- Data governance
- Apr 28
- Comments (0)
The data governance pill for the headache of protecting sensitive information
Year 2022, the pandemic seems to be close to ending, at least in some countries of the world and although we are glad that this happens, we can not forget all the challenges that it has left us in terms of technology, productivity and cybersecurity. As we mentioned in our previous article “Effective management of sensitive information”, the pandemic forced companies to accelerate their digital transformation, if they did not want to disappear in a world in which everything has been virtualized. Companies of all sizes and industries face, now more than ever, a scenario in which their employees are in constant contact with multiple information channels without adequate control of the data that circulates through them, or security controls that enable sensitive files to be managed correctly; on the other hand, practices such as BYOD (Bring Your Own Device) and remote work generate security gaps that, with a lack of good security practices and awareness for the internal user, are the perfect mix to convert the management of the information from a simple headache to a terrible migraine
So, since the user is the weakest link in the security chain, am I condemned to suffer threats to the data?
The answer is no!
But first, we must be aware that threats to confidential information continue to be a challenge with a tendency to continue growing, especially with remote work that is already part of the preferred modality of many companies. The “2022 Thales Data Threat Report” indicates that 79% of companies are concerned about possible security risks, due to the increase in remote work and 22% of companies say that more than 60% of their data has been encrypted with malicious purposes. In addition, 28% of senior leaders indicate that they would not entrust their personal data to their organization; mistrust comes from both sides.
So, although the landscape is challenging, both for users and for organizations, it is possible to establish a protection strategy that enables companies to mitigate the risks associated with data security. To begin, it is important to note that threats to data and the loss or misuse of sensitive information are primarily due to 2 factors:
- The human factor: The user, whether he is an employee, customer, supplier, or any other, is not receiving the necessary awareness to be educated in good security practices and frequently falls for external threats of social engineering such as phishing, smishing, tailgating, impersonation, among others, through which they put sensitive information, both personal and company, at risk.
- Lack of data control: Many organizations are not aware of the number of files, the type of data and the sensitive information that travels through their information channels; likewise they have no control over who is accessing the information, what for, from what device, on what date and time, which in turn makes it difficult to protect data and establish effective security policies.
This is where establishing a strategy that allows data to be governed effectively and, at the same time, generates insights that promote the protection and control of sensitive data, plays an essential role: a ‘Data Governance’ strategy; let’s review the concept.
[You may be interested in: Effective management of Sensitive Information]
Data Governance
Microsoft defines ‘data governance’ as the collection of processes, policies, roles, metrics, and standards that ensures an effective and efficient use of information. This also helps establish data management processes that keep organizations’ data secured, private, accurate, and usable throughout the data lifecycle. In this way, a robust data governance strategy enables companies to always be aware of who has control or is accessing their data, which is crucial for business growth, for better decision-making, managing risks, reducing costs, and meet business objectives.
Headache starts to go away
Even if the information is at rest, the data is dynamic with multiple servers and locations, multiple access vectors and actors, multiple copies of data, and multiple administrators., which keeps complex to control it. Discovering what type of data, where it is located, and who accesses it in the organization is the most effective first step to develop a protection and mitigation strategy. So, going back to the question mentioned earlier, we can say that a data governance strategy works like that pill that helps to gradually eliminate the headache that comes from not knowing how to manage, discover and protect information. sensitive.
At this point where we have concluded that data governance is the best answer to the questions “how to correctly manage and control data?” and “how to protect sensitive information at the same time?”, the next step is to begin the process of implementing data governance strategy.
[Infographic: How to start approaching a data governance strategy]
In our previous article, we mentioned that Synergy Advisors has developed an assessment and scanning offer for data at rest using the E-Inspector tool, a solution created for automated discovery, audit, and protection of stored sensitive information. To continue the protection journey through a data governance strategy, Synergy Advisors’ cybersecurity experts team has developed the next level of protection, which begins with the E-Suite Discovery Offering (EDO): assessments and scans carried out on organizations’ file storage locations, enabling them to proactively discover, protect, and manage sensitive information within the organization. These offerings combine advanced capabilities of data governance and information protection, enabling to create a robust, comprehensive strategy that protects end-to-end data.
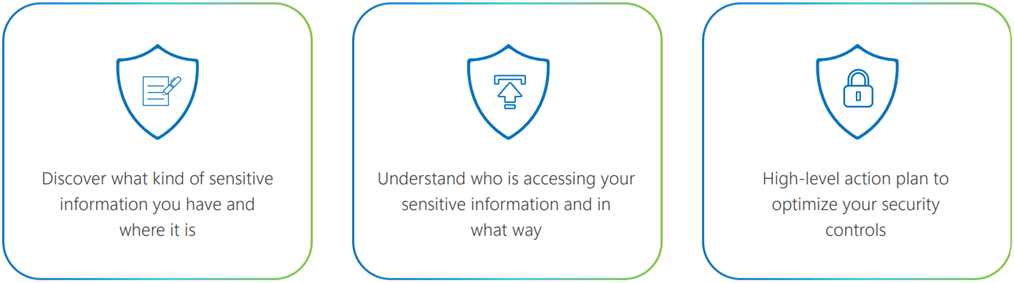
How do Synergy Advisors data governance offerings work?
These are detailed assessments, scannings, and findings that allow building an inventory and analysis of data at rest, in order to establish a mitigation and data protection plan, based on 3 possible scenarios, according to the unique needs of each company:
· EDO Scenario 1 | Scanning for unstructured data: Data that do not have a predefined model or are not organized in some way, such as photographies, text documents, videos, among others.
· EDO Scenario 2 | Scanning for structured data: Data that have a defined model or come from a given field of a record, such as web crawlings, data bases, shared prices, and others.
· EDO Plus | Scanning for both unstructured and structured data: Comprehensive scanning for both unstructured and structured files in multiple locations.
Beyond protecting sensitive data, these assessments have the main goal of enabling organizations to accomplish business, regulatory, and compliance requirements, by creating a data lifecycle process in which questions such as “who created the file?”, “how long time ago?”, “are there duplicates?”, “who has access to them and who has used them?”, among others. Likewise, it is possible to determine the content type, discovering the sensitive data, the level of sensitivity and their classification. In this way, it is possible to create an effective risk mitigation plan.
What do companies get after executing the assessment?
· Action plan roadmap: Co-creation of an expert plan for organizations’ specific scenarios, potential impact analysis, and mitigation steps.
· File inventory: Complete file inventory and data metrics through Synergy Advisors’ E-Visor tool, and Power BI exportable reports, with recommended MIP label and sensitive data found.
To finish this article, we share the guide to get started with the data governance strategy and a more detailed explanation of how these offers work, here.
Are you ready to start?



