Enterprise automated discovery, audit, and protection of stored sensitive information
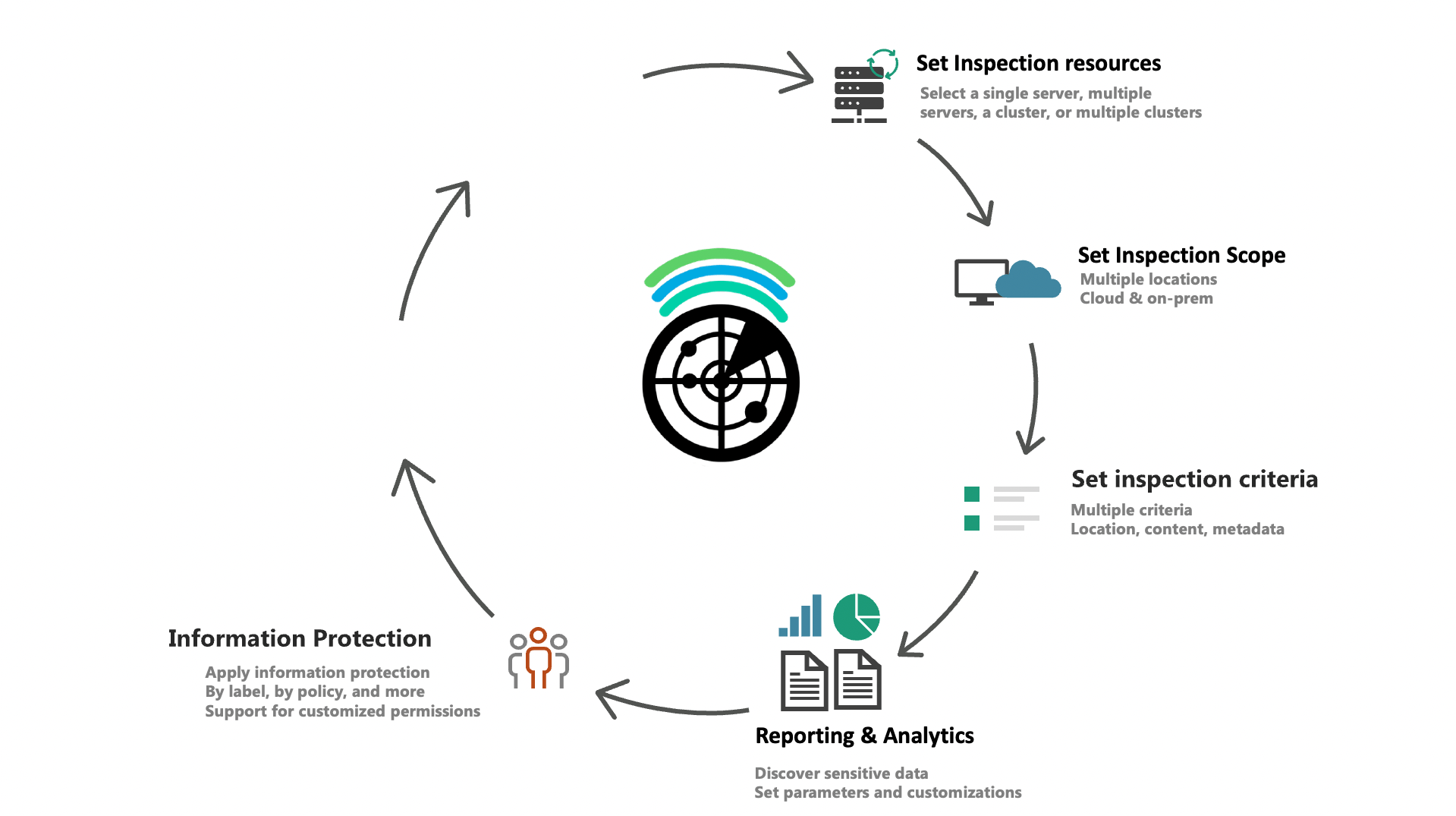
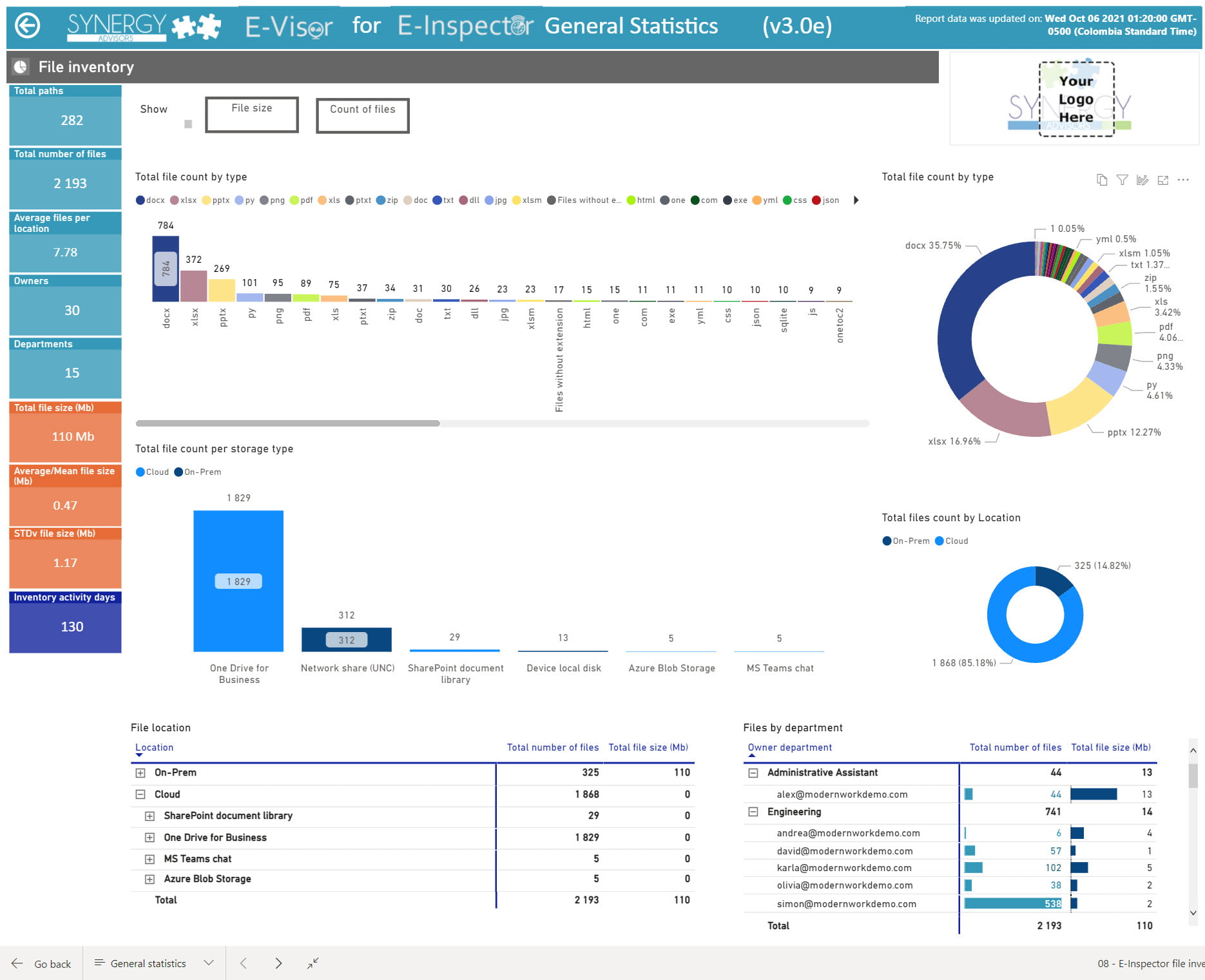
Discovery and Inventory
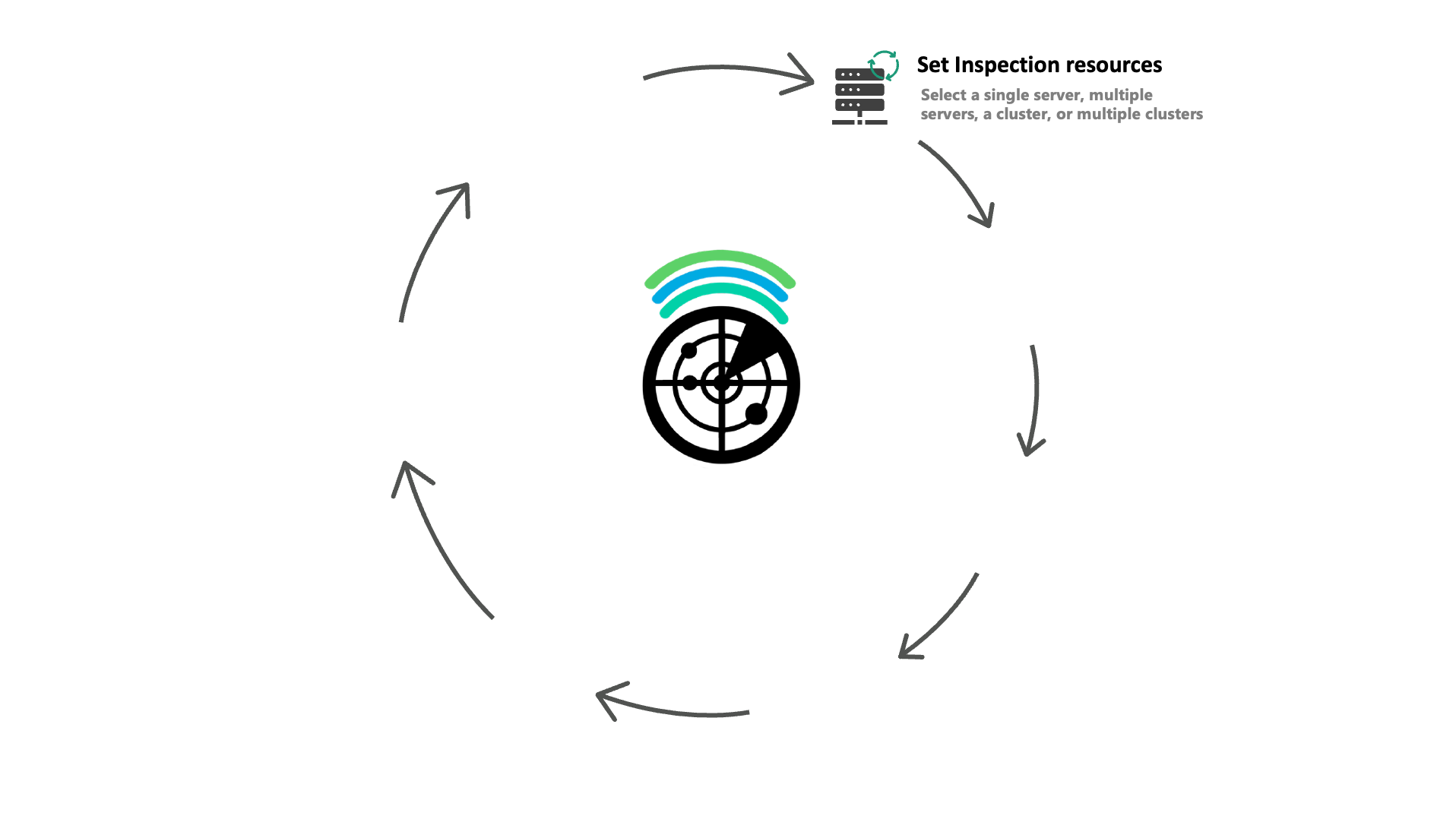
Find sensitive information by file content, metadata, and more
- Business-driven, efficient, and dynamic inventory
- Discover sensitive files by information type
- See where and when files are accessed and by who
- Based on day-to-day access and share content scenarios
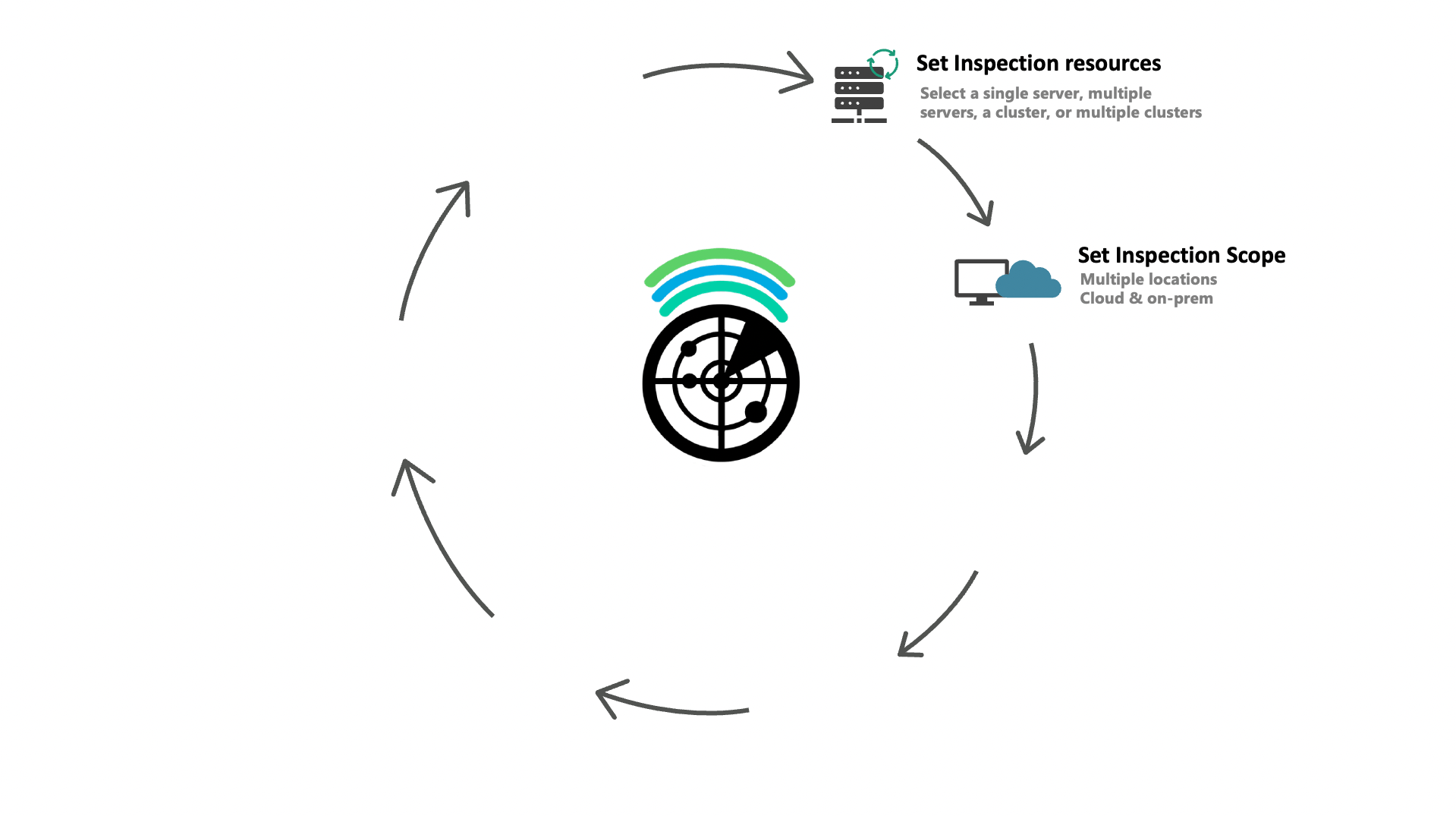
Granularity
Discover and protect multiple files based on specific data attributes
- Scan by multiple filters such as location, type of information, users, and much more.
- Filter reports quickly, and at multiple levels, saving the equivalent of 10,000+ manual DB queries
- Apply information protection with flexible, information-driven, rich policies
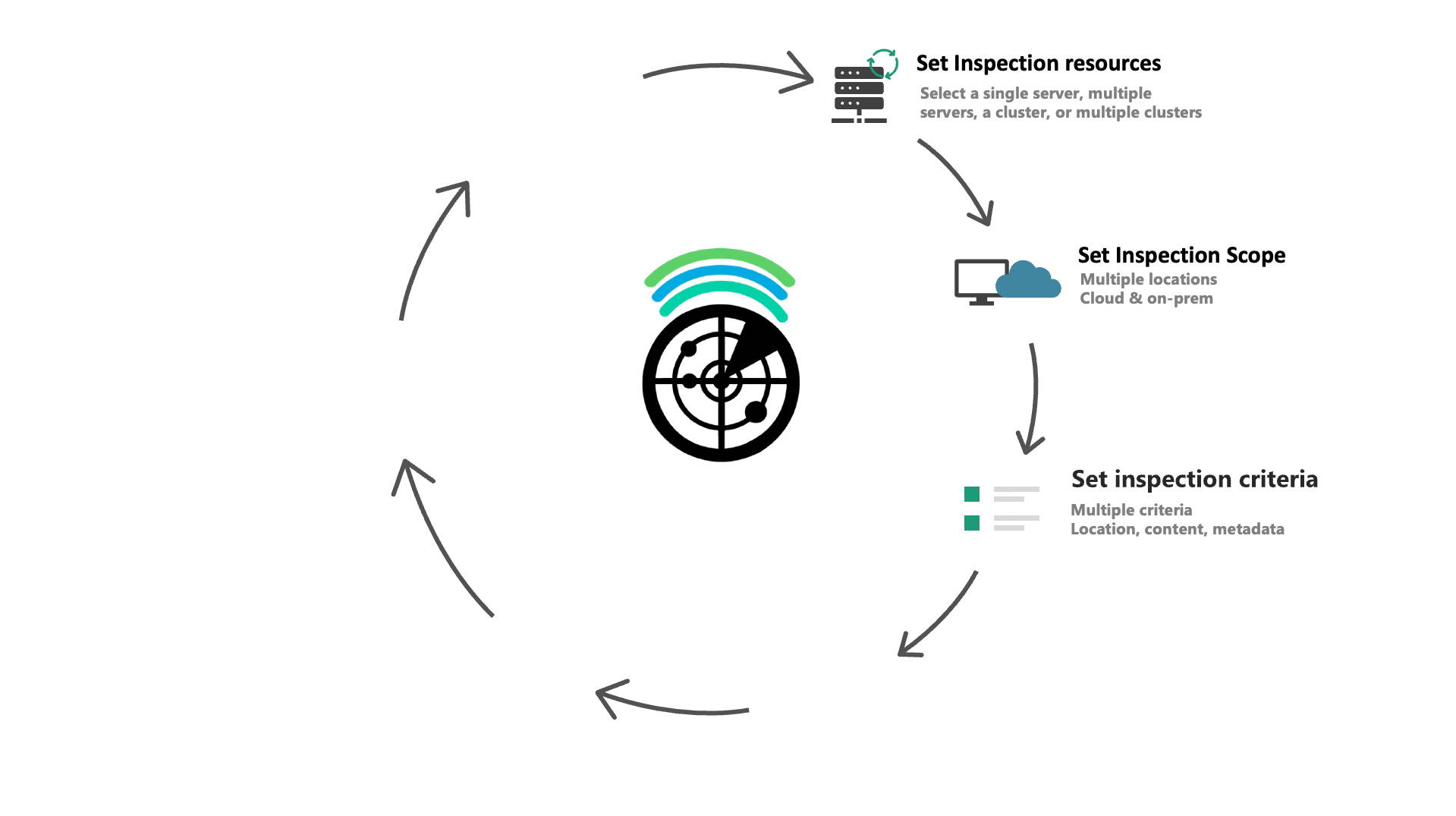
Optimization
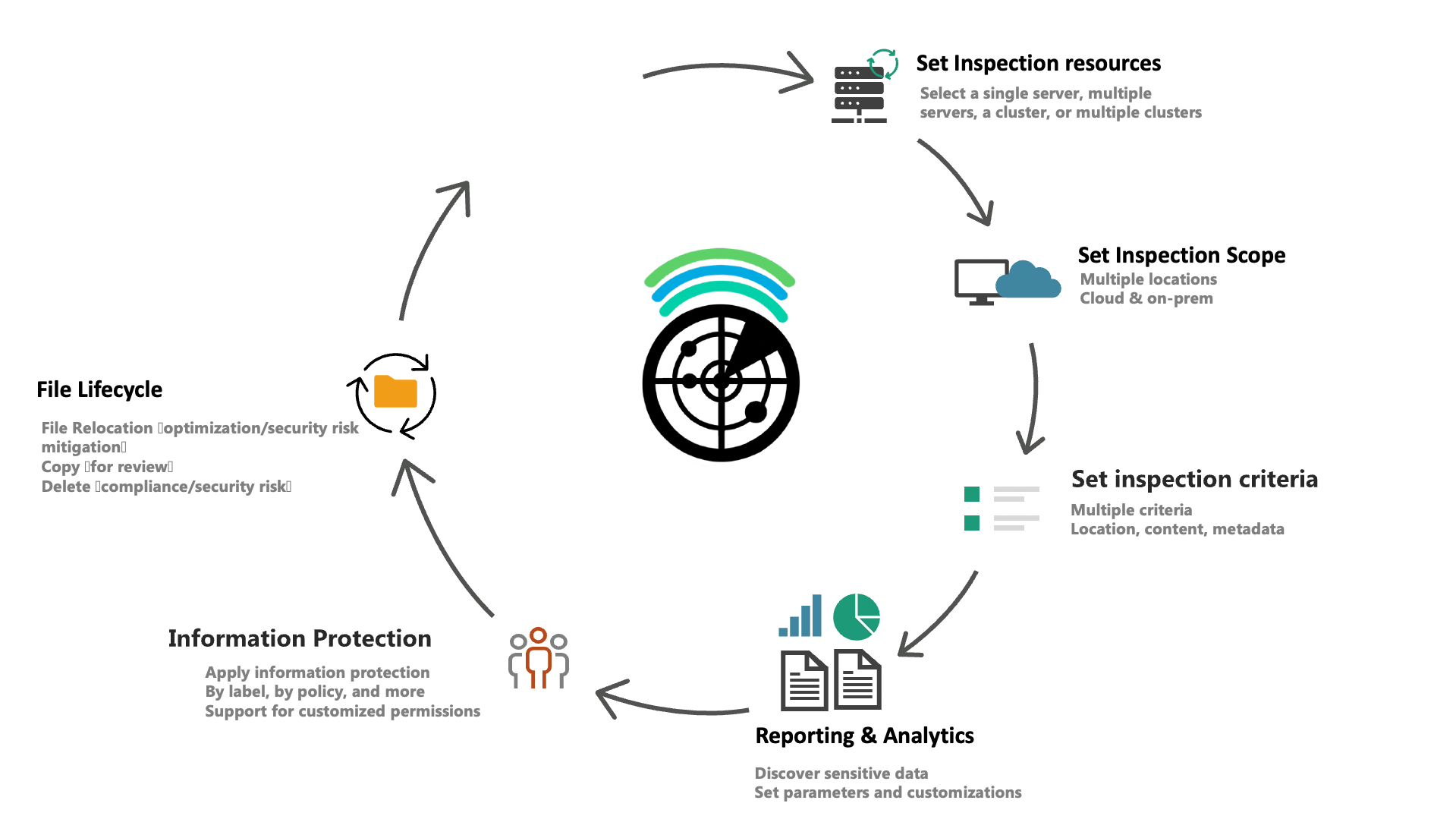
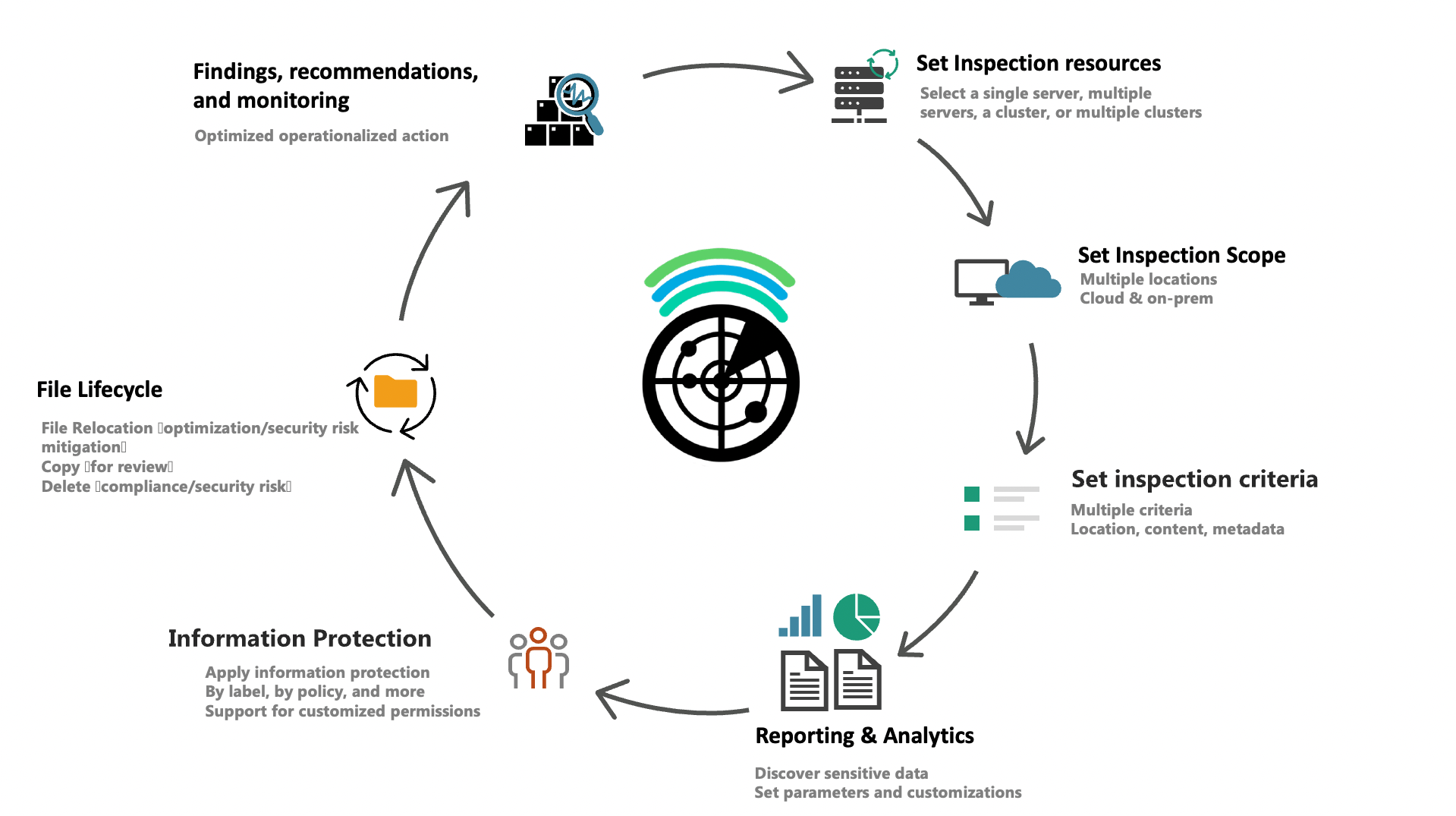
Dynamically apply file lifecycle actions
- Bulk copy, move, and delete actions for files, based on multiple parameters
- Manage owners, change file permissions, and apply or remove encryption to files
- Bulk label and classify information based on several scopes
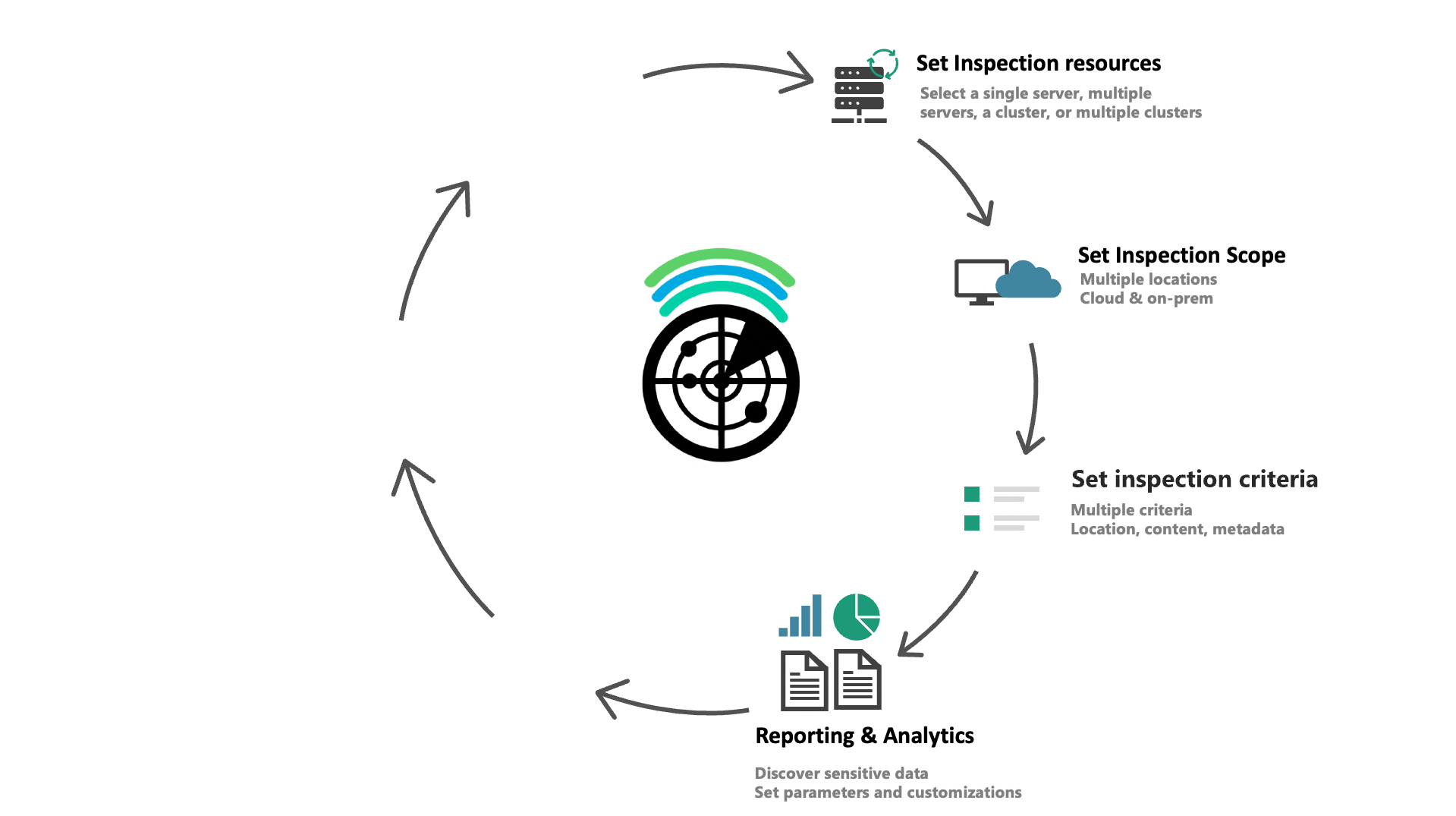
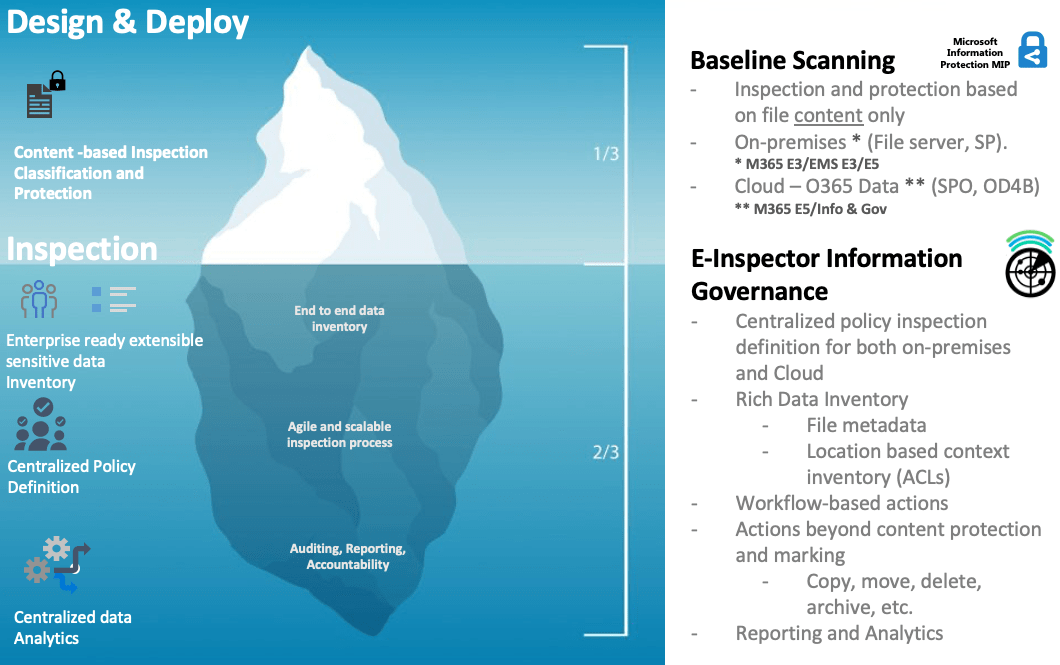
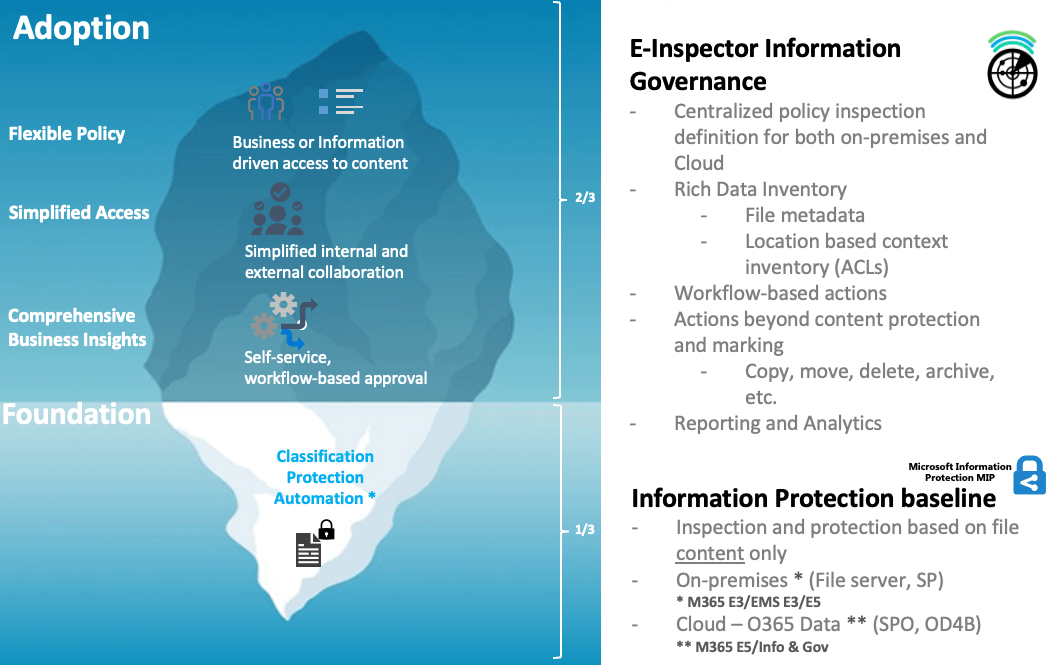
Some of challenges solved by E-Inspector
- Identify what type of data (e.g., credit card numbers, personal data, etc.), where it is stored and who is accessing it
- Understand and monitor the types of information stored in specific repositories (SharePoint Online, SharePoint Server, Teams, OneDrive, on-premises, and more)
- Migrate files to the cloud excluding specific data
- Change document permissions when the user is no longer part of the organization
- Encrypt files by data type, area, users and specific location
E-Inspector implementation
Turning over the iceberg
Day-to-day scenarios
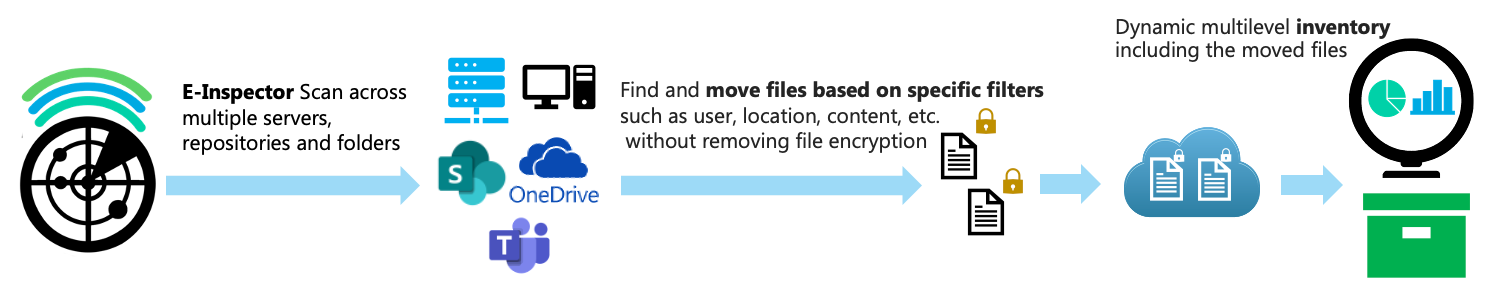
Business-Driven multilevel dynamic inventory
Scenario
- Identify what type of data is currently stored in the HR and finance repositories.
- Find documents containing sensitive information such as credit card numbers, personal data, and social security numbers.
- Build a risk mitigation plan for data leakage.
Impact
- Inefficient process with potential for human risks.
- Not an automated process.
- Demanding in effort and time
Solution
- E-Inspector automates the process.
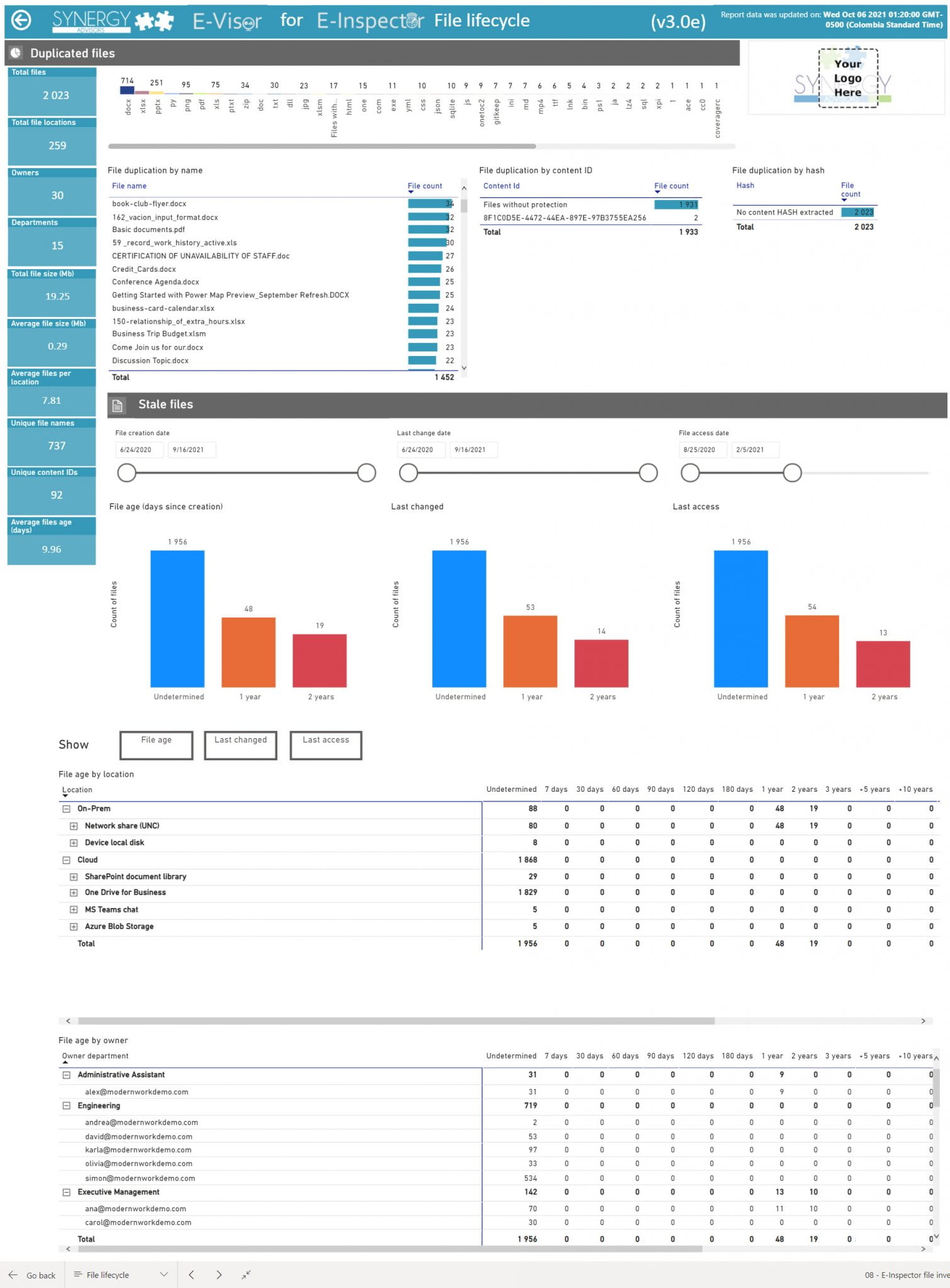
- Detailed inventory (including document characteristics and content).
- Correlation of who uses the document(s) (user/department).

Scenario
- Finance needs to identify which documents contain credit cards in a specified repository.
- Implement encryption on these documents.
- Inefficient process with potential human risks.
- Not an automated process.
- Demanding in effort and time.
- E-Inspector applies the required encryption according to the content of the document.
- E-Inspector streamlines and automates the process.
- Detailed inventory of the files.

Scenario
- Alex is no longer part of the organization.
- Find all of Alex’s documents.
- Assign all of Alex’s documents to Carol.
Impact
Exposure to a possible risk and effort to find that information.
Manual process may result in omission of documents.
Unprotected documents, possible leakage of information.
Solution
E-Inspector identifies all of Alex’s documents.
It grants permissions to Carol automatically.
Does not remove encryption on documents.
Detailed inventory.

Escenario
El cliente quiere migrar los repositorios de archivos de los servidores locales heredados a SharePoint Online; sin embargo, el cliente no quiere almacenar ciertos tipos de información en la nube.
Impact
Exposición a posibles riesgos. Complejidad y esfuerzo para encontrar esa información.
El proceso manual puede dar lugar a la omisión de documentos.
Solution
Proceso automatizado.
No elimina el cifrado de los documentos.
Inventario detallado.
©2020 Synergy Advisors LLC. ALL RIGHTS RESERVED.