caused by user negligence. On the other hand, Microsoft Market Research shows us 93% of organizations are concerned about insider risks and 25% of all data breaches are due to insider activity.
[You may be interested: Webinar – Enhancing Compliance and Insider Risk Management]
Going beyond the statistics, let me tell you about some recent real cases:
- In May 2022, Yahoo’s senior research scientist Qian Sang stole confidential information about Yahoo’s AdLearn product. The compromised data included 570,000 files containing source code, backend architecture information, secret algorithms, and other intellectual property. Sang downloaded this data to his personal storage devices minutes after receiving a job offer from one of Yahoo’s competitors. After discovering the incident, Yahoo has since filed three charges against Sang, including for IP data theft, asserting that his actions exposed the company’s trade secrets, giving competitors a significant edge.
- In March 2022, a group of cybersecurity enthusiasts notified Pegasus Airlines that 6.5 terabytes of their sensitive data were exposed online. This happened because a system administrator had failed to properly configure the cloud environment that stored these records. The breach could have affected thousands of passengers and crew members. By exposing staff’s PII, the airline breached the Turkish Law on the Protection of Personal Data (LPPD), which can lead to a maximum fine of approximately $183,000.
- In February 2022, Toyota halted operations in Japan due to a data breach at their plastic parts supplier, Kojima. As Kojima had access to their manufacturing plants, Toyota had to shut down operations to safeguard their data. Because of this shutdown, the company couldn’t manufacture 13,000 cars, or 5% of their monthly production plan. The breach also impacted operations of Toyota’s subsidiaries, resulting in reduced production and affecting their bottom line. The attack happened right after Japan joined Western allies in imposing sanctions on Russia for the invasion of Ukraine, although it is uncertain whether the attack was related.
What is the correct and effective way to deal with insider risks?
Short Answer: Establish an Insider Risk Management (IRM) Strategy
Long answer: Establish an Insider Risk Management (IRM) strategy that establishes security controls found in the market and includes an exhaustive selection process, a methodology that enables the IRM strategy to be maintained over time, and proper management of internal security incidents.
Gartner defines insider risk management (IRM) as the tools and capabilities to measure, detect, and contain undesirable behavior of trusted accounts within the organization. In response to a recognized need to minimize the effects of unwanted activity within the organization and key partners, security and risk management leaders must mitigate risk. These tools monitor the behavior of employees, service partners, and key suppliers working inside the organization and evaluate whether behavior falls within expectations of role and corporate risk tolerance. Insider risk may involve errors, fraud, theft of confidential or commercially valuable information, or the sabotage of computer systems.
Some of the main benefits of implementing IRM include the following:
1. Proactive detection of insider threats
IRM enables organizations to establish baselines for normal user behavior, detect anomalous or suspicious activities, and investigate and remediate incidents before they become major breaches. For example, IRM can identify employees who are accessing sensitive data outside of their normal work hours, copying or deleting large amounts of data, or attempting to circumvent security controls.
2. Compliance with regulatory requirements
Many regulatory frameworks, such as HIPAA, PCI DSS, and GDPR, require organizations to implement controls to protect against insider threats and to monitor and audit user activity. IRM provides a systematic way to meet these requirements and to demonstrate compliance through reports, dashboards, and alerts.
3. Prevention of data leakage and intellectual property theft
Insiders can compromise sensitive data or intellectual property by intentionally or accidentally leaking or stealing it. IRM helps organizations to prevent data loss by monitoring and controlling access to sensitive information, detecting, and blocking unauthorized attempts to transfer or share data, and encrypting or masking data to prevent theft.
4. Minimization of reputational and financial damage
Insider breaches can have serious consequences for organizations, including loss of revenue, legal liabilities, and damage to reputation. By implementing IRM, organizations can minimize these risks by quickly detecting and responding to insider threats, reducing the impact of incidents, and preventing future incidents from occurring.
5. Enhancement of overall cybersecurity posture
IRM is not a standalone solution, but rather a complementary approach to traditional cybersecurity. By integrating IRM with other security controls, such as identity and access management, intrusion detection and prevention, and security information and event management, organizations can enhance their overall cybersecurity posture and mitigate a wide range of threats.
How do we at Synergy Advisors and Microsoft help you establish a comprehensive IRM strategy?
Synergy Advisors offers consulting services performed by expert architects and engineers to implement security technologies. We offer extensive experience executing Proof of Concepts, security assessments, production pilots, and complete implementations of Microsoft Purview Insider Risk Management and complimentary Microsoft 365 technologies.
Microsoft Purview Insider Risk Management is a compliance solution that helps minimize internal risks by enabling you to detect, investigate, and act on malicious and inadvertent activities in your organization. Insider risk policies from Microsoft Purview enable you to define the types of risks to identify and detect in your organization. Risk analysts in your organization can quickly take appropriate actions to make sure users are compliant with your organization’s information handling standards.
Manage and minimize risk in your organization starting with understanding the types of risks in your modern workplace and the behaviors that generate them. These can include a broad range of internal risks from users:
- Leaks of sensitive data and data spillage
- Confidentiality violations
- Intellectual property (IP) theft
- Fraud
- Insider trading
- Regulatory compliance violations
Complementing the IRM strategy with the power of E-Vigilant
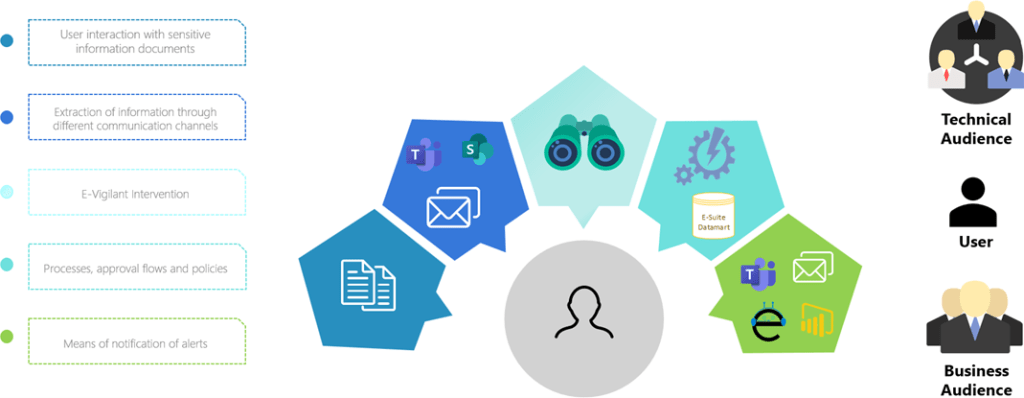
E-Vigilant is an advanced analytics and alerting solution, developed by Synergy Advisors- that resides inside Microsoft Teams and uses Microsoft solutions to COLLECT information from different sources (workloads), ALERT different audiences to different types of incidents, provide a comprehensive VIEW OF THE CYBERSECURITY ecosystem, and facilitate more EFFECTIVE MANAGEMENT. In this way, E-Vigilant complements insider risk management with advanced alerts that enable anticipating and responding to risks, while optimizing the management process when they become security incidents.
Main features
- Route DLP policy violation response to the actors with the requisite context to the violation, reducing false positives and surfacing high-impact cases.
- Alert end users to viruses and malware and recommend or automate next steps, reducing cyber risk and educating end users.
- Automate requests to view Microsoft Purview Information Protection-encrypted files according to robust business logic and response workflows.
- Resides within Microsoft Teams for quick access while you work.
- Detect the misuse of sensitive information.
- Manage and take action on quarantined e-mails with information about status, sender, reason of blocking, and more.
DLP-driven notifications
Webinar ‘Enhancing Compliance and Insider Risk Management with Microsoft Purview and Synergy Advisors E-Suite’
Microsoft and Synergy Advisors are offering an insightful webinar on insider risks and how to protect your environment. In this free webinar, we will discuss the various types of insider risks and which ones you should be most concerned about. You will also learn practical tips and strategies to minimize risks and protect your environment.
Some of the topics that we will cover in this free webinar:
- Lessons learn from real world insider risk cases.
- Top 5 Insider Risk gotchas in the market.
- Leveraging compliance capabilities to face insider risk challenges.
- DEMO: HOW TO LEAN ON ADVANCED INCIDENT MANAGEMENT CAPABILITIES FOR BETTER CONTROL AND VISIBILITY



