
Scanning and protection for unstructured data at rest
The reality of today’s business
- Users have access to multiple communication channels
- Users access data from multiple, and possibly unprotected, devices
- Uncontrolled access to sensitive information
- Lack of security controls to properly manage files
- Lack of good practices in the protection of information
- Lack of analytics for information security decision-making
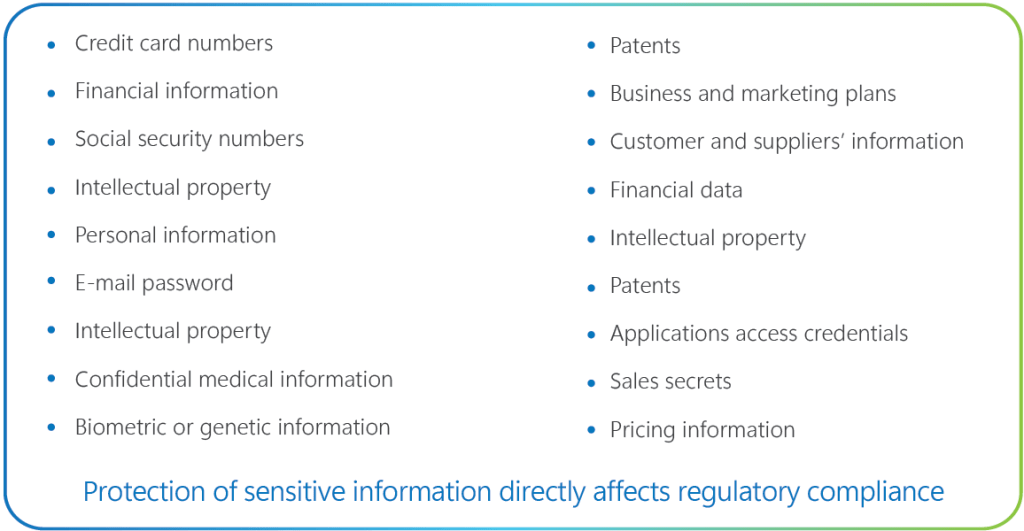
Sensitive data is everywhere
EDO Scenario 1: Assessment and scanning for unstructured data at rest
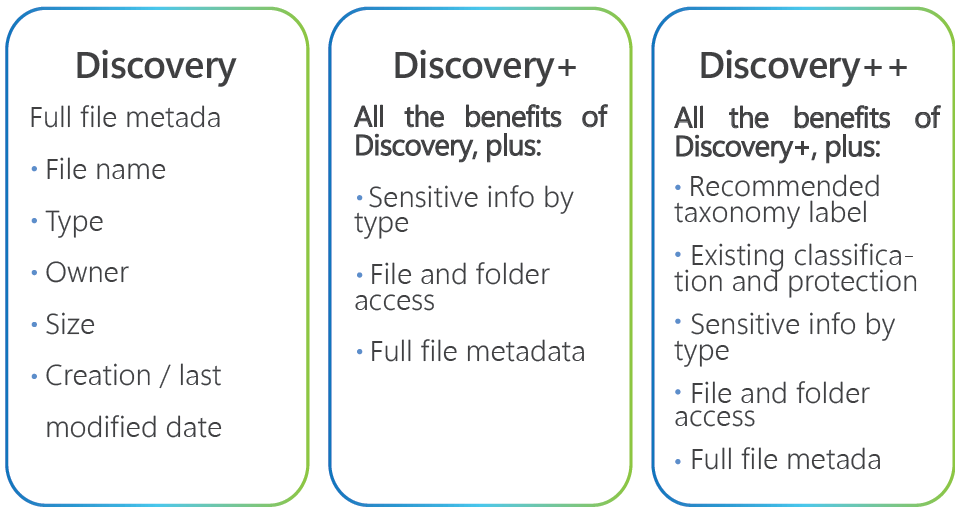
Synergy Advisors brings three options in the “Discovery” stage to satisfy your unique needs, according to the complexity of your current sensitive information management:Prepare for file migrations
- Identify files by sensitive info type
- Discover stale and large file
Prepare for data at rest initiative
- Recommended label by file contents
- See labeling impact before you begin
Access repositories
- Breakdown by size, owner, type, and more
Scope of the offering
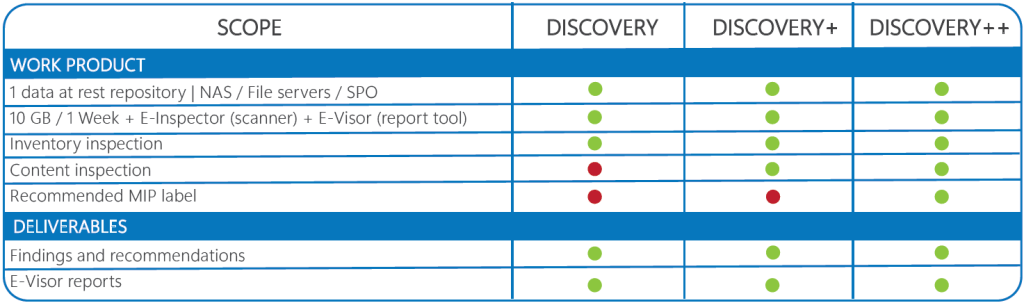
Out of scope
- Additional data repositories
- Customer data modifications
- Detailed remediation to potential findings
What do you need to start protecting your sensitive information?
Quick and easy Fast and thrifty. No premium subscriptions required.
- Azure [Pass] + Enterprise Mobility + Security E5
- Microsoft 365 E5 or M365 Information Protection and Governance
What will you receive after the assessment?
- Action plan roadmap: Co-creation of an expert plan for your specific scenarios, potential impact analysis, and mitigation steps.
- File inventory: Complete file inventory and data metrics through E-Visor and Power BI exportable reports, with recommended MIP label and sensitive data found.