
Identity Threat Detection and Response – ITDR: The new approach to face identity-based attacks
In the process of digital transformation of our organizations, we leave behind a lot of information that becomes a footprint that is difficult to erase, which, together with multiple unprotected identities, constitute doors open to new attempts at cybernetic attacks. Controlling who accesses organizational information is a basic step in protecting it. We must have the ability to decide who has permission to access computing resources, how and when they access it, as well as for what purpose.
According the recently published 2023 Trends in Securing Digital Identities report from the Identity Defined Security Alliance (IDSA), 90% of organizations experienced at least one identity-related breach in the past year. This represents a 7.1% increase (84% of organizations reported an identity-related breach in 2022). Moreover, 68% of the organizations that incurred an Identity-based breach over the past year suffered a direct business impact as a result, the most significant of which being the cost associated with recovering from the breach.
These are some figures from the report that confirm the urgency of an identity protection strategy:
- 98% of identity and security professionals say the number of machine and human identities in their organizations is increasing, citing such top factors as the growing adoption of cloud applications (52%); the rise of remote working (50%); increased mobile device usage (44%) and an increase in third-party relationships (41%).
- 50% of the organizations surveyed cited remote work as one of the top leading factors driving the increase of number of identities.
- 62% of breaches in 2023 were caused by phishing, and it is the top cause of identity-related breaches for organizations.
- 37% of the organizations reported that inadequately managed privileges resulted in a breach, making it the second-leading cause of breaches in 2023.
- 30% of organizations say that poor password hygiene is another critical point that generates brute force attacks, including credential stuffing and password spraying attacks.
[You may be interested: PASSWORDLESS: The Future of Access and Identity Security]
Microsoft estimates that estimated that more than 80% of breaches can be attributed to identity-based attacks, and as more and more cybercrime groups join nation-state actors in executing these types of attacks, that number is only going to grow.
What are the benefits from protecting identities in organizations?
Cybercriminals constantly seek to steal personal information, such as usernames, passwords, social security numbers, and credit card details, to commit identity theft. Once they have access to this data, they can impersonate individuals and organizations, commit financial fraud, and cause significant impact to businesses.
Many online services require users to provide financial details for purchases or transactions. Protecting digital identities safeguards these financial assets from theft and unauthorized access.
Cybercriminals may try to gain access to various online accounts (e.g., email, social media, banking) by stealing digital identities. Taking control of these accounts allows attackers to conduct malicious activities or launch phishing attacks on the organization’s customers, providers, business partners, and employees.
Employees’ digital identities are often gateways to sensitive company data. Protecting their identities through strong authentication and security measures helps safeguard corporate information from data breaches.
Even within organizations, protecting digital identities can help prevent disgruntled employees or malicious insiders from causing damage by accessing sensitive data or systems.
When customers feel their digital identities are secure, they are more likely to engage in online services provided by companies.
A compromised digital identity could lead to unauthorized access to corporate platforms or other systems. Malicious activities carried out under stolen identity can damage an organization’s reputation and business relationships.
[You may be interested: IDENTITY GOVERNANCE: Intelligently govern identities and prevent security gaps]
Overall, by employing robust security practices and staying vigilant against potential threats, individuals and organizations can help safeguard themselves and their stakeholders from cyber risks. This is why two generally separate categories are joining today to create a new security approach that involves identity and access management (IAM), and extended detection and response (XDR).
How does Microsoft provide ITDR capabilities for comprehensive identity protection?
Microsoft sees ITDR as an integrated partnership between two critically important disciplines: IAM and XDR. IAM is a foundational element of any organization’s security strategy, providing a baseline for identity security and helping IT departments control what company resources users can and cannot access. By using IAM best practices such as strong authentication, Conditional Access, and identity governance, organizations can reduce their overall attack surface area while also providing the information and context needed to detect breaches.
XDR solutions are designed to deliver a holistic, simplified, and efficient approach to protect organizations against advanced attacks. These solutions correlate identity signals with telemetry from other domains like endpoints, cloud applications, and collaboration tools, giving security operations center (SOC) teams a more complete view of the cyberattack kill chain. With this enhanced visibility, they can more effectively investigate threats and provide automated remediation across multiple domains using vast sets of intelligence and built-in AI.
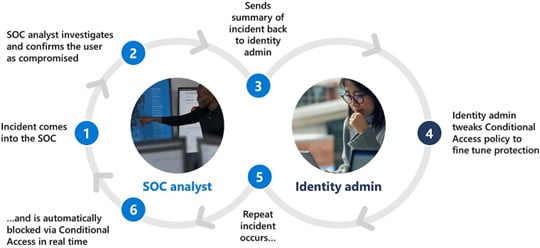
IAM and XDR each provide immense benefits to organizations, but when working together in concert, they provide a robust and comprehensive ITDR solution. Microsoft has built the following diagram that illustrates how SOC and identity teams can work together to remediate identity threats using a successful ITDR strategy:
An incident comes into the SOC
A SOC analyst investigates the incident and confirms the user is compromised.
The SOC analyst sends a summary of the incident to the identity admin.
The identity admin tweaks conditional access policies to fine tune protection.
Another similar incident comes into the SOC.
This time it is automatically blocked by conditional access in real time.
[You may be interested: BLOG: Right-size permissions across a multi-cloud environment]
Microsoft Identity Threat Detection and Response + Synergy Advisors services
As a six-time Leader in the Gartner® Magic Quadrant™ for Access Management, Microsoft provides comprehensive protection for all your identities and identity infrastructure by reinforcing your security boundary with complete, consistent protection and effective access management across your entire identity landscape. Through conditional access policies, comprehensive threat intelligence, and automated response capabilities provided by Microsoft, and Synergy Advisors consulting services, you can establish a robust identity protection strategy, and get some benefits such as:
The best-case scenario in any attack is that the bad actors are stopped before they can breach your security. Microsoft and Synergy Advisors recommend implement granular Conditional Access policies as a powerful first step in thwarting cybercriminals and keeping their organization safe, and protect non-human identities, whether applications, services, or containers. It’s critical to create more secure access policies and manage the lifecycles of different workload identities to prevent an attack.
IT and identity practitioners need to analyze relevant risk signals from across their unique landscape and enforce universal Conditional Access policies in real time. The deep integration of our IAM and XDR platforms helps organizations do just that. Leveraging insights from the more than 65 trillion signals daily across Microsoft’s ecosystem, Microsoft identity protection capabilities detect things like atypical travel, unfamiliar sign-in properties, and leaked credentials. These capabilities then assign each sign-in attempt a risk score, which in turn can trigger pre-defined remediation efforts or block access entirely until an administrator can review.
Effective breach detection and response face ever-evolving attack strategies and the impact of human error from multifactor authentication fatigue or social engineering attacks. To do this, you need powerful detections both at the identity level and across the entire cyber kill chain.
We help you harness the power of best-of-breed identity detections by integrating Microsoft’s identity security capabilities directly into the XDR platform so SOC teams can see identity alerts and data within the context of broader security incidents. By correlating identity data with signals from across other security domains, not only is each individual alert increasingly more accurate but analysts also gain unprecedented insight into the entirety of an attack and its progression.
The final piece of a successful ITDR strategy is the ability to stop in-progress attacks and limit lateral movement. Microsoft combines AI and machine learning into its security capabilities to help empower the SOC with intelligent automation that can disrupt attacks at machine speed. Analysts can confidently automate workflows and remediation tactics thanks to the high level of accuracy our correlated incidents provide. This effectively shifts the response time from hours or days to minutes or seconds.
How to start?
From Synergy Advisors we want to advise you on the fastest, easiest, and most effective way to start taking advantage of the ITDR capabilities offered by Microsoft solutions. Contact our Marketing team by emailing us at ww-marketing@synergyadvisors.biz to get a free session with one of our experts, who will guide you on how to start with Microsoft ITDR.
Synergy Advisors is a premier Microsoft Certified Partner that specializes in Microsoft 365, Identity, Azure B2C and B2B Collaboration, Security, Management, and Cloud technologies. We help you digitally transform and implement a more secure collaborative infrastructure, reduce your IT costs, and meet your regulatory requirements.



